Loopy Evil malware

Specialists lately found a macOS stealer malware disguised as the favored display screen recording app Loom, unfold by misleading Google-sponsored URLs.
Moonlock Lab discovered a complicated macOS stealer malware disguised as Loom, orchestrated by the infamous Loopy Evil group. It makes use of misleading Google-sponsored URLs to trick customers into downloading dangerous software program.
The investigation started when Moonlock Lab recognized a Google advert selling the official Loom app. The advert appeared reliable and enticed customers to click on on a trusted supply.
Nonetheless, clicking the hyperlink redirected customers to a web site almost similar to the official Loom web site, hosted at smokecoffeeshop[.]com. Customers had been prompted to obtain what they believed was Loom, a malicious file containing stealer malware.
The marketing campaign was not restricted to Loom. The attackers had additionally created pretend variations of different fashionable functions, together with Figma, TunnelBlick (VPN), Callzy, and a suspiciously named file, BlackDesertPersonalContractforYouTubepartners[.]dmg.
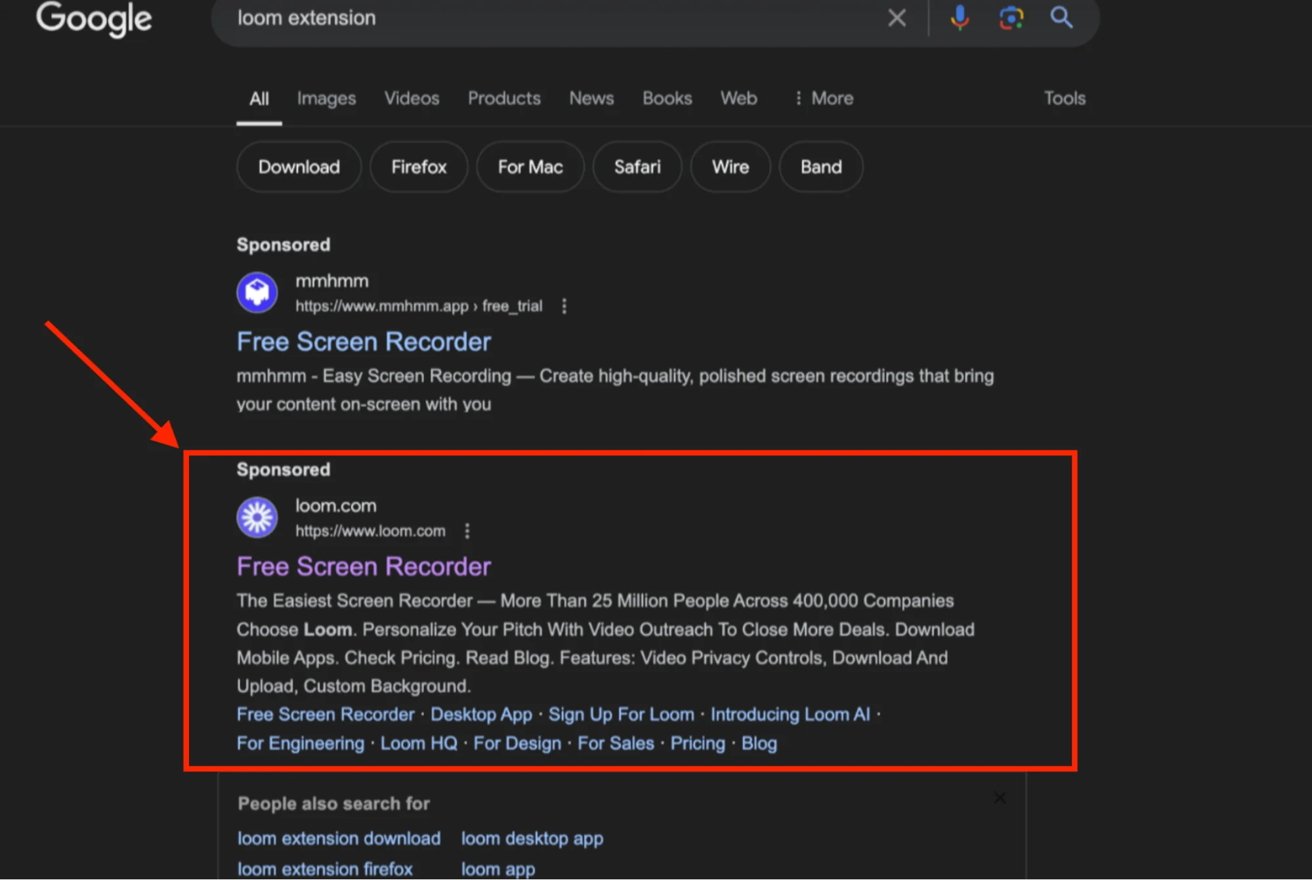
A misleading Google sponsored hyperlink
The final instance suggests a phishing marketing campaign concentrating on YouTube content material creators, a tactic beforehand used towards Home windows customers however now repurposed for macOS.
Related phishing emails had been despatched to Home windows customers in 2022. Mac customers face the identical threats, with attackers exploiting the connection between gaming firms and content material creators. They lure bloggers and content material creators with guarantees of profitable contracts to advertise video games like Black Desert On-line on their channels.
