Securing distributed techniques is a fancy problem as a result of variety and scale of elements concerned. With a number of companies interacting throughout doubtlessly unsecured networks, the chance of unauthorized entry and information breaches will increase considerably. This text explores a sensible strategy to securing distributed techniques utilizing an open-source venture. The venture demonstrates methods to combine a number of safety mechanisms and applied sciences to sort out widespread safety challenges similar to authentication, authorization, and safe communication.
Understanding Safety Challenges in Distributed Methods
Distributed techniques contain a number of companies or microservices that should talk securely throughout a community. Key safety challenges in such architectures embody:
- Safe communication: Making certain that information transmitted between companies is encrypted and protected from eavesdropping or tampering
- Authentication: Verifying the identities of customers and companies to forestall unauthorized entry
- Authorization: Controlling what authenticated customers and companies are allowed to do, based mostly on their roles and permissions
- Coverage enforcement: Implementing fine-grained entry controls and insurance policies that govern service-to-service and consumer interactions
- Certificates administration: Managing digital certificates for encrypting information and establishing belief between companies
This open-source venture addresses these challenges utilizing a number of built-in applied sciences and options.
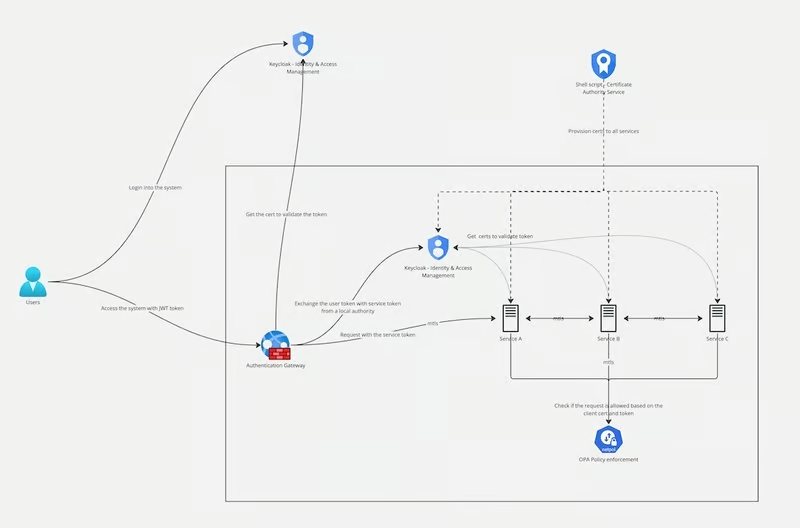
Undertaking Setup and Configuration
The venture begins with organising a safe setting utilizing shell scripts and Docker. The setup entails provisioning digital certificates and beginning the mandatory companies to make sure all elements are prepared for safe communication.
Steps to Set Up the Setting
1. Provisioning Certificates
The venture makes use of a shell script (provisioning.sh) to simulate a Certificates Authority (CA) and generate the mandatory certificates for the companies.
./provisioning.sh
2. Launching Providers
Docker Compose is used to start out all companies outlined within the venture, guaranteeing they’re configured accurately for safe operation.
docker-compose up
3. Testing Service-to-Service Communication
To validate service-to-service communication utilizing certificates and JWT tokens, the test_services.sh script is supplied. This script demonstrates how completely different companies work together securely utilizing their assigned certificates.
Fixing Safety Challenges in Distributed Methods
The venture integrates a number of key applied sciences to handle the first safety challenges talked about earlier. This is how every problem is tackled:
1. Safe Communication With Mutual TLS (mTLS)
Problem
In a distributed system, companies should talk securely to forestall unauthorized entry and information breaches.
Resolution
The venture makes use of Mutual TLS (mTLS) to safe communication between companies. mTLS ensures that each the consumer and server authenticate one another utilizing their respective certificates. This mutual authentication prevents unauthorized companies from speaking with legit companies.
Implementation
Nginx is configured as a reverse proxy to deal with mTLS. It requires each consumer and server certificates for establishing a safe connection, guaranteeing that information transmitted between companies stays confidential and tamper-proof.
