Know-how within the digital age has revolutionized our lives. Nevertheless, this comfort comes with a rising risk: cybercrime. Malicious actors, starting from petty thieves to classy cybercriminals, function on-line, searching for to use vulnerabilities and steal delicate data, monetary knowledge, and even identities.
From on-line banking and buying to social media and distant work, the web has turn out to be a necessary a part of our each day routines. What does it imply when your on-line id is turned in opposition to you? Or when it’s worthwhile to show your individual id to regain management of instruments you beforehand assumed had been solely there to make your life simpler?
This text equips you with the elemental data and practices to guard your self on-line. A number of the matters I’ll tackle are the core rules of cybersecurity, exploring sturdy passwords, two-factor authentication, software program updates, and securing your gadgets. Specifically, I’ll deep dive into the way to establish and keep away from phishing assaults and scams. Lastly, I would like you to depart this text to grasp the significance of on-line privateness and knowledge safety, not only for your self however for safeguarding your households and broader social networks, as nicely.
Constructing a Strong Protection: Passwords and Authentication
The primary line of protection in cybersecurity is entry management. Sturdy passwords and sturdy authentication strategies are essential for this. A weak password, like your birthday or pet’s title, is well compromised by automated applications and even educated guesses.
Listed here are some key rules for creating unbreakable passwords:
- Size is essential: Goal for a minimum of 12-15 characters.
- Embrace variety: Use a mix of uppercase and lowercase letters, numbers, and symbols.
- Keep away from predictability: Avoid dictionary phrases, keyboard patterns (e.g., “qwerty”), and private particulars.
- Uniqueness is crucial: Do not reuse passwords throughout completely different accounts.
Remembering quite a few complicated passwords generally is a problem. Password managers provide an answer that may forestall you from tearing out your hair making an attempt to recollect every service’s login credentials. These safe functions retailer your passwords and might even generate sturdy, distinctive passwords for every of your accounts. In its usually humorous trend, this XKCD comedian has some surprisingly poignant and helpful ideas, which may be particularly helpful for producing and remembering the password for a password supervisor.
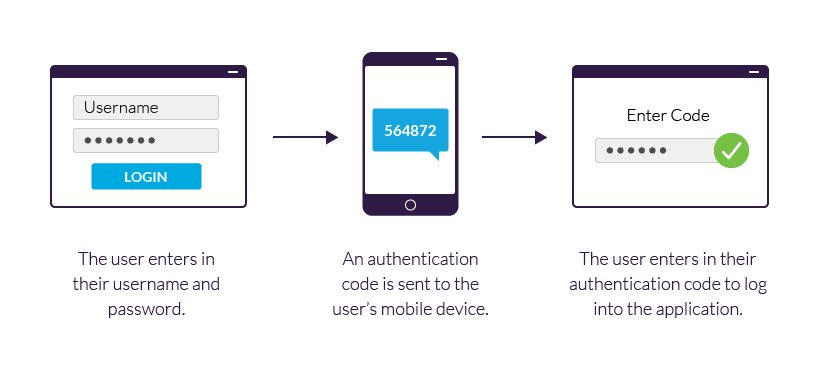
Two-factor authentication (2FA) provides one other layer of safety by requiring a second verification step after coming into your password. This could possibly be a code despatched to your cellphone through textual content message, a fingerprint scan, or a facial recognition immediate. Enabling 2FA considerably reduces the danger of unauthorized entry, even when your password is compromised.
Retaining Your Software program Up to date: Patching the Gaps
Unpatched software program vulnerabilities are like cracks in your digital armor. Hackers always scan for these weaknesses to use them and achieve entry to your system. Software program updates, usually free and available, patch these vulnerabilities, considerably hindering attackers.
Listed here are some greatest practices for software program updates:
- Allow automated updates: Most software program means that you can configure automated updates for the working system, functions, and net browsers. This ensures you are all the time protected by the most recent safety patches.
- Keep knowledgeable: Hold a watch out for crucial safety updates that require guide set up.
