Many massive enterprises like retail and banks are adopting open-source Istio service mesh to summary and higher handle the safety and community of microservices. To both deal with value, obtain HA/DR, or enhance latency, they apply multi-cloud and multi-cluster methods of their manufacturing system.
Implementing Istio in a multi-cloud surroundings could be tough, and designers usually take time for experimentation. On this weblog, we’ll talk about numerous methods to realize multi-cloud and multicluster configuration for Istio implementation and likewise information you thru the steps to arrange primary-primary multicluster Istio in EKS and AKS
Multicluster Istio Deployment Fashions
Istio could be configured by deploying it into single or a number of clusters, similar or totally different networks, single or a number of management planes, or single or a number of meshes. To attain HA/DR or enhance latency, Istio is deployed into a number of clusters. There are 4 common deployment fashions for deploying Istio to achieve HA/DR and make seamless service discoverability in your manufacturing techniques.
Istio Deployment fashions
- Main-remote on the identical community: One Istio management aircraft is deployed in a number of cluster(s) (or known as Main) and serves as a grasp. All different clusters (known as Distant) could be introduced underneath the management of grasp Istio.
- Main-remote on totally different networks: Main-Distant setup with clusters in a special community; i.e., totally different zone or multi-cloud
- Multi-primary on the identical community: Every cluster within the manufacturing system may have one Istio management aircraft, however they may all be related and conscious of one another. Observe that there could be a number of distant clusters for every main cluster. Consult with Determine 1.
- Multi-primary on totally different networks: Multi-primary setup for clusters in numerous zones/areas or multi-cloud clusters.
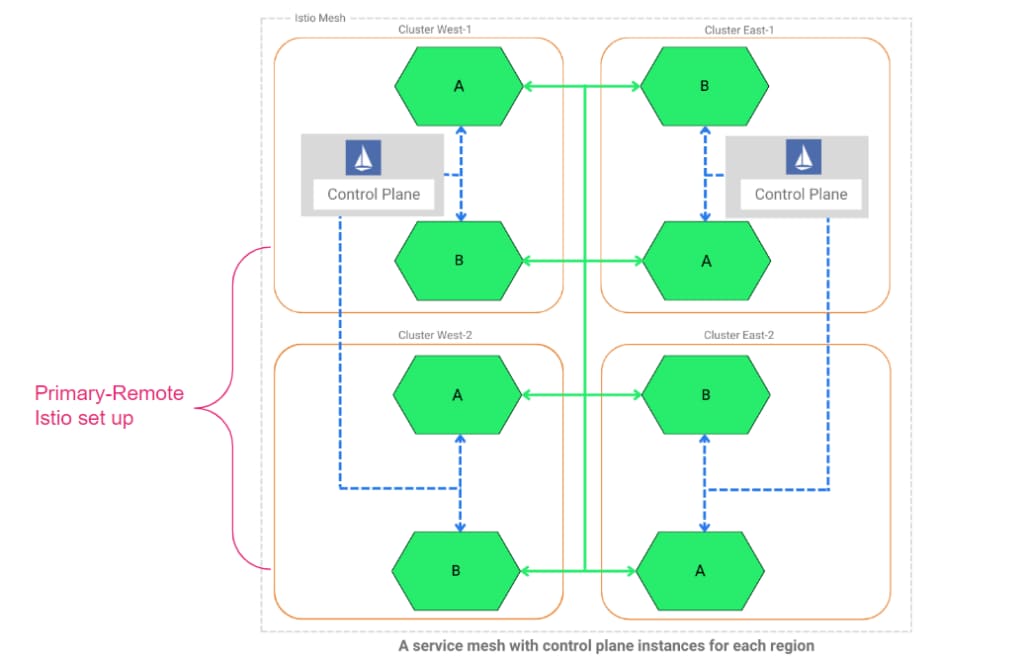
Determine 1: Depiction of Istio configured in each Main-primary and Main-remote model
We had mentioned organising Istio within the Main-remote cluster in GKE and AKS earlier. On this weblog, we’ll concentrate on the Multi-Main Istio setup.