2. Authentication With Keycloak
Problem
Correctly authenticating customers and companies is important to forestall unauthorized entry.
Resolution
The venture leverages Keycloak, an open-source id and entry administration answer, to handle authentication. Keycloak helps a number of authentication strategies, together with OpenID Join and consumer credentials, making it appropriate for each consumer and repair authentication.
- Consumer Authentication:
Customers are authenticated utilizing OpenID Join. Keycloak is configured with a consumer (appTest-login-client) that handles consumer authentication flows, together with login, token issuance, and callback dealing with. - Service Authentication:
For service-to-service authentication, the venture makes use of a Keycloak consumer (client_credentials-test) configured for the consumer credentials grant kind. This technique is right for authenticating companies with out consumer intervention.
Authentication Circulation Instance
- Customers navigate to the login web page.
- After profitable login, Keycloak redirects the consumer to a callback web page with an authorization code.
- The authorization code is then exchanged for a JWT token, which is used for subsequent requests. The
authn.jsfile within thenginx/njslisting offers an in depth implementation of this movement.
Service Authentication Instance Utilizing Shopper Credentials
curl -X POST "http://localhost:9000/realms/tenantA/protocol/openid-connect/token"
-H "Content-Type: application/x-www-form-urlencoded"
-d "grant_type=client_credentials"
-d "client_id=client_credentials-test"
-d "client_secret=your-client-secret-here"
3. Consumer Authorization With Open Coverage Agent (OPA) and JWT
Problem
Imposing fine-grained entry controls to make sure that authenticated customers and companies solely have entry to approved sources
Resolution
The venture makes use of a mix of Open Coverage Agent (OPA) and JWT tokens to implement authorization insurance policies. The venture demostrate three completely different methods for JWT validation to make sure strong safety:
- Retrieving certificates from Keycloak: Fetches the certificates dynamically from Keycloak to validate the token.
- Utilizing x5t (Thumbprint): Makes use of the thumbprint embedded within the token to retrieve the general public key from a neighborhood belief retailer.
- Embedded certificates validation: Validates the token utilizing an embedded certificates, guaranteeing the certificates is validated in opposition to a trusted Certificates Authority (CA).
Seek advice from the nginx/njs/token.js file for the detailed implementation of those methods.
4. Coverage Enforcement With Open Coverage Agent (OPA)
Problem
Implementing dynamic and versatile entry management insurance policies for each companies and customers
Resolution
OPA is used to implement fine-grained insurance policies for entry management. Insurance policies are written in a declarative language (Rego) and saved within the opa/ listing. These insurance policies dictate the situations below which companies can talk and customers can entry sources, guaranteeing that entry controls are constantly utilized throughout the system.
5. Certificates Administration
Problem
Managing digital certificates for companies to determine belief and safe communications
Resolution:
The venture features a strong certificates administration system. A shell script (provisioning.sh) is used to simulate a Certificates Authority (CA) and generate certificates for every service. This strategy simplifies certificates administration and ensures that every one companies have the mandatory credentials for safe communication.
We additionally added an endpoint to replace the service certificates with out the necessity of nginx restart.
curl --insecure https://localhost/certs --cert certificates/gen/serviceA/consumer.crt --key certificates/gen/serviceA/consumer.key -F cert=@certificates/gen/serviceA/consumer.crt -F key=@certificates/gen/serviceA/consumer.keyConclusion
Constructing a safe distributed system requires cautious consideration of assorted safety points, together with safe communication, authentication, authorization, coverage enforcement, and certificates administration. This open-source venture offers a complete instance of methods to combine a number of safety mechanisms to handle these challenges successfully.
By following the setup and configurations demonstrated on this venture, builders can leverage mutual TLS, Keycloak, Open Coverage Agent, and Nginx to construct a strong safety structure. These applied sciences, when mixed, present a powerful basis for securing distributed techniques in opposition to a variety of threats, guaranteeing each information safety and safe entry management.