A malicious LedgerLive clone
A side of the marketing campaign entails utilizing a stealer that replaces the reliable LedgerLive app with a malicious clone. LedgerLive is broadly utilized by cryptocurrency holders, making it a goal for cybercriminals.
Attackers can entry and drain victims’ cryptocurrency wallets by changing the real app with a dangerous model. The malicious clone mimics the reliable app’s look and performance, making it troublesome for customers to detect the compromise.
Moonlock Lab’s investigation discovered strings containing “Ledger” within the contaminated recordsdata, confirming the malicious intent in direction of customers’ cryptocurrency property. The stealer, recognized as a variant of AMOS, retains key options like grabbing recordsdata, {hardware} info, passwords, information from browsers, and keychain dump credentials.
Darknet recruitment and attribution
Darknet recruitment adverts posted by Loopy Evil search people to hitch a workforce utilizing this variant of macOS stealer. The recruitment announcement particulars advantages like dependable safety and exploiting numerous codecs for various victims.
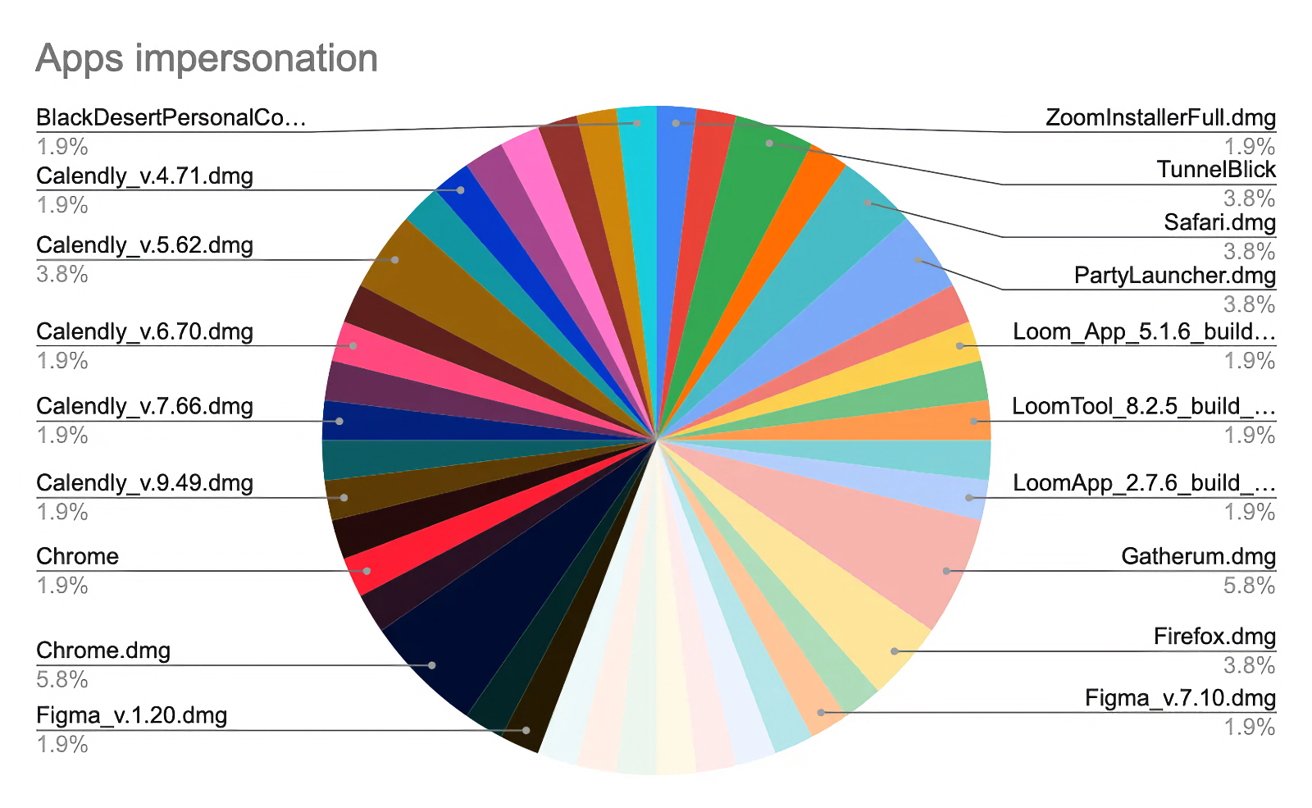
The extent of the marketing campaign
Curiously, Moonlock Lab recognized an IP handle linked to a governmental entity with excessive malware affiliation and 93 recordsdata marked as malware. The IP handle hosted macOS-related recordsdata from the marketing campaign beginning July 23, 2024.
How Mac customers can keep protected
Mac customers can shield themselves by taking proactive measures. All the time double-check URLs when downloading recordsdata, even from trusted sources like Google Advertisements or high search outcomes.
Repeatedly scan your machine with dependable anti-malware instruments like CleanMyMac X with Moonlock Engine to make sure no malicious software program is current. Hold software program up-to-date to guard towards recognized vulnerabilities.
Lastly, be cautious with emails providing contracts or offers from unknown senders to stop phishing schemes. The Mac’s built-in safety features, Gatekeeper and XProtect, present further safety towards malicious software program and are enabled by default.