Structure To Setup Multi-Main Istio in Multicluster Panorama
The best way to realize a multi-primary Istio setup is to put in Istio management planes in every cluster (as proven in Determine 2) after which have these clusters entry the API server of one another. Thus, there might be a single service mesh (though totally different Istio management planes), and the service discovery might be seamless within the mesh. The Istio management planes don’t intervene with one another, so the failure of 1 Istio management aircraft is not going to have an effect on different main clusters.
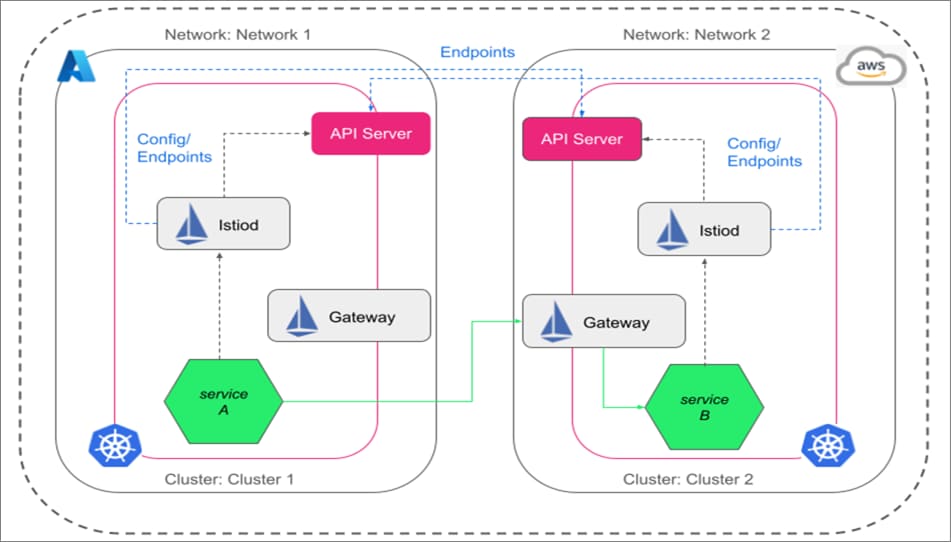
Determine 2: Multi-primary Istio arrange in AKS and EKS
Advantages of Multi-Main Istio
Key advantages of organising multi-primary Istio are:
- Improved availability: If a management aircraft fails, the harm might be restricted to workloads or knowledge aircraft managed by that management aircraft.
- Configuration isolation: Configuration could be made to at least one cluster, zone, or area with out impacting others.
- Canary or blue/inexperienced deployment: You’ve gotten extra fine-grained management over configuration rollout, corresponding to canary or blue/inexperienced, by deploying them right into a sub-section of the mesh solely.
- Managed visibility and entry with RBAC: Since all of the companies in a number of clusters can introduced underneath one mesh with a multi-primary setup, you possibly can implement fine-grained authorization for the developer and DevOps workforce worldwide. You possibly can outline the least privilege for entry to a selected cluster or service in the entire mesh from a central level. Observe that you need to create and deploy authorization insurance policies in every main cluster, which might be utilized by the grasp management aircraft.
Steps to Configure Multi-Main Istio in EKS and AKS
We are going to talk about a step-by-step information to configure multi-primary Istio on this part.
Prerequisite
- Use certificates issued by the identical Root CA – a vital step to ascertain belief between the 2 clusters. Since Istio generates its certificates, two Istiod in respective clusters may have their model of the certificates, and clusters can’t belief and talk with one another. For enterprise utilization, it’s endorsed to maintain the Root certificates secured and secure, say, in Vault.
- Have two separate clusters in numerous networks. We’ve thought of EKS and EKS clusters for the multi-primary setup.
You possibly can entry all of the Git multi-primary Istio yaml information.
