On this submit, we’ll clarify all of the steps required to attach a Mule software to Salesforce utilizing the Salesforce connector with the OAuth JWT stream. You may as well create your individual certificates for the OAuth JWT stream with Salesforce or with OpenSSL (signed by a CA or self-signed). Each choices are very effectively defined within the video on the conclusion of the article from Stefano Bernardini, MuleSoft Ambassador.
 On this submit, we’ll be utilizing a self-signed certificates created by Salesforce however, be mindful, that for manufacturing environments, a certificates issued by a Trusted Certificates Authority is at all times beneficial.
On this submit, we’ll be utilizing a self-signed certificates created by Salesforce however, be mindful, that for manufacturing environments, a certificates issued by a Trusted Certificates Authority is at all times beneficial.
1. Create the Certificates
- Begin from our Salesforce org.
- Go to Setup > Certificates and Key Administration.
- Click on on Create Self-Signed Certificates.
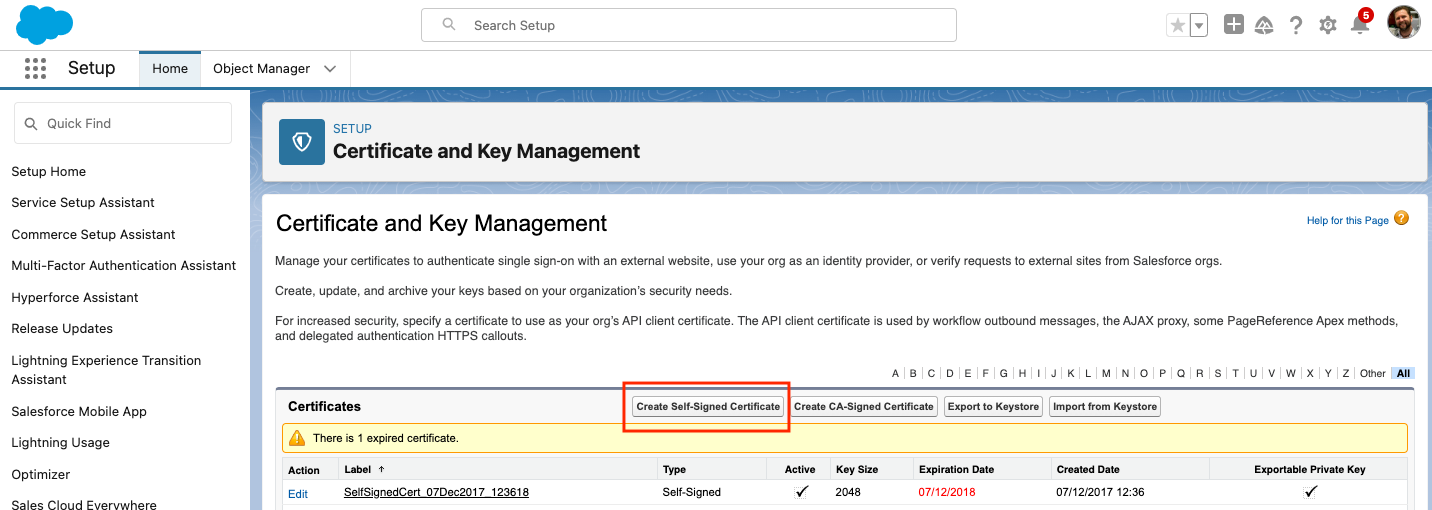
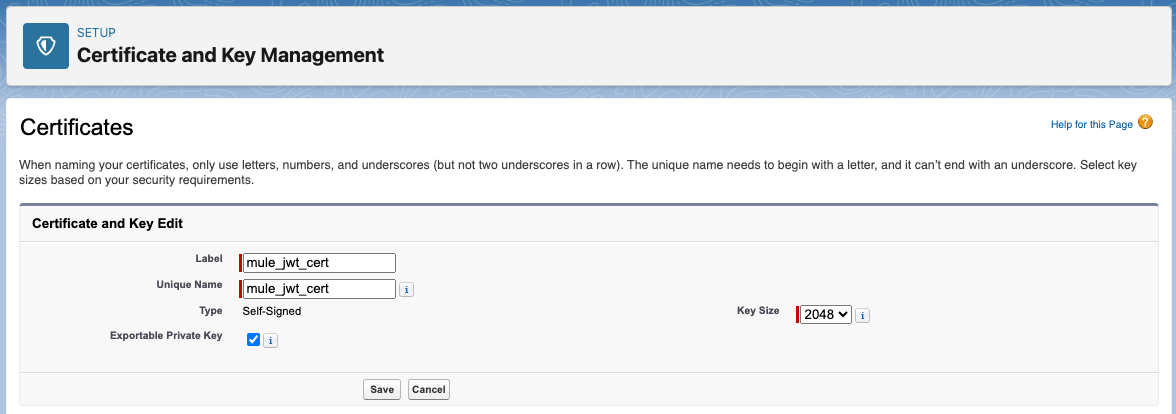
-
After you click on on Save, the certificates can be created and within the subsequent window, you’ll get the main points of your certificates.
