Editor’s Observe: The next is an article written for and revealed in DZone’s 2024 Development Report, Enterprise Safety: Reinforcing Enterprise Software Protection.
Full-stack safety protects each layer of a software program utility, together with the entrance finish, again finish, infrastructure, and community. It integrates sturdy safety measures to handle vulnerabilities by using instruments and practices to take care of knowledge integrity, stop unauthorized entry, and guarantee compliance, particularly as purposes broaden and combine with numerous applied sciences and platforms.
Understanding the safety measures required at every layer of an utility is essential for builders to make sure complete safety. This information explores important methods and instruments to safe fashionable purposes at each layer and addresses the most effective practices and challenges encountered in full-stack safety.
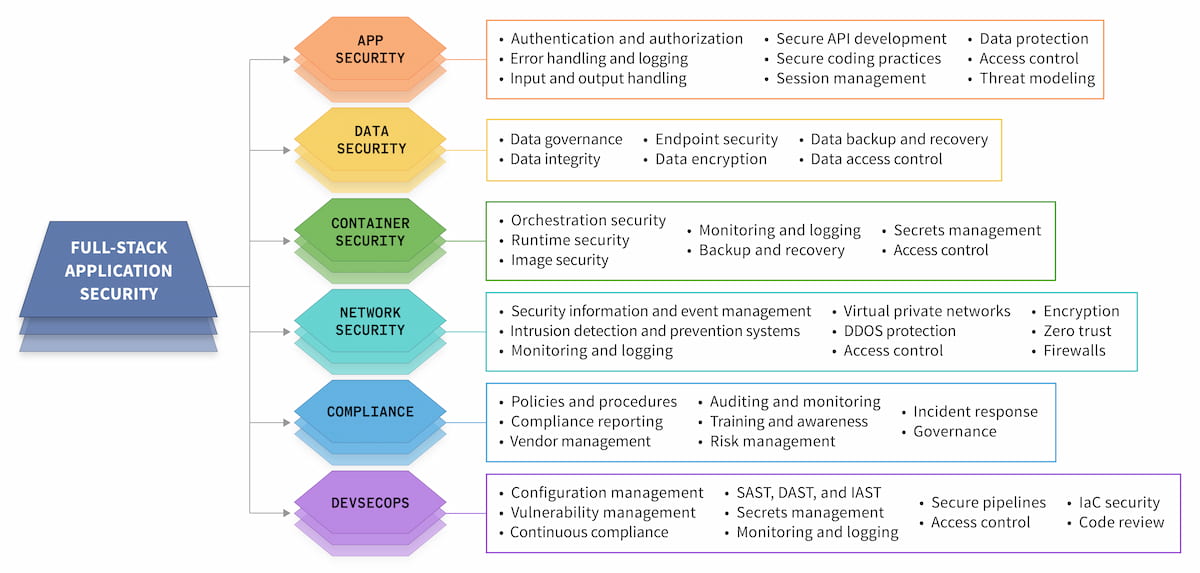
Determine 1. Software safety elements
Menace Modeling for Full-Stack Purposes
Menace modeling is essential for retaining full-stack purposes safe. It includes an intensive evaluate to identify potential threats and weaknesses, permitting us to sort out these points earlier than the app goes stay. This course of requires an in depth take a look at the app’s structure, knowledge flows, and the way it operates. Utilizing a guidelines just like the one beneath supplies a structured strategy to menace modeling.
Preparation Section
- Perceive the appliance’s scope and objective, together with main operate and goals, structure, audience, and utility boundaries
- Assemble a cross-functional menace modeling staff together with builders, safety consultants, and system architects
Modeling Section
- Doc the appliance structure, highlighting all elements, knowledge flows, and exterior interactions
- Determine belief boundaries and classify all knowledge processed and saved by the appliance
Identification Section
- Checklist potential menace brokers (e.g., hackers, third-party providers)
- Catalog potential threats utilizing frameworks like STRIDE
- Determine vulnerabilities (e.g., static evaluation, code opinions)
Evaluation Section
- Assess the chance and influence of recognized threats
- Prioritize threats based mostly on their danger ranges utilizing a danger matrix
Mitigation Section
Implementation and Observe-Up Section
- Implement the mitigation methods and safety controls
- Check and validate the carried out safety measures
- Plan for normal updates to the menace mannequin as the appliance or surroundings evolves
Steady Enchancment Section
- Set up steady monitoring to detect new threats utilizing SIEM instruments
- Schedule periodic opinions
- Encourage ongoing safety coaching for the event and operations groups
Safe Coding Practices
Safe coding practices are important for safeguarding full-stack purposes from threats and vulnerabilities. On this part, we’ll dive into pointers that cowl each layer of the stack, serving to builders construct resilient purposes that may deal with each present and future safety challenges.