- Prioritize updates for safety software program: Often replace your antivirus, anti-malware, and firewall software program to profit from the most recent risk detection capabilities.
Securing Your Gadgets: Past the Desktop
Our digital lives lengthen past desktops and laptops. Smartphones and tablets maintain a wealth of non-public data and require equal consideration to safety.
This is the way to safeguard your cell gadgets:
- Use sturdy passwords or PINs: Do not underestimate the significance of a safe display screen lock in your cellphone or pill.
- Obtain apps solely from trusted sources: App shops vet apps for safety dangers, so keep away from downloading from unknown sources.
- Be cautious with app permissions: Grant apps solely the permissions they completely have to perform.
- Allow distant wipe: This lets you erase all knowledge out of your system remotely in case it will get misplaced or stolen.
One level, usually ignored, is that public Wi-Fi networks could also be handy however are sometimes unsecured. Keep away from accessing delicate data or monetary accounts whereas linked to public Wi-Fi. If vital, think about using a digital personal community (VPN) to encrypt your web visitors on public networks.
Recognizing Deception: Phishing Assaults and Scams
Phishing assaults try to trick you into revealing private data or clicking on malicious hyperlinks. They usually come disguised as emails, textual content messages, or faux web sites imitating respectable entities like banks, social media platforms, and even your boss.
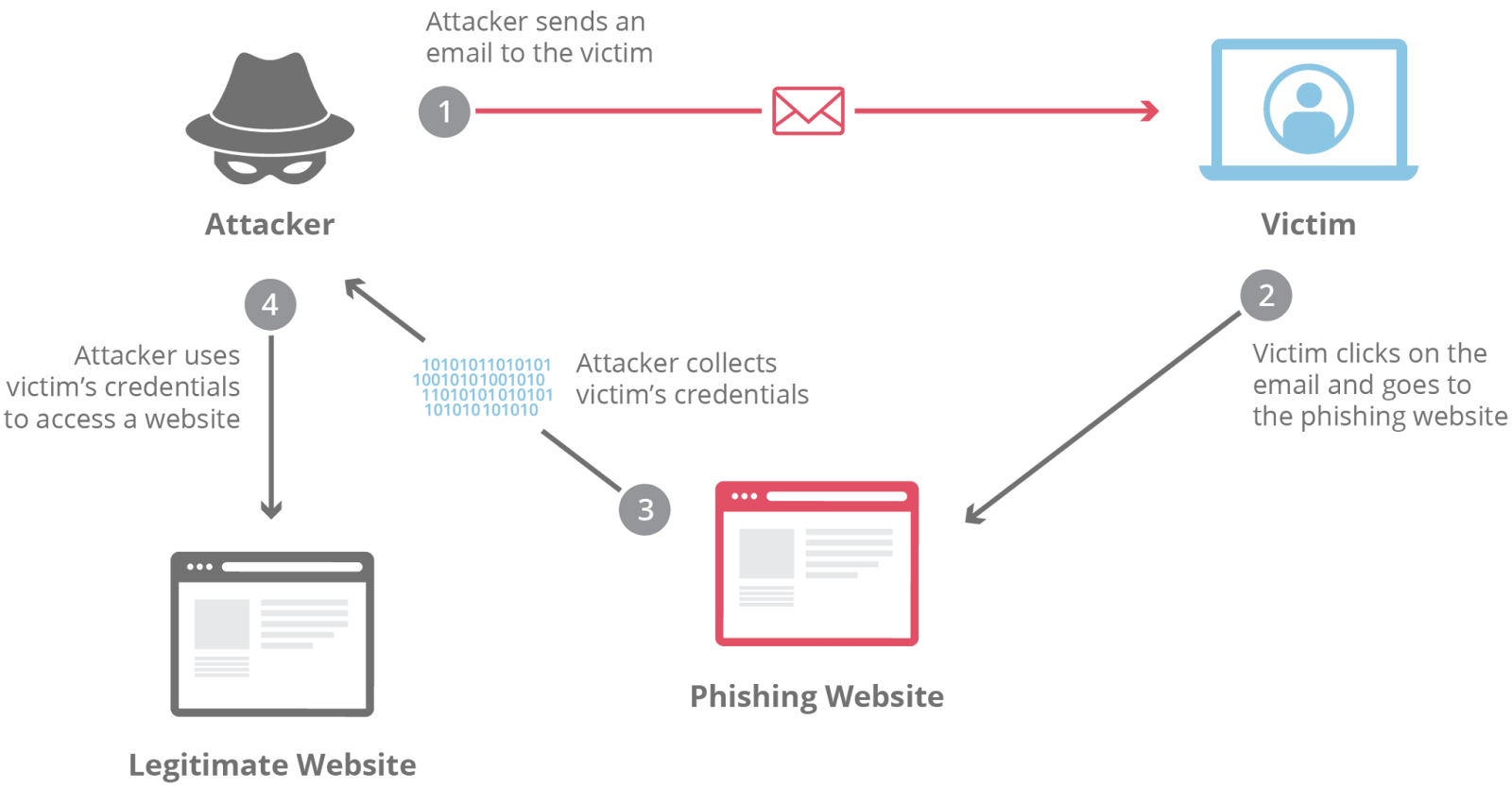
This is the way to establish phishing makes an attempt:
- Suspicious sender addresses: Test the sender’s e-mail tackle rigorously for typos or inconsistencies.
- Urgency and stress techniques: Phishing emails usually create a way of urgency or stress to compel you to behave with out pondering critically.
- Grammatical errors and poor formatting: Respectable corporations normally preserve excessive requirements for e-mail communication.
- Unrealistic provides or threats: Be cautious of emails providing unbelievable offers or threatening dire penalties in case you do not comply.
- Hover over hyperlinks earlier than clicking: Do not click on on suspicious hyperlinks instantly. Hover your mouse cursor over the hyperlink to see the precise vacation spot URL within the backside left nook of your browser window.
In case you suspect a phishing try, do not reply to the e-mail or click on on any hyperlinks. Many e-mail suppliers/web sites have a “report phishing” button. Use this selection to report the try and assist forestall others from falling sufferer.