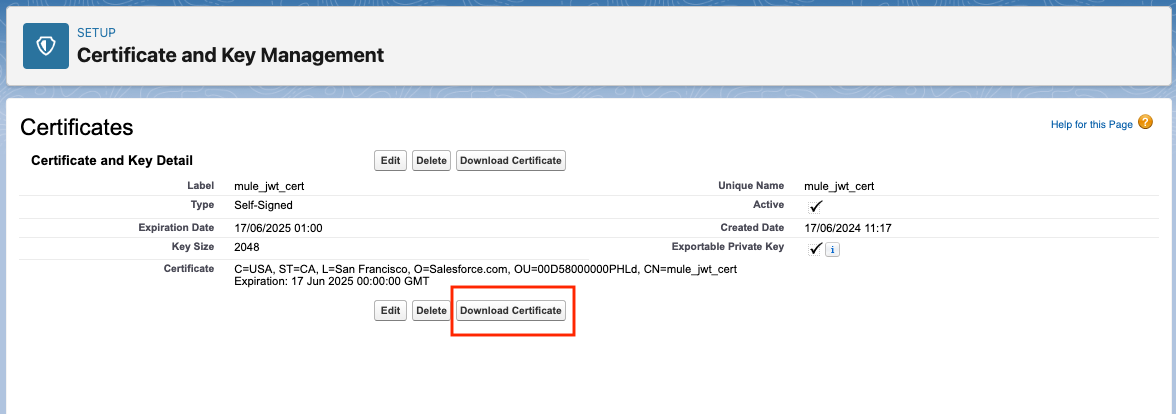
- Click on on Obtain Certificates and reserve it to a separate folder. We’ll use it later.
- We’ll get again to the Certificates and Administration web page. We must always see now our certificates within the checklist of certificates.
- From there, we’ll export our certificates to a keystore. Click on on Export to Keystore.
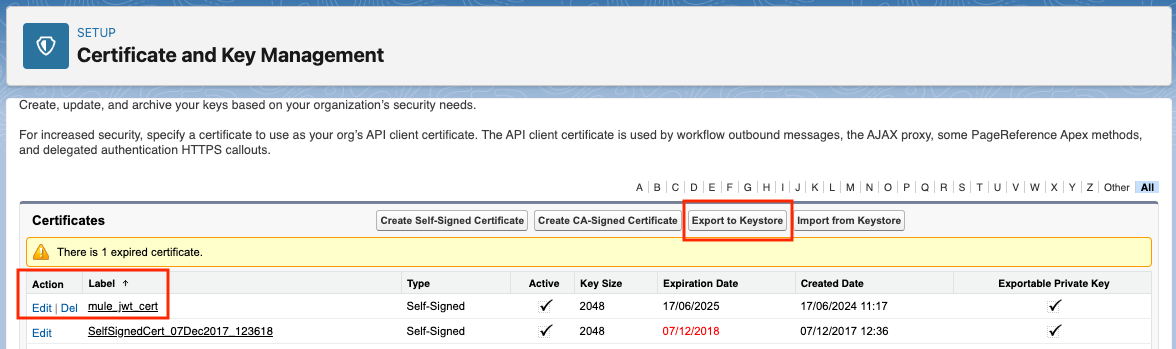
- Present a password on your keystore and bear in mind it. We’ll use it later to arrange the JWT auth within the Mule app.
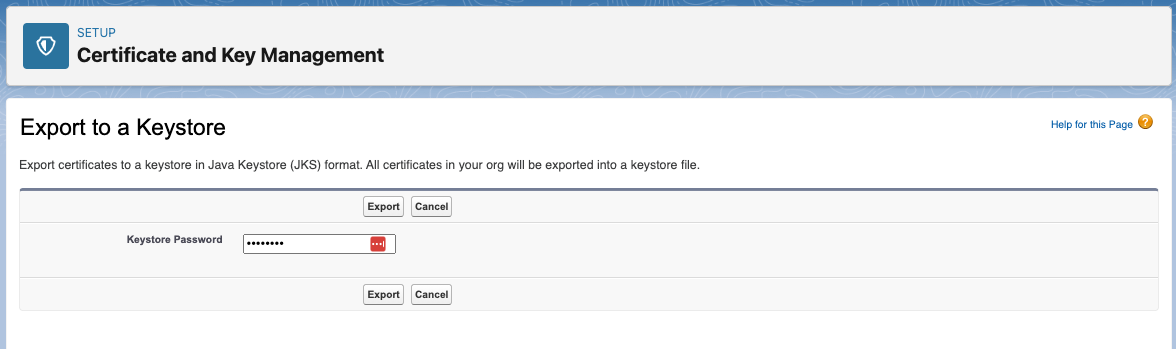
- You’ll get a .jks file. Put it aside to our separate folder.
- This jks ought to have:
- The certificates
- The Personal Key
- The Public Key
- We will confirm that with Key Retailer Explorer, for instance.
2. Create the Linked App in Salesforce
- Begin in your Salesforce org.
- To create the Linked App, we’ll go to Setup > App Supervisor (use Finder).
- Click on on New Linked App within the high proper nook.
- For the remainder of the values, we will depart them as default. Click on Save on the backside of the web page.
- App Supervisor will inform you that it could actually take as much as 10 minutes to get your related app prepared. Click on on Proceed.
