The introduction of software program has made exceptional adjustments to how enterprise is performed. “Back then,” individuals would meet in individual, and most corporations used guide strategies, which weren’t scalable. Software program has modified the sport, and net functions are important for a enterprise’s success. Software program is how clients work together with companies, share their information, and obtain items and companies.
Software program-as-a-service (SaaS) has turn into a large business, caring for internet hosting companies utilized by clients by upgrading, scaling, and securing buyer information. With the large proliferation of SaaS companies, many are utilizing AWS, and safety is an enormous concern. Malicious actors search to steal buyer information or DDoS-ing the service to stop reputable clients from accessing the web site.
It’s 2024, and we’re nonetheless scuffling with the safety of hosted net companies. The Mirai botnet has been one of the crucial profitable botnets, taking down large corporations and creating variants of botnet code. Defending net functions is a non-trivial drawback, and the urgency of securing them at varied levels of the structure can’t be overstated.
Downside
Internet functions face many issues, every various and complicated in its personal proper. This implies our firewall guidelines have to be created individually to deal with these issues.
DDoS Assaults
These assaults goal to inundate net functions by sending them extreme site visitors from quite a few compromised machines, rendering companies inaccessible to licensed customers.
Credit: Rustam, F., Mushtaq, M., Hamza, A., Farooq, M., Jurcut, A., & Ashraf, I. (2022). Denial of Service Assault Classification Utilizing Machine Studying with Multi-Options. Electronics, 11(22), 3817.
SQL Injection
Attackers use software code weaknesses to inject dangerous SQL statements, which might result in unauthorized entry to necessary information.
Credit: Alghawazi, M., Alghazzawi, D., & Alarifi, S. (2023). Deep studying structure for detecting SQL injection assaults primarily based on RNN autoencoder mannequin. Arithmetic, 11(15), 3286.
Cross-Web site Scripting
Malicious code is inserted into dependable web sites, working in customers’ browsers and presumably stealing helpful data or taking management of person periods.
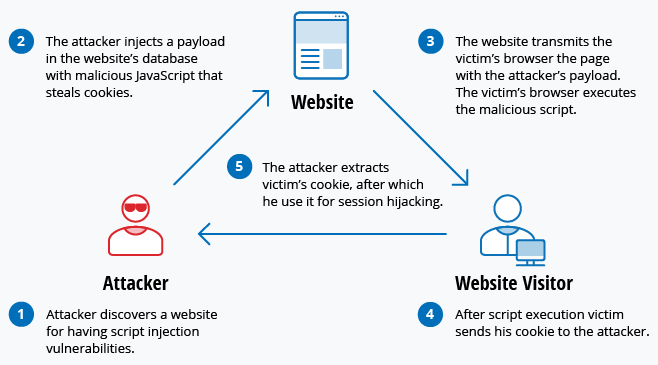
Credit: Mwila, Okay. A. (2020). An evaluation of cyber assaults preparedness technique for private and non-private sectors in Zambia (Doctoral dissertation, The College of Zambia).
Cross-Web site Request Forgery
Attackers deceive customers into finishing up unintended actions on an online software whereas they’re logged in.
Credit score: Cross-Web site Request Forgery (CSRF) Christopher Makarem by Christopher Makarem in IOCSCAN
Script Kiddies
Bots are used to mechanically scrape content material, perform credential-stuffing assaults, or interact in different malicious actions.
Credit: What Is Credential Stuffing and How Can It Impression You? By Dashlane
The results of such assaults could possibly be vital and will end in compromised information, monetary loss, service disruption, and long-term harm to an organization’s picture. The problem lies in growing a safety infrastructure that may adequately mitigate these dangers whereas additionally being versatile and able to increasing to counter new assault strategies.
Conventional net software firewalls normally don’t successfully deal with these difficult challenges, notably in cloud-native settings the place functions are unfold out in numerous native companies and areas. That is the place AWS WAF (Internet Software Firewall) is necessary, offering a deeply built-in answer for AWS clients.