Safeguarding Your Privateness: Controlling Your Digital Footprint
The huge quantity of information we generate on-line creates a digital footprint, a path of our actions and preferences. Whereas some knowledge assortment is critical for sure on-line providers, it is essential to be aware of how a lot data you share and with whom.
Listed here are some steps you’ll be able to take to guard your on-line privateness:
- Evaluate your privateness settings on social media platforms and different on-line accounts. Restrict the data that’s publicly seen and management who can see your posts and exercise.
- Be cautious about what data you share on-line. Keep away from posting private particulars like your property tackle, cellphone quantity, or birthdate publicly.
- Beware of information breaches. Allow knowledge breach notifications for the providers you employ and think about using a service that screens your e-mail tackle for breaches.
Knowledge breaches can compromise your private data. Sturdy passwords and never reusing them throughout accounts assist mitigate this threat. Nevertheless, it is also essential to pay attention to knowledge breaches and take steps to guard your self in case your data is uncovered.
This is what to do in case of a knowledge breach:
- Change your passwords instantly. In case your login credentials are compromised in a knowledge breach, change your passwords for the affected accounts and another accounts the place you have used the identical password.
- Monitor your accounts for suspicious exercise. Be vigilant for any unauthorized transactions or modifications to your account data.
- Take into account credit score freezing or monitoring. Relying on the severity of the info breach, you could wish to think about putting a credit score freeze in your accounts or enrolling in credit score monitoring providers.
Embracing a Safe Digital Life-style
The digital age provides immense advantages, nevertheless it additionally comes with inherent dangers. By following the cybersecurity necessities outlined on this article, you’ll be able to considerably scale back your threat of falling sufferer to cyberattacks and shield your on-line privateness. Keep in mind, cybersecurity is an ongoing course of. Keep knowledgeable about evolving threats, replace your software program usually, and be vigilant concerning the data you share on-line. By embracing these practices, you’ll be able to navigate the digital world with confidence and benefit from the huge potentialities it provides.