-
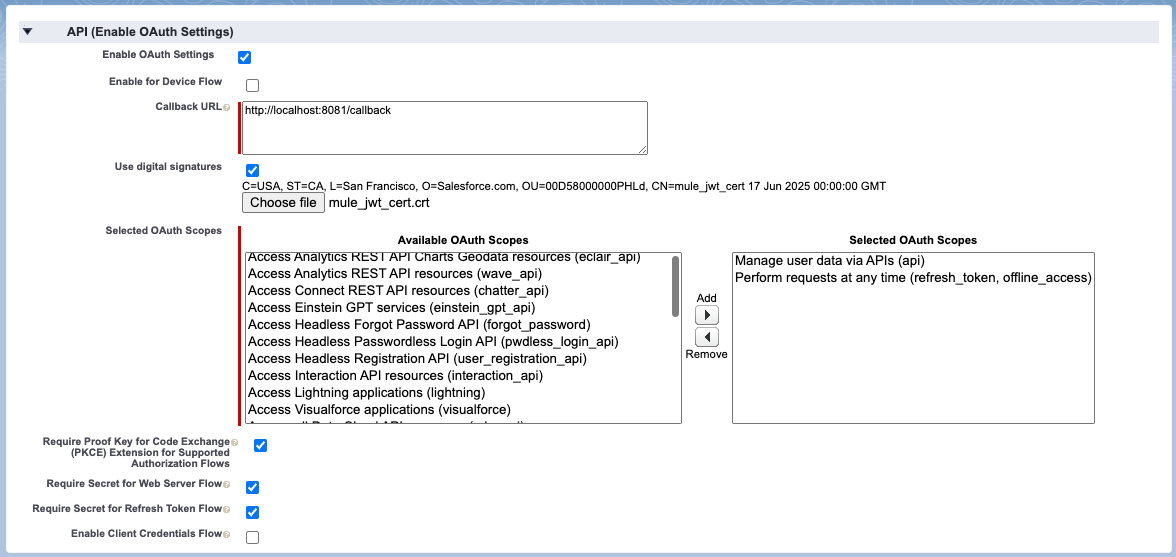
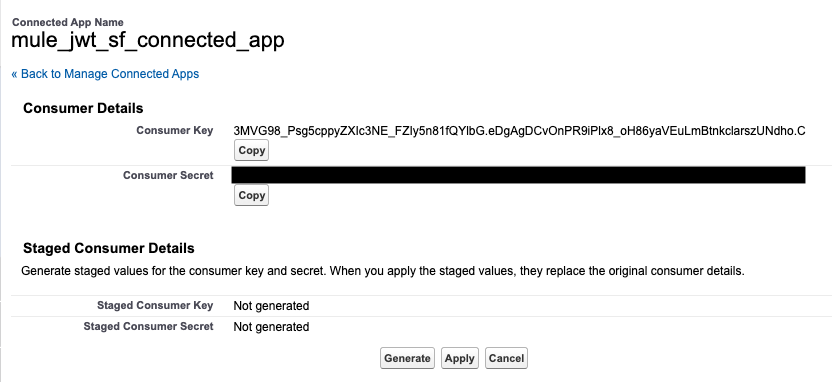
Within the subsequent window, inside the particulars of our related app, we’ll go to the API (Allow OAuth Settings) part and click on on Handle Client Particulars.
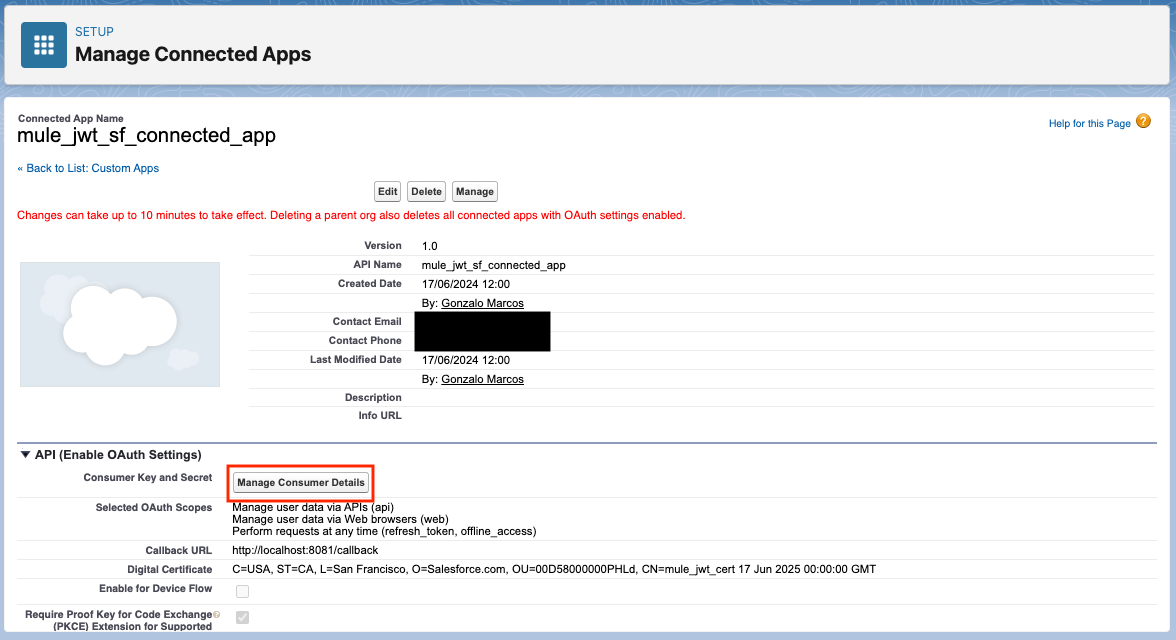
- You’ll be prompted to Confirm Your Id. You’ll want to offer a verification code that has been despatched to your e mail. Enter the code and you must see the Client key and Client Secret of our related app.
- Copy the Client Key. We’ll use it later within the Mule app.