Step 1: Create the Root Certificates and Cluster Certificates
Step 1.1
You possibly can run the next command to generate the widespread root certificates. We’ve used Istio instruments.
make -f istio-1.20.3/instruments/certs/Makefile.selfsigned.mk root.ca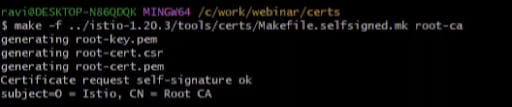
Step 1.2
Now you possibly can create cluster certificates by operating the next command. We’ve named our certificates as webinar-cluster and eks-cluster.
make -f istio-1.20.3/instruments/certs/Makefile.selfsigned.mk webinar-cluster-cacertsmake -f istio-1.20.3/instruments/certs/Makefile.selfsigned.mk eks-cluster-cacerts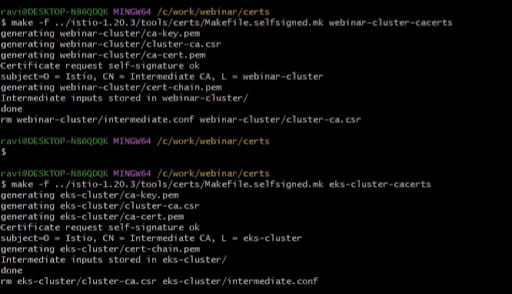
Step 2: Create a Namespace in Every Cluster and Create Secrets and techniques From the Certificates
Step 2.1
We’ve created a namespace known as istio-system in AKS and EKS clusters. We’ve used aks-primary-namespace-prep.yaml, and eks-primary-namespace-prep.yaml to create them.
Command:
kubectl create -f aks-primary-namespace-prep.yaml –context=$AKS
kubectl create -f eks-primary-namespace-prep.yaml –context=$EKSStep 2.2
We are going to create secrets and techniques for the istio-system namespace in every cluster by operating the command:
kubectl create secret generic cacerts -n istio-system –context=$AKS
–from-file=certs/webinar-cluster/ca-cert.pem
–from-file=certs/webinar-cluster/ca-key.prem
–from-file=certs/webinar-cluster/root-cert.pem
–from-file=certs/webinar-cluster/cert-chain.pem
kubectl create secret generic cacerts -n istio-system –context=$EKS
–from-file=certs/eks-cluster/ca-cert.pem
–from-file=certs/eks-cluster/ca-key.prem
–from-file=certs/eks-cluster/root-cert.pem
–from-file=certs/webinar-cluster/cert-chain.pem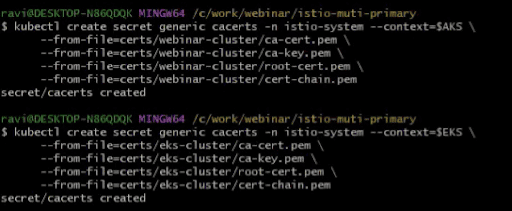
Step 3: Set up Istio Utilizing HELM
Step 3.1
Add the HELM repo by executing the next instructions.
helm repo add istio https://istio-release.storage.googleapis.com/charts
helm repo replaceAs soon as the helm repo is up to date, we’ll set up Istio utilizing HELM in every cluster, in 3 sequential steps: first set up Istio-base, then Istiod, and eventually east-west gateway.
Step 3.2
Please comply with the under instructions to put in istio-base to the istio-system namespace of every cluster. We are going to set up first in AKS after which in EKS (however you possibly can select to run the instructions parallelly as properly).
helm set up istio-base istio/base -n istio-system –kube-context=$AKS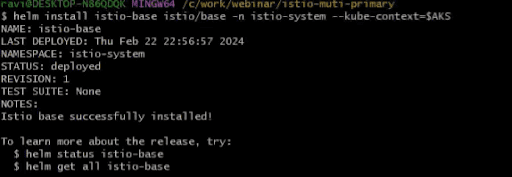
Now you can set up istio-base within the EKS cluster by operating the next units of instructions.
helm set up istio-base istio/base -n istio-system –kube-context=$AKSNow, you possibly can set up istiod by operating the next instructions.
helm set up istiod istio/istiod -n istio-system –set world.meshID=mesh1 –set world.multiCluster.ClusterName=webinar-cluster –set world.community=network1 –kube-context=$AKSIt’s best to see an output like under.