Applied sciences
AWS WAF
AWS WAF is a versatile and sturdy service Amazon offers as a part of its AWS Suite. From their web site, they make it very clear.
With AWS WAF, you’ll be able to create safety guidelines that management bot site visitors and block frequent assault patterns comparable to SQL injection or cross-site scripting (XSS).
Broadly, AWS WAF offers some basic constructing blocks utilizing which one can construct a strong safety system.
- Managed guidelines: Managed guidelines block frequent, well-known assault patterns. AWS creates and updates these guidelines, saving clients from reinventing the wheel.
- Customized guidelines: Not all assaults might be blocked utilizing managed guidelines. Some assaults are extra distinctive to a buyer’s service implementation and want specialised dealing with. The client is accountable for creating and updating these guidelines.
- IPSet is a set of IP addresses that one can use to allowlist or block. AWS offers a managed listing and clients can create their very own.
- Regex: Some assault patterns might be reused with minor variations. Might you create a regex sample and reuse it inside your customized guidelines?
AWS WAF has a WebACL idea, the place one can bundle all the things collectively as a single cohesive unit and connect it to supported AWS Service assets that should be protected.
AWS CloudFront CDN
AWS CloudFront is the flagship CDN product supplied by Amazon and securely delivers information, photographs, movies, and any content material that the client needs thereby lowering latency if caching insurance policies are enabled. Together with the everyday advantages of a CDN like decrease latency, it presents
- DDoS safety on the edge: The assaults don’t make it over to your servers.
- Caching region-specific static pages to considerably cut back looking occasions
- Encrypt the end-to-end expertise utilizing safe digital certificates.
AWS Software Load Balancer
AWS offers two sorts of load balancers: Community Load Balancer (NLB), which works on the L3/L4 layer of the networking stack, and Software Load Balancer (ALB), which works on the L7 software layer. AWS WAF works totally on the L7 layer. That is made abundantly clear by AWS WAF or AWS Defend.
For WAF to work, we now have to decide on ALB quite than NLB. Load balancers are imagined to be extremely accessible by expectation, and if the attacker manages to compromise the load balancer, it defeats the first objective. Utilizing AWS Defend and AWS WAF with ALB is the beneficial answer.
AWS API Gateway
API Gateway is a totally managed cloud service that lets builders construct and deploy APIs, the commonest being REST APIs. It permits an authentication mechanism and is extremely scalable. Since most requests are served on the L7 or HTTP layer, attackers can ship specifically crafted requests to use any attainable safety loopholes.
To mitigate this potential safety danger, we must always affiliate AWS WAF with API Gateway to handle points particular to this use case and this layer of the structure stack.
Methodologies
Block Completely different Sorts of Assaults at Completely different Phases
Not all assaults might be blocked in any respect locations of the cloud stack. Even when it may be, it may not be as environment friendly as one would possibly suppose. Primarily, we are able to block at three locations.
- CDN – Block regional assaults: It really works effectively when the attackers usually are not extremely distributed, nevertheless it works fairly effectively even when they’re distributed in all places. CloudFront has a number of Level-of-Presence (PoP) worldwide with storage and computing that may block malicious assaults on the first level of site visitors ingress and spare the webservers from taking the brunt of such costly assaults.
- Software Load Balancer: These are regional load balancers sitting contained in the AWS community, most likely inside your subnet, and have the accountability of spreading the site visitors load throughout a number of cases of your net server. Many of the frequent assaults must be blocked by the point site visitors reaches ALB. At this layer, extra advanced and rarer assaults might be dealt with.
- API Gateway: The API Gateway is the place the place we might deal with the precise assaults associated to API Design. The attacker might attempt to ship a malformed POST request that has the aptitude to trigger severe points. Such validations could be too costly to implement in code.