-
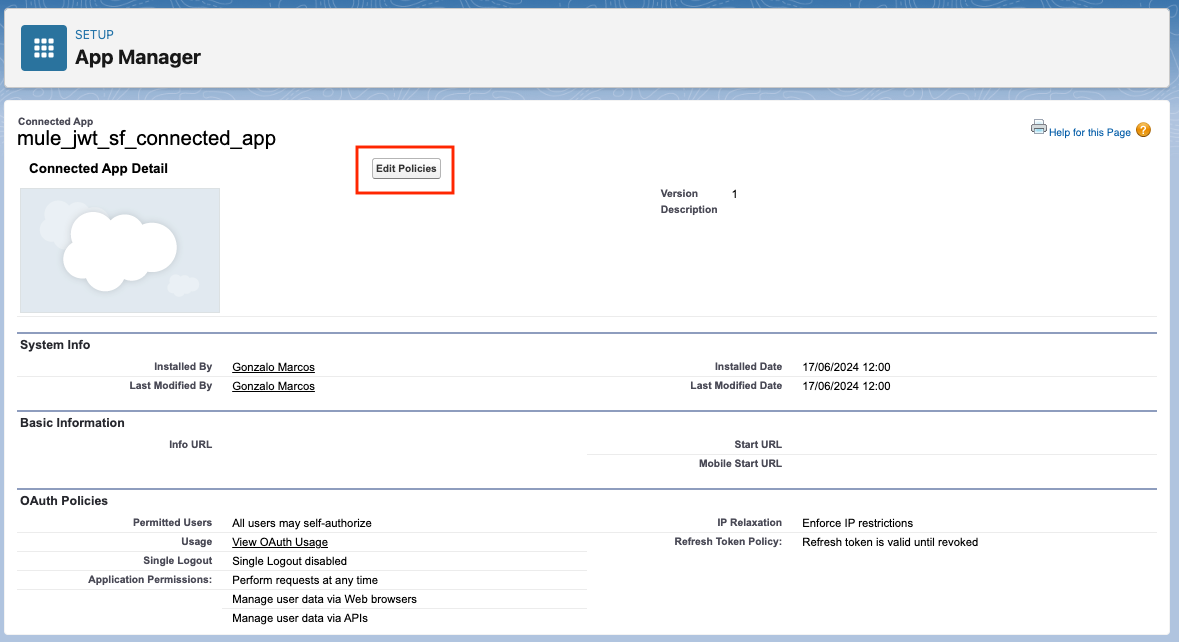
Return to Setup > App Supervisor and from the checklist of apps, discover our Linked App and click on on Handle in the proper dropdown.
-
From right here, click on on Edit Insurance policies.
-
 In Permitted Customers, choose Admin authorized customers are pre-authorized, and click on Save.
In Permitted Customers, choose Admin authorized customers are pre-authorized, and click on Save. 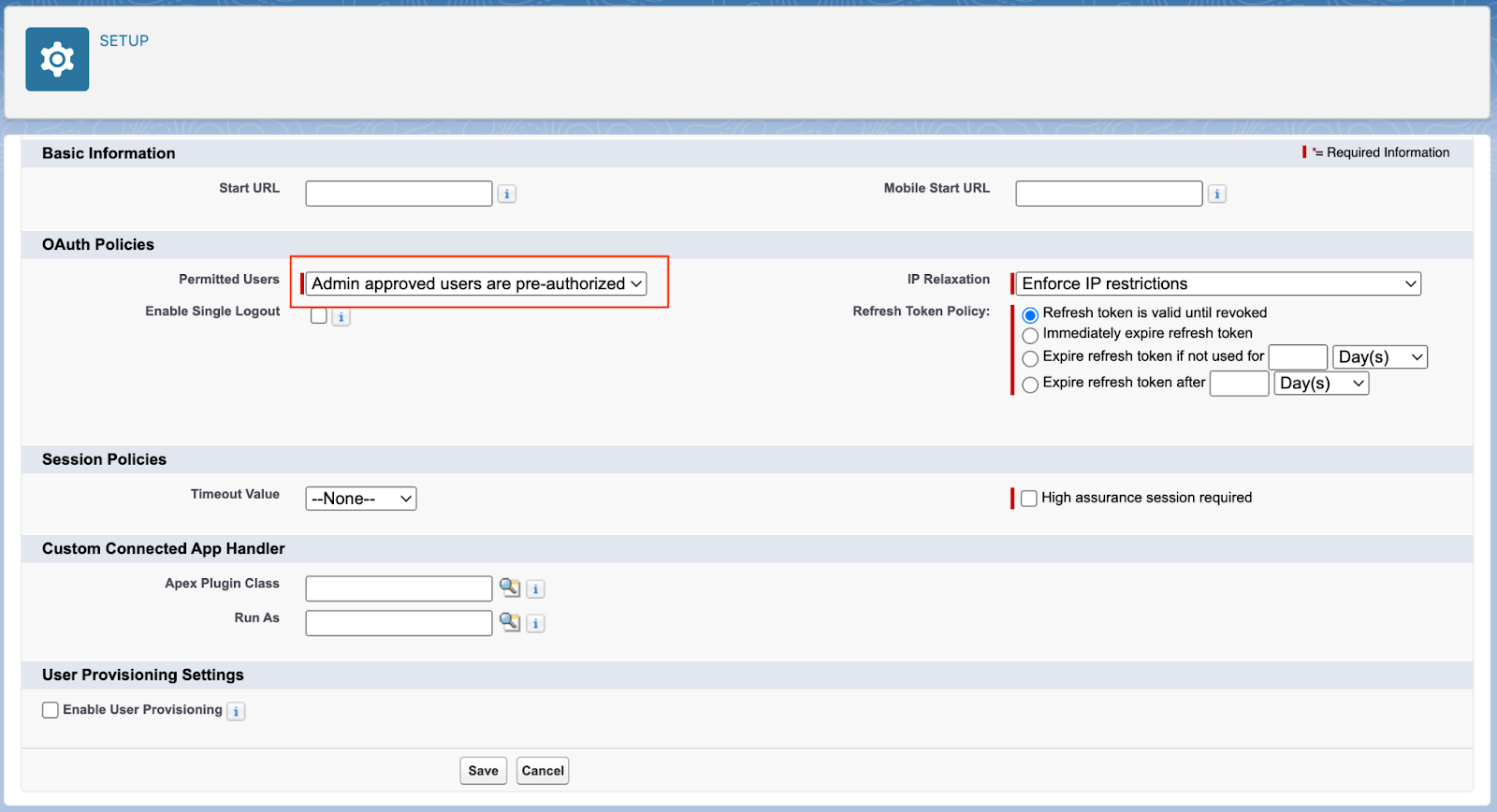 Again to the Handle Linked App web page: Scroll all the way down to the Profiles part and click on Handle Profiles.