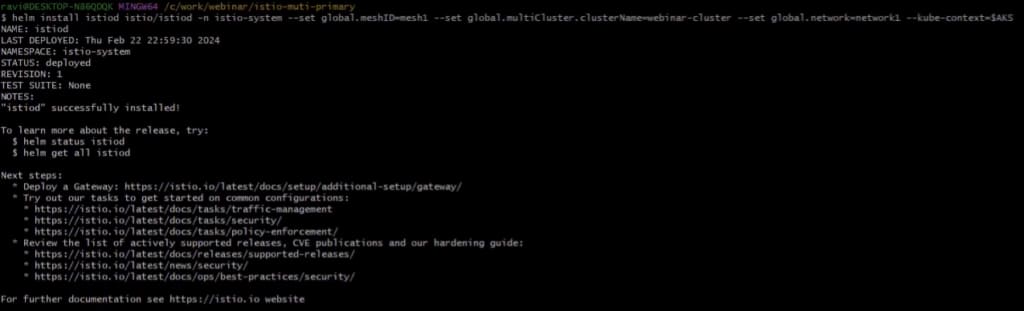
Now, we have to set up east-west gateway utilizing the next command:
helm set up istio-eastwestgateway istio/gateway -n istio-system –set networkGateway=network1 –set labels.``topology.istio.io/community”=network1 –kube-context=$AKSIt’s best to see an output like this:
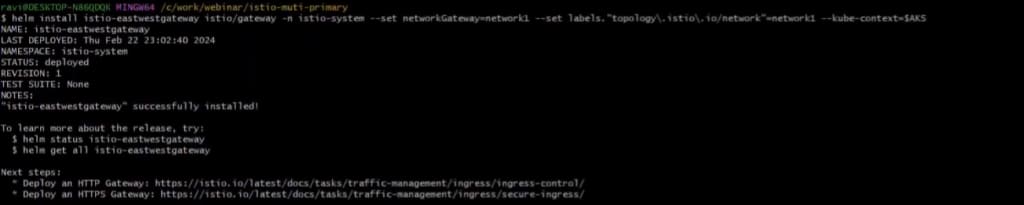
Run the under instructions to put in Istio-base, istiod, and east-west gateway in EKS.
helm set up istio-base istio/base -n istio-system –kube-context=$EKShelm set up istiod istio/istiod -n istio-system –set world.meshID=mesh1 –set world.multiCluster.ClusterName=eks-cluster –set world.community=network2 –kube-context=$EKShelm set up istio-eastwestgateway istio/gateway -n istio-system –set networkGateway=network2 –set labels.``topology.istio.io/community”=network2 –kube-context=$EKS
You possibly can confirm if the installations are correct and verify the pods within the istio-system namespace in every cluster.
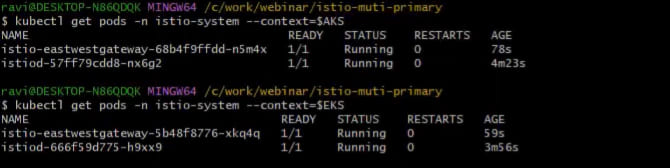
Step 4: Established the Belief Between Two Main Clusters: EKS and AKS
Step 4.1
On this step, we’ll create a gateway useful resource in every cluster in order that communication can occur between them by way of the eastwest gateway. Consult with the expose-services.yaml.
apiVersion: networking.istio.io/v1alpha3
form: Gateway
metadata:
identify: cross-network-gateway
namespace: istio-system
spec:
selector:
istio: eastwestgateway
servers:
- port:
quantity: 15443
identify: tls
protocol: TLS
tls:
mode: AUTO_PASSTHROUGH
hosts:
- "*.local"You run the next command to create eastwest gateway useful resource:
kubectl apply -f expose-services.yaml –context=$AKS
kubectl apply -f expose-services.yaml –context=$EKSStep 4.2
To begin the safe communication, we have to create a secret and entry the API server of every cluster to the opposite.