Completely different AWS Guidelines for Completely different AWS Assets
Fee Primarily based Guidelines
The very best place to place rate-based guidelines is on the sting, nearer to the customers. Loads of occasions, we use IP-based rate-limiting. Relying on the implementation of the rate-limiting logic for that particular CDN, it could be attainable to be fairly environment friendly for the reason that variety of IPs that may use a specific PoP is a a lot smaller subset of all the purchasers accessing that service. Within the case of CloudFront, there’s a PoP in San Francisco and Santa Clara, each throughout the larger San Francisco Bay Space. Site visitors from San Jose can be routed to Santa Clara PoP, and San Mateo or Oakland can be routed to San Franciso PoP. Every PoP has a smaller deal with area to compute the speed limits.
An instance of fee primarily based rule is:
{
"Name": "RateLimitRule",
"Priority": 1,
"Action": {
"Block": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "RateLimitRule"
},
"Statement": {
"RateBasedStatement": {
"Limit": 2000,
"AggregateKeyType": "IP"
}
}
}Maliciously Crafted Requests
Non-rate-limiting however low-effort high-volume assaults like Log4J or SQL injection assaults primarily based on most typical patterns might be greatest blocked on the Edge itself. This ensures that the site visitors that makes it to regional information facilities is far smaller than the overall site visitors despatched to the sting.
Particular Headers Allowlist
In case your software requires particular headers to be current, you’ll be able to permit them to be listed as the primary rule of your WebACL and set the default motion of WebACL to dam. This ensures that each one malformed HTTP requests can be blocked on the edge and considerably filters out undesirable site visitors on the edge.
Validation Token
If you need your software to comprise particular validation tokens in headers, you’ll be able to specify such guidelines within the WebACL related to the Software Load Balancer. This ensures that different companies in your group that need to entry your service can instantly attain ALB throughout the AWS community itself. Placing these sorts of guidelines on ALB WAF ensures that they’re enforced for each inner and exterior customers.
File Varieties
In case your API endpoint solely permits particular file sort uploads, that may be included within the WAF related to the API Gateway. Such restrictions might be applied in software logic, too, however if you wish to block an express listing, then the WAF on the API Gateway is usually a good selection.
JWT or API Key
In case your software makes use of JWT for token-based authentication, the WAF guidelines can give attention to such logic when related to API Gateway. We are able to use the identical place for API Key Validation. An instance of such a rule is:
{
"Name": "ValidateJWTToken",
"Priority": 5,
"Action": {
"Block": {}
},
"VisibilityConfig": {
"SampledRequestsEnabled": true,
"CloudWatchMetricsEnabled": true,
"MetricName": "ValidateJWTToken"
},
"Statement": {
"NotStatement": {
"Statement": {
"ByteMatchStatement": {
"SearchString": "Bearer ",
"FieldToMatch": {
"SingleHeader": {
"Name": "Authorization"
}
},
"TextTransformations": [
{
"Priority": 0,
"Type": "NONE"
}
],
"PositionalConstraint": "STARTS_WITH"
}
}
}
}
}Payload Limits
If we need to implement Payload dimension limits, we are able to put them on both the sting, API, or ALB. There is no such thing as a appropriate reply, and it is determined by what you are promoting logic. Ideally, it’s greatest to place such guidelines on the sting to keep away from large information switch prices, however it may well additionally imply inner companies can bypass such limits.
Blocking Some Assaults in Software Logic
Not all the things might be blocked on the WAF guidelines stage since it may be too advanced to implement utilizing the standardized WAF syntax. Take, for instance, a Downgrade assault, the place the assault wish to exploit the backward compatibility nature of the design. Authentication validation techniques might be prone to Move-The-Hash assaults, the place the attacker doesn’t have to de-hash the hashed password however tries to restart the session utilizing stolen hashed passwords. Code Injection assaults must be addressed within the code itself as we use code to validate the enter information.