Again to the Handle Linked App web page: Scroll all the way down to the Profiles part and click on Handle Profiles.-
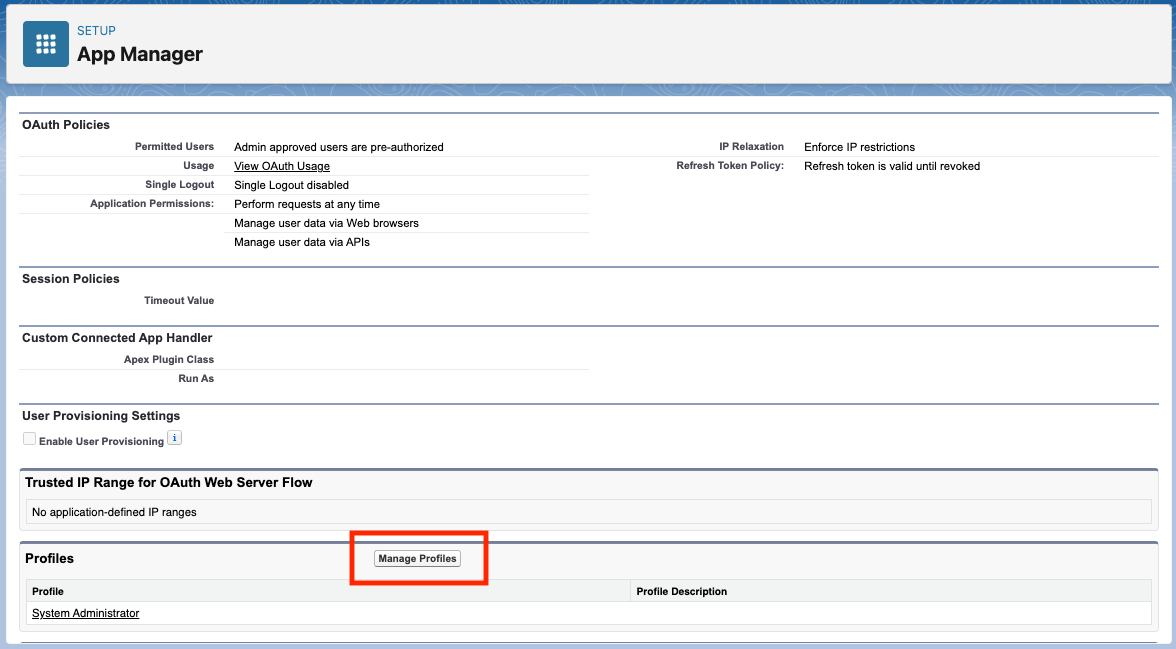
Within the checklist of profiles, choose the profile that ought to have entry to this related app. For the aim of this instance, we’re utilizing a System Admin profile. It is best to use a profile with the minimal permissions required on your use case. Relying in your use case you would possibly want solely a technical consumer otherwise you would possibly have to impersonate an actual consumer, permitting all of the customers related to this profile to propagate their id all the way down to the Mule app.
3. Create the Mule App
- From the Studio, create a New Mule Mission.
- Within the Mule Palette, add the Salesforce Module connector.
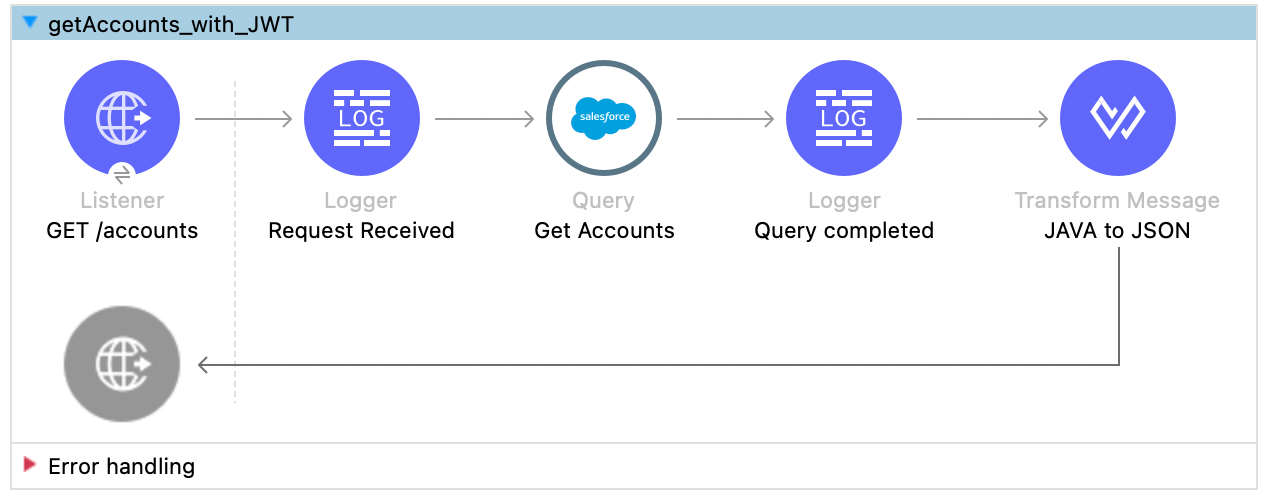
Design the Circulation
- Drag and drop the next components (see screenshot for particulars of the stream):
- A Listener
- 2 Loggers – earlier than and after the Salesforce Question
- A Salesforce Query from the Salesforce Connector
- A Rework Message to transform the result of the stream to JSON
Add the Key Retailer
- From there, go to Sources and add the jks file of our keystore.
- Again to Studio: Should you right-click once more within the identify of our mission and click on Refresh, we must always see our keystore beneath the src/most important/assets folder.