We will execute the next command to create a secret in AKS and apply it within the EKS.
istioctl create-remote-secret –identify=webinar-cluster –context=$AKS > aks-api-server.yaml
istioctl create-remote-secret –identify=eks-cluster –context=$EKS > eks-api-server.yamlWe will now apply the secrets and techniques in respective clusters by executing the next instructions:
kubectl apply -f aks-api-server.yaml –context=$EKS
kubectl apply -f eks-api-server.yaml –context=$AKSBy now, we’ve got established the belief between the 2 clusters, and communication now occurs utilizing the Istio eastwest gateway. We are going to confirm the communication by putting in a couple of companies within the subsequent step.
Step 5: Confirm and Validate the Multicluster Communication in Multi-Main Istio Setup
We are going to create a brand new namespace (say take a look at) in every cluster and make it Istio-enbaled. We are going to deploy companies in take a look at namespace in every cluster and provoke communication.
Step 5.1
We are going to create a brand new namespace in every cluster.
kubectl create ns take a look at –context=$EKS
kubectl create ns take a look at –context=$AKSThen we’ll label the take a look at namespace in every cluster as Istio-enbaled.
kubectl label ns take a look at istio-injection=enabled –context=$AKS
kubectl label ns take a look at istio-injection=enabled –context=$EKSStep 5.2
We are going to deploy the helloworld-deployment-v1 yaml in AKS, helloworld-deployment-v2 yaml in EKS, and hello-world service in each clusters, respectively. We will even deploy sleep.yaml to twist the applying and take a look at the communication.
Execute the command to deploy the helloworld and sleep companies in AKS and EKS, respectively.
kubectl apply -f helloworld-service.yaml -n take a look at –context=$AKS
kubectl apply -f helloworld-deployment-v1.yaml -n take a look at –context=$AKSkubectl apply -f helloworld-service.yaml -n take a look at –context=$EKS
kubectl apply -f helloworld-deployment-v2.yaml -n take a look at –context=$EKSkubectl apply -f sleep.yaml -n take a look at –context=$AKS
