Cthulhu Stealer in motion [Cado Security]
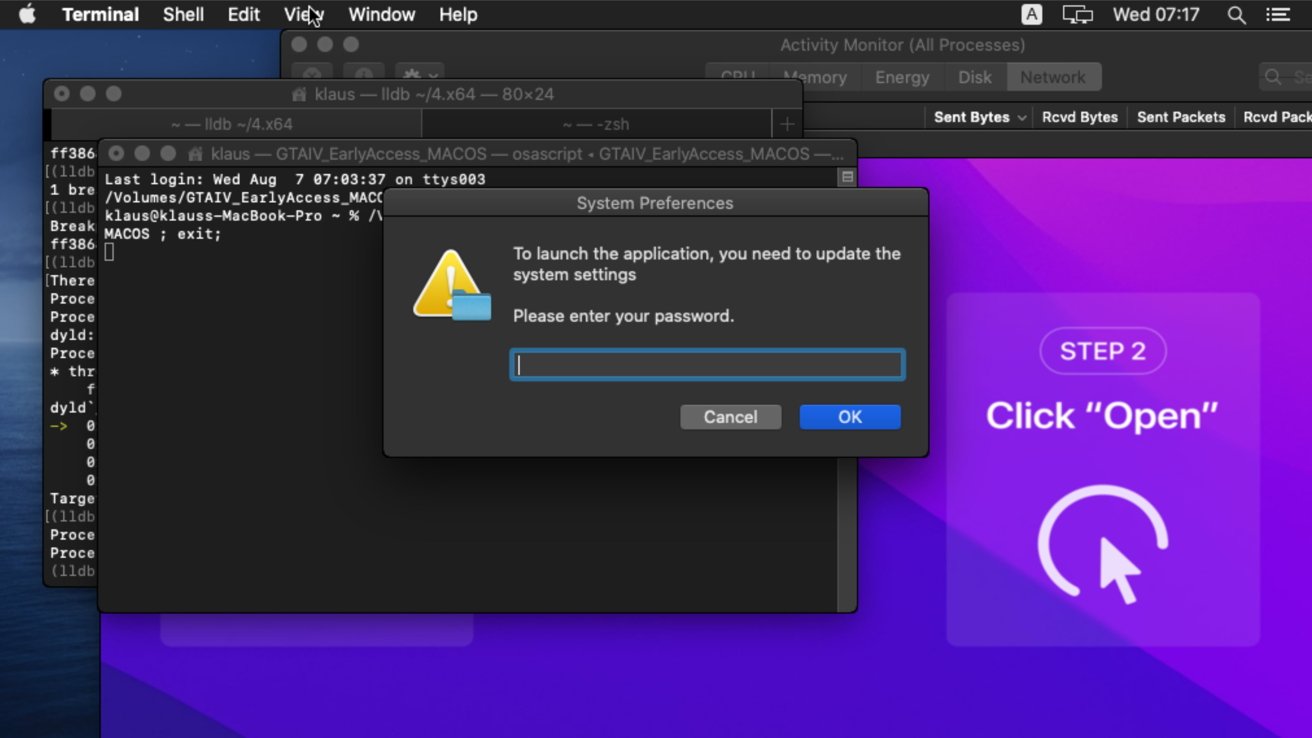
Researchers have found one other data-seizing macOS malware, with “Cthulhu Stealer” offered to on-line criminals for simply $500 a month.
The Mac is turning into much more of a goal for malware, with warnings surfacing from researchers surfacing frequently. Within the newest instance, it is for malware that is been in circulation for fairly just a few months.
Defined by Cato Safety and reported by Hacker Information on Friday, the malware known as “Cthulu Stealer” has apparently been round since late 2023. Consisting of “Malware-as-a-Service,” it was in a position for use by on-line criminals for a mere $500 monthly.
Dangerous disk photos
The malware takes the type of an Apple disk picture that accommodates a pair of binaries. This allowed it to assault each Intel and Apple Silicon Macs, relying on the detected structure.
To attempt to entice customers to open it, the malware can be disguised as different software program, together with Grand Theft Auto IV and CleanMyMac. It additionally appeared as Adobe GenP, a instrument for patching Adobe apps in order that they do not depend on receiving a paid safety key from the Artistic Cloud.
The supposed contents was a ploy to persuade customers to launch the unsigned file and permitting it to run after bypassing Gatekeeper. The customers are then requested to enter their system password, adopted by a password for the MetaMask cryptocurrency pockets.
With these passwords in place, system data and iCloud Keychain passwords are stolen, together with internet browser cookies and Telegram account particulars. They’re despatched off to a management server.
“The main functionality of Cthulhu Stealer is to steal credentials and cryptocurrency wallets from various stores, including game accounts,” stated Cato Safety researcher Tara Gould.
Borrowing code
Evaluation of the malware signifies that the malware is much like one other that was beforehand discovered by the title of “Atomic Stealer.”
It’s thought that whomever made Cthulu Stealer used the code that produced Atomic Stealer as a base. Apart from performance, the principle proof of that is an OSA script that prompts for the consumer’s password, which has the identical spelling errors.
Unusually for found malware, it seems that the creators of Cthulhu Stealer aren’t capable of handle it, as a consequence of fee disputes. The developer behind it was completely banned from a cybercrime market that marketed the instrument over accusations of an exit rip-off that affected different market customers.
Defending your self
Customers haven’t got to do this a lot to guard themselves from Cthulhu Stealer, not least due to possession management points.
As typical, the recommendation is to be vigilant about what apps you obtain, that you simply obtain from protected sources, and to concentrate to what the app does as you put in it.
As for overriding Gatekeeper, that is one thing that may be completed simply in macOS Sonoma and earlier releases. For macOS Sequoia, customers can’t Management-click to override Gatekeeper, however might want to go to System Settings then Privateness & Safety to overview a software program’s safety data as an alternative.
This transformation ought to cut back the variety of situations the place Gatekeeper is bypassed, just by including extra obstacles.
Even so, customers ought to nonetheless listen each time Gatekeeper raises an objection to putting in or operating an app.