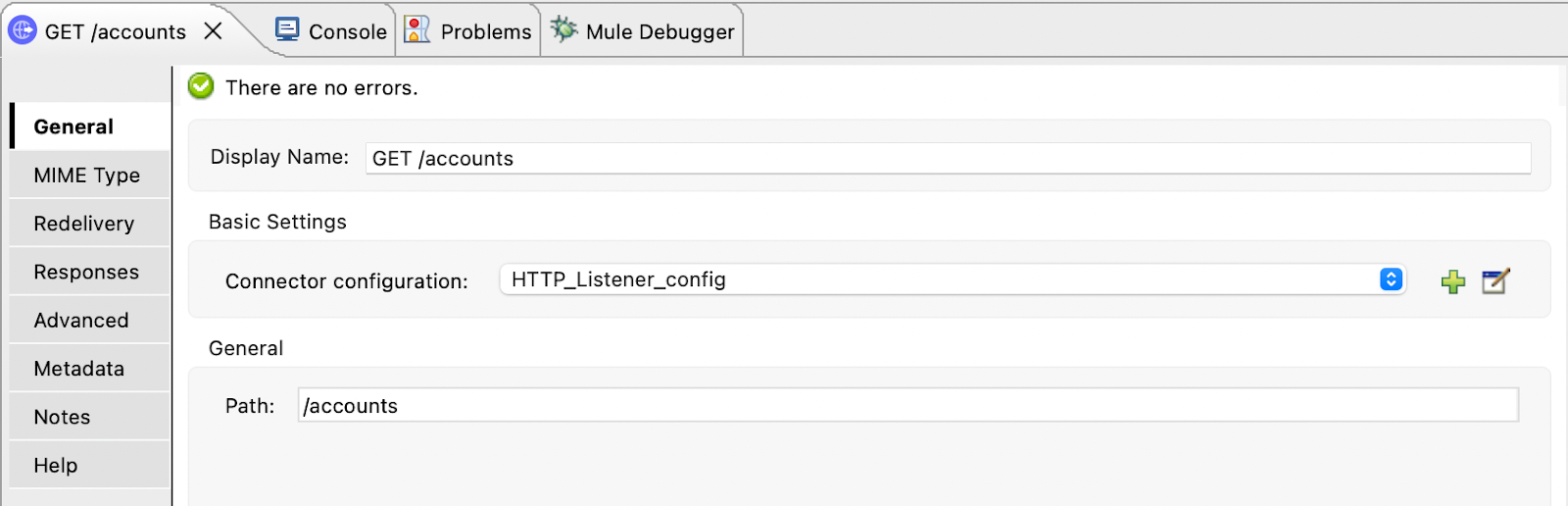
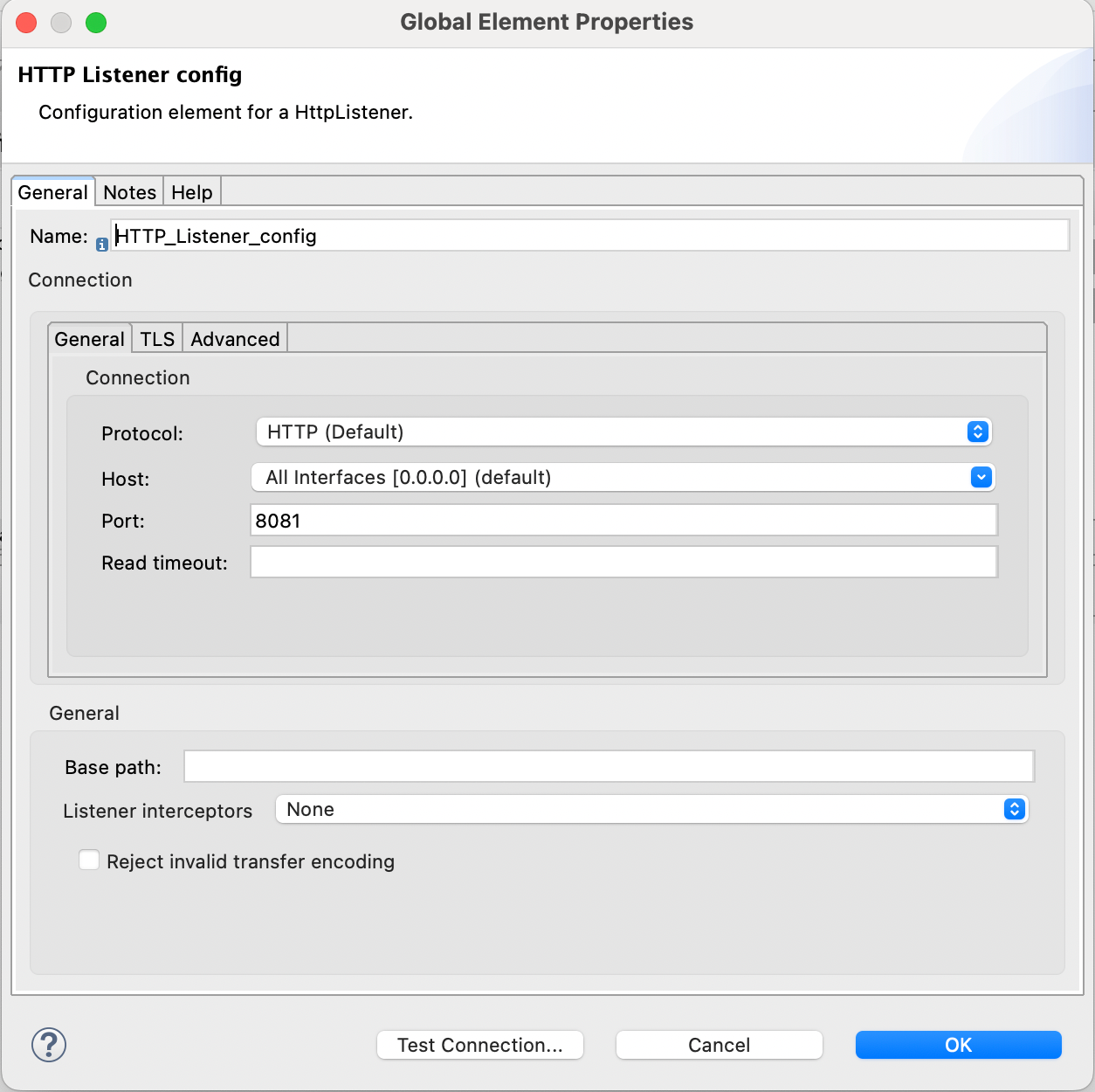
HTTP Listener
- Our Mule app can be listening on port 8081.