Desk 1. Safe coding practices for full-stack purposes
| Class | Finest Practices | Instruments/Strategies |
| Enter validation | – Validate all inputs to forestall frequent vulnerabilities (e.g., cross-site scripting, SQL injection) – Use strict kind, format, and content material checks |
– OWASP Validator – sanitize-html – Joi (for Node.js) |
| Authentication | – Implement sturdy multi-factor authentication – Securely handle session tokens and cookies – Make the most of safe password storage methods |
– OAuth – JSON Internet Token (JWT) |
| Authorization | – Implement the precept of least privilege – Use role-based or attribute-based entry controls – Frequently evaluate and replace entry controls |
– Spring Safety – CASBIN (for Go and Node.js) |
| Information safety | – Encrypt delicate knowledge at relaxation and in transit – Use safe knowledge serialization and deserialization strategies – Apply knowledge masking |
– Transport layer safety – Superior Encryption Normal – Information masking instruments |
| API safety | – Safe API endpoints in opposition to frequent assaults – Implement price limiting – Use API gateways for added safety layers |
– API gateways – JWT – OAuth |
| Error dealing with | – Keep away from detailed error messages revealing system info – Implement centralized error dealing with to forestall leakage |
– Customized error handlers – Logging libraries |
| Logging and monitoring | – Log all entry and modifications to delicate knowledge – Guarantee logs don’t comprise delicate info – Use real-time monitoring for safety alerts |
– SIEM techniques – ELK stack (Elasticsearch, Logstash, Kibana) |
| Configuration administration | – Safe all utility and server configurations – Automate configurations – Use configuration administration instruments for consistency |
– Configuration administration instruments (e.g., Ansible) |
| Safety testing | – Carry out static and dynamic evaluation – Frequently conduct penetration testing – Make the most of automated safety scanning instruments |
– SAST and DAST instruments – Penetration testing providers |
| Container safety | – Use trusted base photos – Safe runtime configurations – Guarantee sturdy container isolation – Frequently scan for vulnerabilities |
– Docker Bench for Safety – Clair |
| Community safety | – Isolate delicate elements utilizing community segmentation – Use firewalls and intrusion detection techniques – Safe communication channels – Implement zero-trust architectures |
– Firewalls – Intrusion detection system/intrusion prevention system – VPNs |
| Incident response | – Develop and replace incident response plans – Practice employees on detection and response – Simulate safety incidents |
– NIST Incident Response – NCSC Cyber Incident Response |
Authentication and Authorization Mechanisms
Authentication and authorization are foundational to securing full-stack purposes. Implementing sturdy authentication and authorization mechanisms is important for shielding delicate knowledge and functionalities in full-stack purposes.
Implementing Authentication
Authentication verifies a consumer’s identification to make sure they’re who they declare to be. Core strategies of authentication embrace username/password, multi-factor authentication (MFA), certificates based mostly, single sign-on (SSO), token based mostly, and public key infrastructure (PKI). Implementing authentication strategies includes adopting greatest practices that guarantee safety and consumer belief:
- Builders ought to leverage sturdy authentication protocols equivalent to OAuth2 and JWT for safe and scalable authentication processes.
- Imposing MFA provides an additional layer of safety, decreasing the danger of unauthorized entry.
- Passwords should be hashed utilizing sturdy algorithms like bcrypt earlier than storage, and ensure session administration is safe sufficient to forestall session hijacking.
- Builders also needs to be certain that all authentication-related communication is encrypted utilizing HTTPS to keep away from interception.
- Implement account lock-out insurance policies to forestall brute pressure assaults.
- Frequently evaluate and replace your authentication strategies to remain forward of rising threats and vulnerabilities, making certain the appliance stays safe.
Desk 2. Execs and cons of authentication strategies
| Methodology | Execs | Cons |
| Password based mostly | – Easy to grasp and implement – Ubiquitous, supported by most techniques |
– Weak to brute-force and dictionary assaults – Requires sturdy password insurance policies and safe storage |
| MFA | – Provides an additional layer of safety – Considerably reduces danger of compromised accounts |
– Might be cumbersome for customers – Extra prices for implementation and upkeep – Depending on consumer’s entry to a second issue (e.g., telephone) |
| Token based mostly | – Stateless and scalable – Helps SSO |
– Token theft can result in unauthorized entry – Token administration and storage complexity – Requires safe token issuance and validation |
| Certificates based mostly | – Robust safety with digital certificates – Appropriate for machine and consumer authentication |
– Complexity in managing certificates – Certificates issuance and revocation processes – Excessive preliminary set-up prices |
| SSO | – Handy for customers, with one login for a number of techniques – Reduces password fatigue |
– Single level of failure – Complicated implementation and configuration – Dependency on identification suppliers |
| Federated identification administration | – Simplifies consumer administration throughout techniques – Reduces password fatigue with SSO |
– Requires belief between federated companions – Complicated implementation and configuration – Dependency on identification suppliers |
| PKI | – Robust safety with cryptographic keys – Appropriate for safe communications and knowledge integrity |
– Complicated key administration – Excessive preliminary set-up and upkeep prices – Requires safe key storage and distribution |
Implementing Authorization
Authorization determines what an authenticated consumer is allowed to do inside a system. Strategies of authorization are role-based entry management (RBAC), attribute-based entry management (ABAC), and permission-based entry management (PBAC). Implementing authorization strategies in purposes requires considerate planning to make sure customers have the fitting entry ranges based mostly on their roles and duties:
- Builders ought to undertake efficient authorization strategies to handle permissions effectively, making certain that customers have solely mandatory entry.