General Design
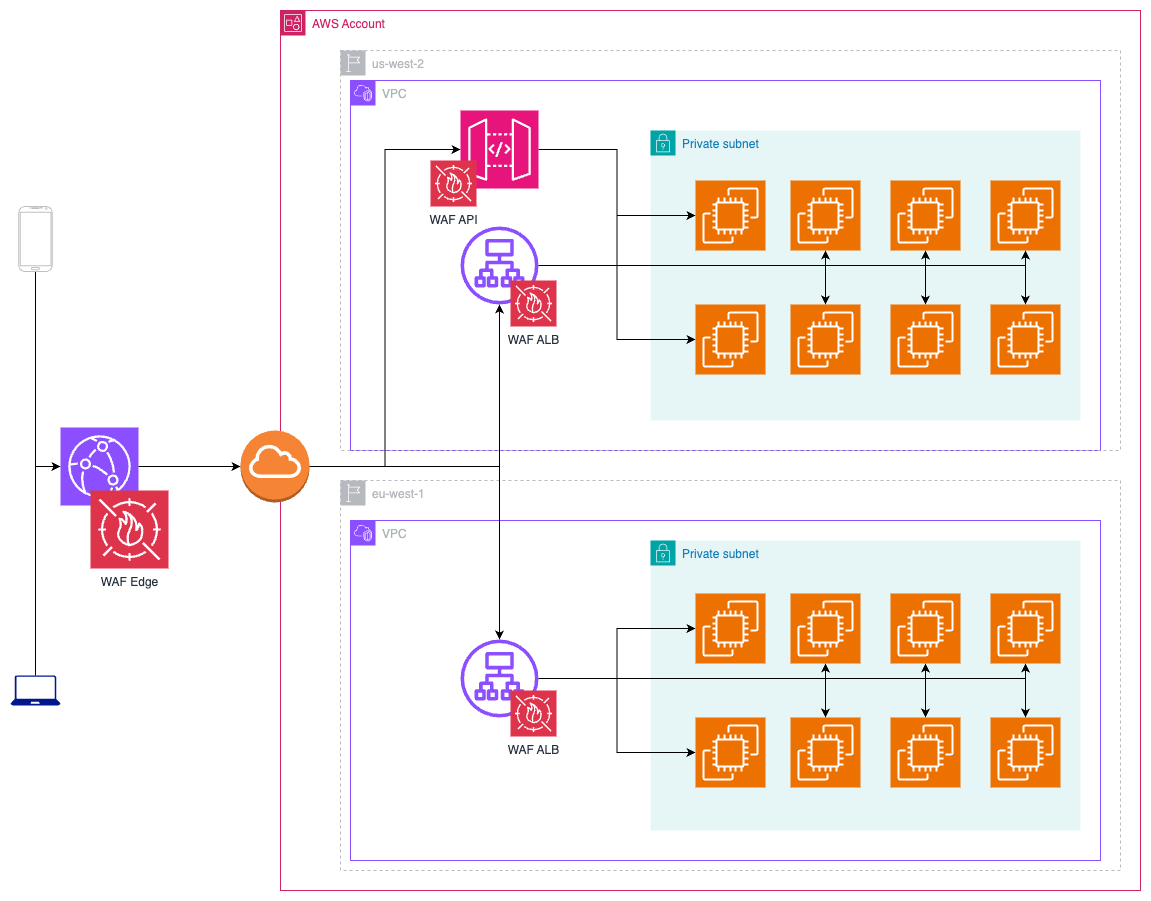
A candidate design of the cloud structure. Various enterprise wants can change the general design.
Conclusion
Utilizing AWS WAF with CloudFront, API Gateway, and Load Balancer created a strong and dependable structure. As cloud-native options, one can use AWS CDK to outline the code configuration, thereby explicitly following Infrastructure as Code patterns. We are able to tailor particular guidelines to particular levels and assets to create a seamless and environment friendly safety posture.
I might strongly counsel the engineers engaged on the cloud structure not contemplate any design to be set in stone. Common iterations and evaluations are wanted to keep away from accumulating pointless technical debt. Utilizing AWS WAF wants to incorporate a correct operational plan and incident response plan. Maintaining a tally of WAF Logs and extracting related metrics is essential in keeping track of the effectivity of the foundations. I counsel rigorously contemplating alarms primarily based on the enterprise wants and typical site visitors patterns. The operational plan ought to define how such alarms behave, and the incident response plan ought to define what the on-call ought to do when particular incidents are in progress.