- Our endpoint can be /accounts.
Loggers
Salesforce Connector Question
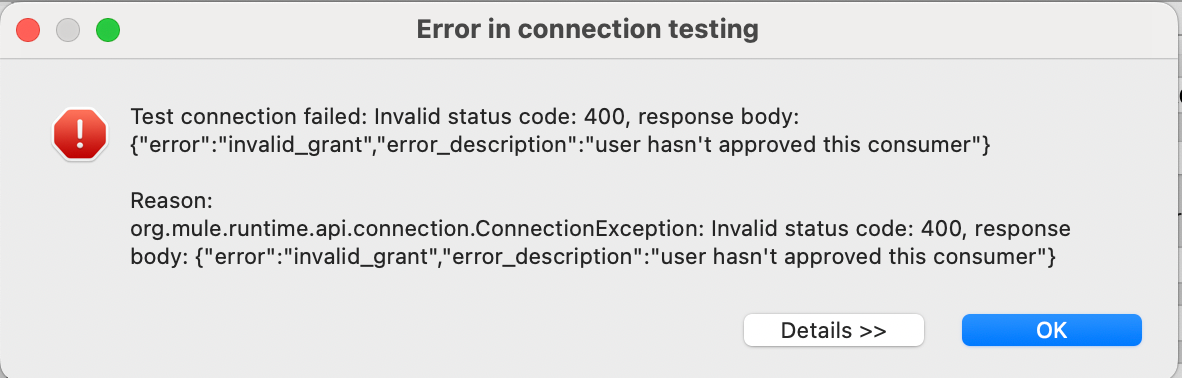
- Should you see the next error, get again to our Salesforce Linked App and evaluate:
- The profiles allowed to make use of the app
- Should you’ve chosen the choice of Admin-approved, customers are pre-authorized.
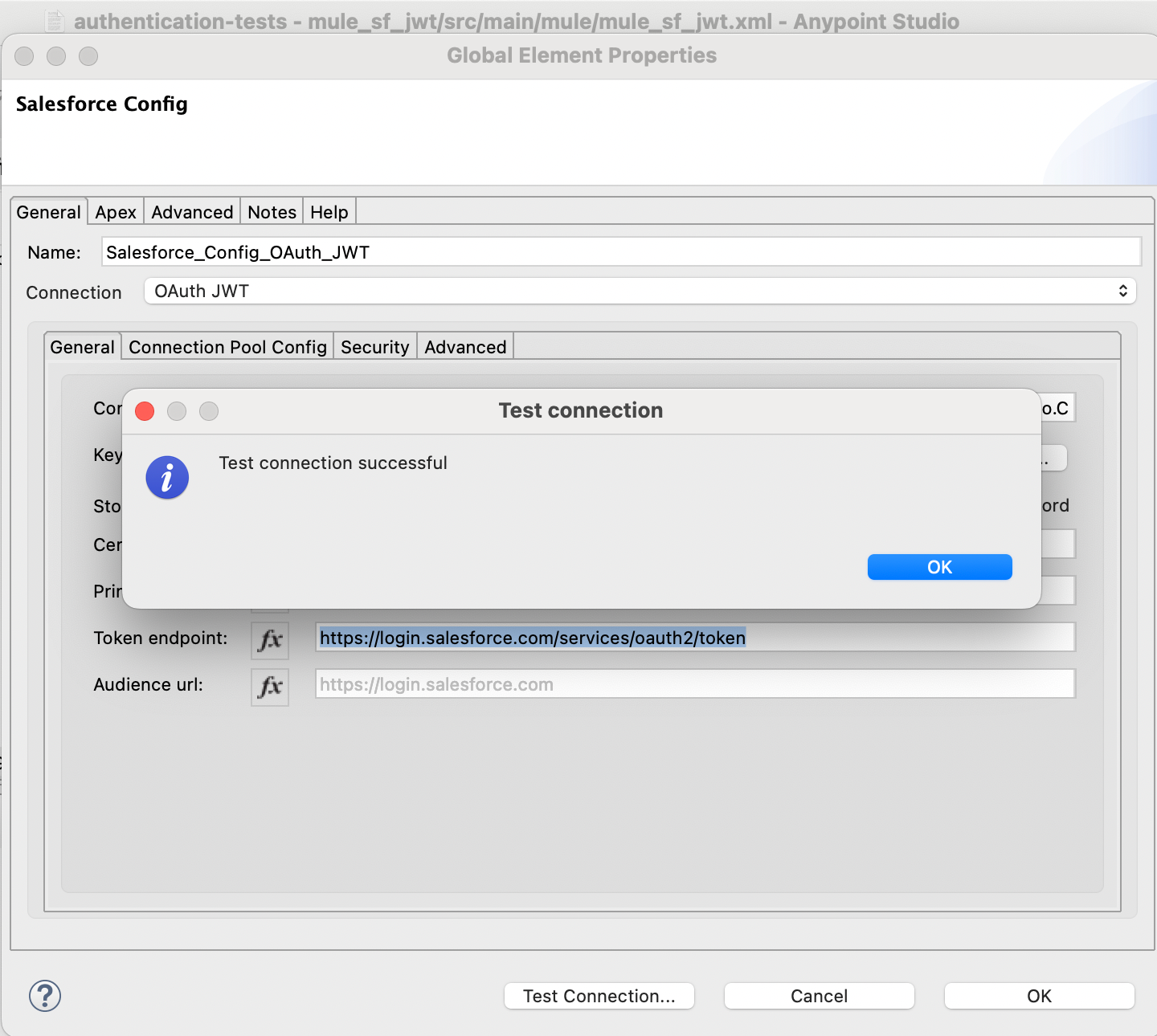
- As soon as we’ve obtained the configuration of the connector and the way it will authenticate with JWT, let’s arrange the Question.