kubectl apply -f sleep.yaml -n take a look at –context=$EKSConfirm if all of the pods and companies are created, and your output ought to look one thing under:
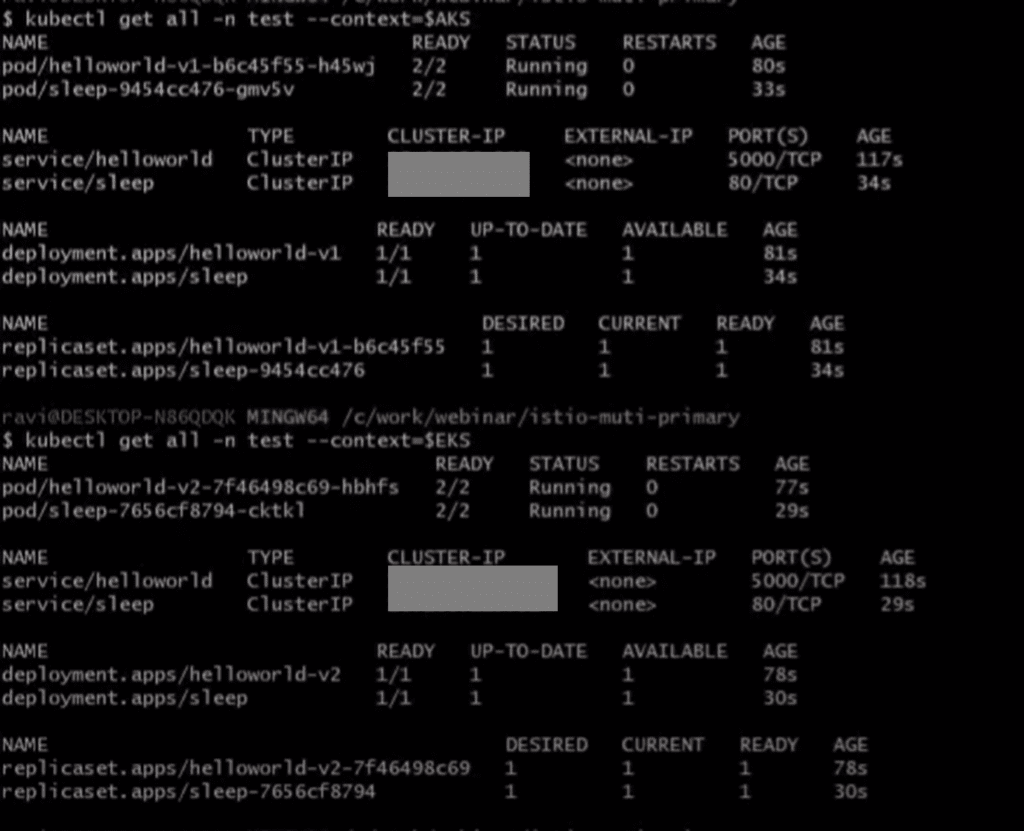
Step 5.3
We are going to confirm the communication by sending a curl request from one of many sleep pods in AKS. You possibly can run the next command to get into one of many sleep pods in AKS.
kubectl exec it > -n take a look at –context=$AKSTo twist helloworld in AKS and EKS clusters from sleep pod in AKS, we have to execute the under instructions:
curl helloworld:5000/hiyaIt’s best to get a response from the helloworld service within the AKS and EKS cluster as properly. Right here is the output. Helloworld service responds from V1 and V2 deployments in AKS and EKS clusters.
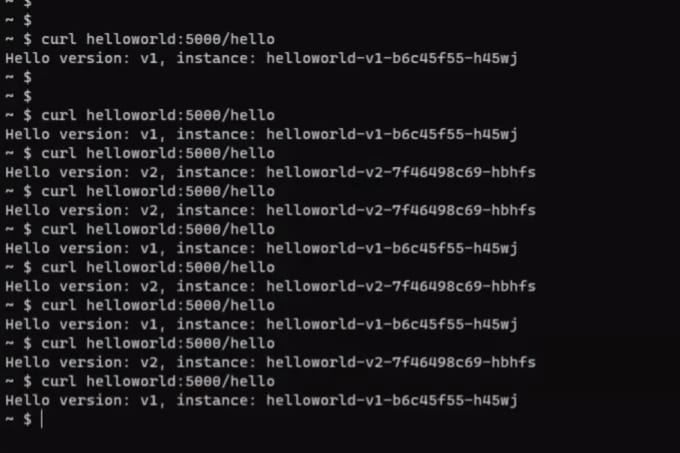
Step 5.4
Equally, for those who attempt to get right into a sleep pod within the take a look at namespace in EKS cluster and attempt to curl helloworld service, then you definately would get a response from the hello-deployment V1 and V2 deployed within the AKS and EKS clusters.
Widespread Questions of Istio Multi-Main Implementation
1. How Is Multi-Main Completely different From Implementing Istio Into Particular person Clusters?
If the Istio management aircraft is applied individually, they may talk with every wrt load balancing or site visitors dealing with. In every of those situations, unbiased Ingress might be liable for executing the duty. Moreover, we would require an exterior load balancer to distribute the site visitors.
One other drawback is service discovery is not going to occur. Companies in cluster-1 (or say mesh-1) is not going to pay attention to the Companies operating in cluster-2 (say, mesh2). In that case, builders should proper separate logic to deal with the communication.
2. Can We Not Deal with the HA Case of Multi-Main Utilizing Main-Distant?
Sure, you possibly can deal with however the danger of the primary-remote is that if the management aircraft fails within the main cluster, then all of the community and safety insurance policies applied within the knowledge aircraft within the cluster-2 (distant cluster) will cease working.
Video
If you’re , you possibly can watch the whole video:

