Product and infrastructure engineering groups will not be at all times aligned with the pursuits of safety engineering groups. Whereas product and infrastructure deal with driving enterprise worth and delivering sensible options, safety focuses on detection, prevention, and remediation, which might appear much less instantly worthwhile. Like an insurance coverage coverage, it isn’t fully apparent why it is well worth the cash or effort when there hasn’t been an incident but.
As an alternative of the normal cycle of figuring out vulnerabilities, making use of remediation, and following up by way of case administration, I’ve discovered it far more efficient to advocate for safety options that additionally ship enterprise worth. For instance, utilizing OAuth and IAM-based entry as an alternative of static keys and encryption as an alternative of extra granular entry management can considerably simplify infrastructure, cut back complexity, and reduce the operational burden, making them very interesting to each product and platform engineering groups.
An Instance: Change Static Keys With IAM-Primarily based OAuth
Historically, entry between programs is carried out by way of static key-secret pairs. Whereas frequent, this methodology usually results in reliability points because of the complexity of managing key era, rotation, and software lifecycle. Platform groups should additionally make investments important effort in monitoring and detecting anomalies to stop sudden key-secret compromises, reminiscent of unintended publicity by way of Slack or GitHub. Even when builders report and remediate leaks, the rotation course of may be laborious. Worse, builders might think about it a low-risk leak, and the leak can go unreported.
In response to ISO/IEC 27001:2022, A.9.1:
Organizations should implement insurance policies and procedures to regulate entry to data, making certain it’s only accessible to these with a authentic want.
Platform groups have two selections:
- Add extra complicated entry controls and approval processes.
- Change static key-secret pairs with IAM-based OAuth.
The primary possibility may be tempting, because it includes merely including a vendor like ServiceNow with out a lot further work. Nevertheless, the second possibility, whereas requiring extra implementation adjustments, is safer and reduces the operational burden on software groups to replace secrets and techniques, restart pods, and guarantee secrets and techniques are picked up. In reality, a number of corporations specializing in non-human identification authentication, reminiscent of P0 and Clutch, have not too long ago emerged, highlighting the rising development in the direction of safer and environment friendly authentication strategies.
This instance demonstrates how a special method to safety implementation can enhance safety requirements, simplify infrastructure structure, and improve total developer velocity.
The Case for Information Encryption
Information encryption is one other instance the place, though safety groups can not merely “add a vendor,” it considerably reduces complexity and implementation efforts throughout all platforms from each safety and structure design standpoints.
The everyday knowledge stream includes:
- Supply software publishes knowledge
- Information is shipped to a transport layer (e.g., Kafka, Kinesis)
- Information is saved in a database (MySQL, Postgres), knowledge warehouse (Redshift, Snowflake), or knowledge lake (S3, Databricks)
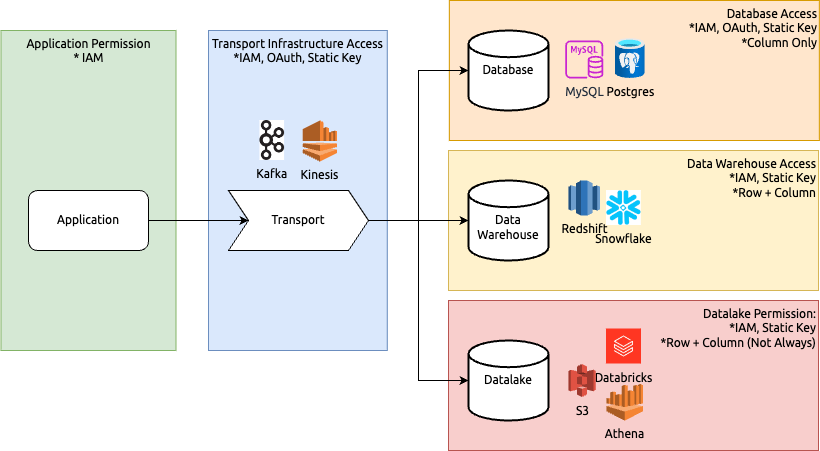
Totally different options have completely different interpretations and implementations of “access control,” main platform groups to implement their very own variations. This usually leads to fragmented implementations throughout the corporate. For safety engineers, the extra fragmented the implementations are, the tougher it’s to implement standardized governance, management, and monitoring, in the end making the system much less safe.
Infrastructure/Vendor Auth and Permission Comparability
Conclusion
With knowledge encryption, entry is configured as soon as with a crypto key and may then be assigned to particular person workloads at completely different levels of the info stream. This considerably reduces the complexities concerned in implementing and aligning permission insurance policies throughout completely different platforms. Encryption ensures that knowledge is constantly protected throughout all platforms, simplifying governance and management whereas enhancing total safety.