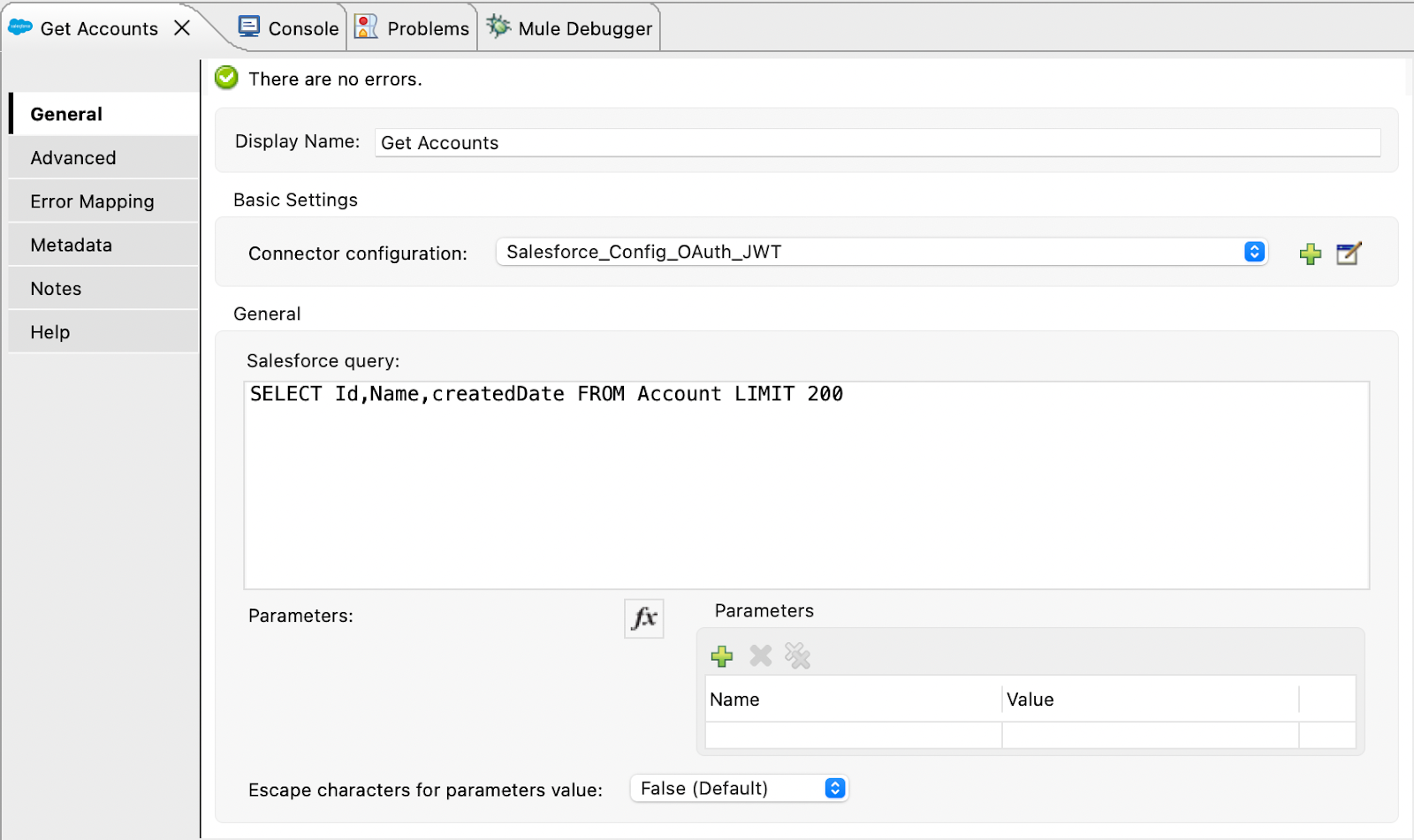
- Click on on the Question Factor and enter the next configuration within the Properties tab:
- Enter a descriptive identify in Show Identify – in our instance, Get Accounts.
- Within the Connector Configuration, decide up the Salesforce Config world factor we’ve simply outlined within the earlier step.
- Within the Salesforce Question, enter the SOQL question to get the data we wish to get from Salesforce. In our case, it’s only a question to Get Accounts.
Transformation
- The output from Salesforce can be in Java format. We’ll add a metamorphosis factor to translate that to JSON format, in order that our API supplies responses in JSON
- Within the remodel factor, simply add the next within the Output:
%dw 2.0
output software/json
---
payload4. Check the App
- From Studio, right-click on the designer canvas and click on Run mission, which is able to deploy our app domestically.
- From our testing software, right here we use Postman. We’ll ship a GET to http://localhost:8081/accounts.
- If every little thing goes effectively, we must always get the checklist of account data.
Within the subsequent submit, we’ll be including mTLS to this configuration.
Video