- Following the precept of least privilege by granting minimal permissions helps scale back the danger of unauthorized actions.
- Securing APIs and back-end providers by validating tokens and consumer roles for each request is crucial.
- Frequently auditing permissions and entry logs helps determine and repair any unauthorized entry makes an attempt.
- Utilizing entry reconciliation processes to repeatedly verify that consumer permissions match their present roles ensures that entry rights are at all times updated and cling to the precept of least privilege.
- Centralizing and retaining authorization logic constant throughout the appliance boosts safety and simplifies administration.
Desk 3. Execs and cons of authorization strategies
| Methodology | Execs | Cons |
| RBAC | – Easy and straightforward to handle – Centralized management over consumer permissions – Reduces administrative overhead |
– Can turn into advanced with many roles – Roles can turn into outdated or overly broad |
| ABAC | – Extremely versatile – Can deal with advanced entry insurance policies – Context conscious |
– Complicated to implement and handle – Efficiency overhead because of coverage analysis |
| PBAC | – Centralized administration of entry insurance policies – Extremely adaptable to totally different contexts and environments |
– Requires subtle coverage administration instruments – Potential efficiency influence |
Database Safety and Information Safety
Database safety and knowledge safety are essential features of managing and safeguarding info inside a company. They contain a spread of practices and applied sciences designed to guard databases from unauthorized entry, use, or modification in addition to disclosure, disruption, or destruction. Understanding database safety and safety is essential for builders to make sure the integrity, confidentiality, and availability of knowledge, which protects in opposition to breaches, ensures compliance, and maintains consumer belief.
Desk 4. Database safety and knowledge safety greatest practices
| Class | Finest Practices |
| Database entry management | – Implement RBAC – Use MFA – Evaluate and replace entry permissions repeatedly |
| Information encryption | – Encrypt delicate knowledge at relaxation and in transit utilizing sturdy protocols – Use key administration options to safe key dealing with |
| Information masking and redaction | – Use dynamic knowledge masking for real-time safety – Apply static masking in check environments |
| SQL injection prevention | – Use ready statements and parameterized queries – Conduct common code opinions and safety testing – Make use of internet utility firewalls to dam SQL injection assaults |
| Backup and restoration | – Implement automated and common backups – Retailer backups securely, presumably off web site – Frequently check restoration procedures to make sure efficient knowledge restoration |
| Information privateness rules compliance | – Keep knowledgeable about knowledge safety legal guidelines (e.g., GDPR, HIPAA) – Implement compliance insurance policies and applied sciences – Frequently audit practices and conduct coaching |
Cloud Safety Concerns
Cloud safety concerns are essential for shielding knowledge, making certain compliance, and sustaining service reliability in cloud environments. They information builders in securing utility design, deployment, and administration, in the end safeguarding in opposition to breaches and making certain consumer belief. Key cloud safety concerns embrace:
- Shared accountability mannequin – Perceive and outline what safety elements are managed by the cloud supplier versus these managed by your staff.
- Cloud-specific identification and entry administration (IAM) – Make the most of cloud supplier IAM instruments to handle consumer identities and permissions securely.
- Information residency and sovereignty – Adjust to legal guidelines and rules concerning the place knowledge is saved and the way it’s transferred throughout borders.
- Cloud community safety – Implement digital non-public clouds and personal subnets to manage community visitors. Use safety teams and community ACLs to implement safety.
- Cloud compliance and authorized concerns – Adhere to cloud-specific rules and requirements to make sure compliance throughout all operational areas.
- Cloud menace detection and monitoring – Deploy cloud-native monitoring options that supply integration with cloud platforms for real-time menace detection and safety logging.
- Cloud incident response – Develop cloud-specific incident response protocols leveraging cloud providers for sooner and extra scalable responses.
- Cloud catastrophe restoration – Make the most of cloud infrastructure to arrange and handle catastrophe restoration options which are sturdy and geographically distributed.
- Cloud safety posture administration (CSPM) – Use CSPM instruments to repeatedly consider and handle the cloud safety posture throughout numerous cloud environments.
Conclusion
Securing full-stack purposes is more and more advanced however essential in at present’s digital world. As know-how advances and threats develop extra subtle, sturdy safety measures throughout all layers of your stack are important. Organizations should foster a tradition of safety, repeatedly replace practices, and keep proactive. The way forward for full-stack safety will probably be formed by AI for higher menace detection, zero-trust fashions for steady verification, and evolving practices for cloud-native applied sciences and DevSecOps integration.
Extra sources:
That is an excerpt from DZone’s 2024 Development Report, Enterprise Safety: Reinforcing Enterprise Software Protection.
Learn the Free Report

