eBPF is a groundbreaking know-how that lets you run sandboxed packages inside the Linux kernel. This gives a secure and environment friendly approach to prolong the kernel’s capabilities with out modifying its supply code.
Excessive-Stage Overview
Under is an summary of the stack:
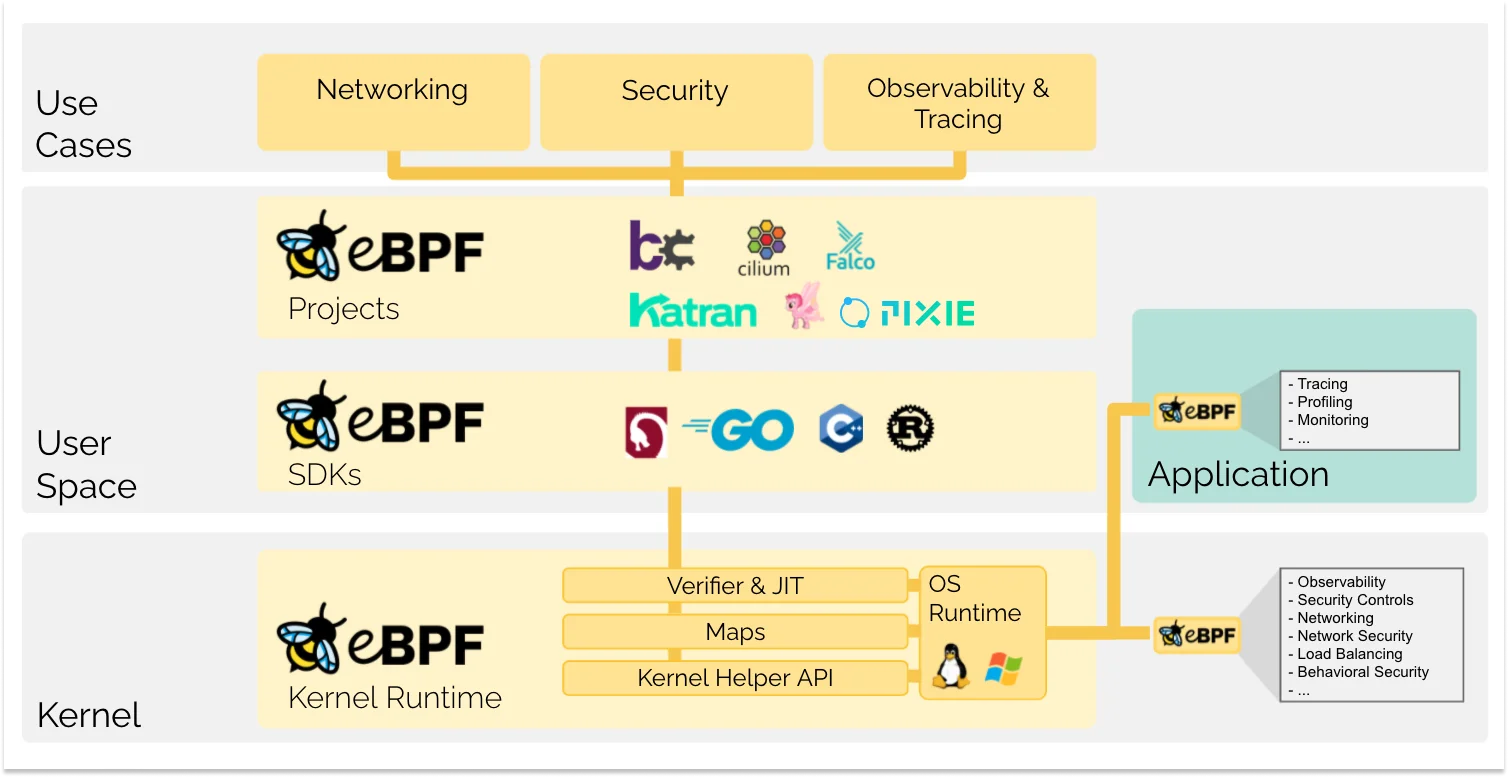
Interception Factors and Probes
eBPF packages are triggered by occasions and execute when the kernel or an software reaches a specified interception level. Customary interception factors embody system calls, operate begins/ends, kernel tracepoints, community occasions, amongst others.
Ought to there be no current interception level for a selected requirement, one has the choice to ascertain a kernel probe (kprobe) or person probe (uprobe), enabling the attachment of eBPF packages just about anyplace inside the kernel or person purposes.
As soon as the suitable interception level is pinpointed, the eBPF program might be launched into the Linux kernel by the bpf system name, generally facilitated by one of many eBPF libraries.
Usually, eBPF is employed in a roundabout way, however by frameworks resembling Cilium, bcc, or bpftrace. These frameworks supply a layer of abstraction over eBPF, eradicating the necessity to write packages from scratch and as an alternative permitting for the definition of intent-based directives which can be then executed through eBPF.
In situations the place no such abstraction layer is accessible, it turns into essential to writer packages instantly. The Linux kernel mandates that eBPF packages be submitted as bytecode. Though it is technically possible to code in bytecode instantly, the prevalent observe is to make use of a compiler suite like LLVM to transmute pseudo-C code into eBPF bytecode.
Load, Verification, and Compilation
Upon loading into the Linux kernel, the eBPF program undergoes a two-stage course of earlier than being linked to the chosen interception level.
Firstly, a verification section confirms the security of the eBPF program. This section checks that this system adheres to numerous standards, resembling:
- The entity loading the eBPF program possesses the mandatory capabilities (privileges). Within the absence of enabled unprivileged eBPF, solely privileged entities can load eBPF packages.
- This system is steady and doesn’t jeopardize the system.
- This system is assured to finish its execution (i.e., it will not enter an infinite loop, thereby stalling additional processes).
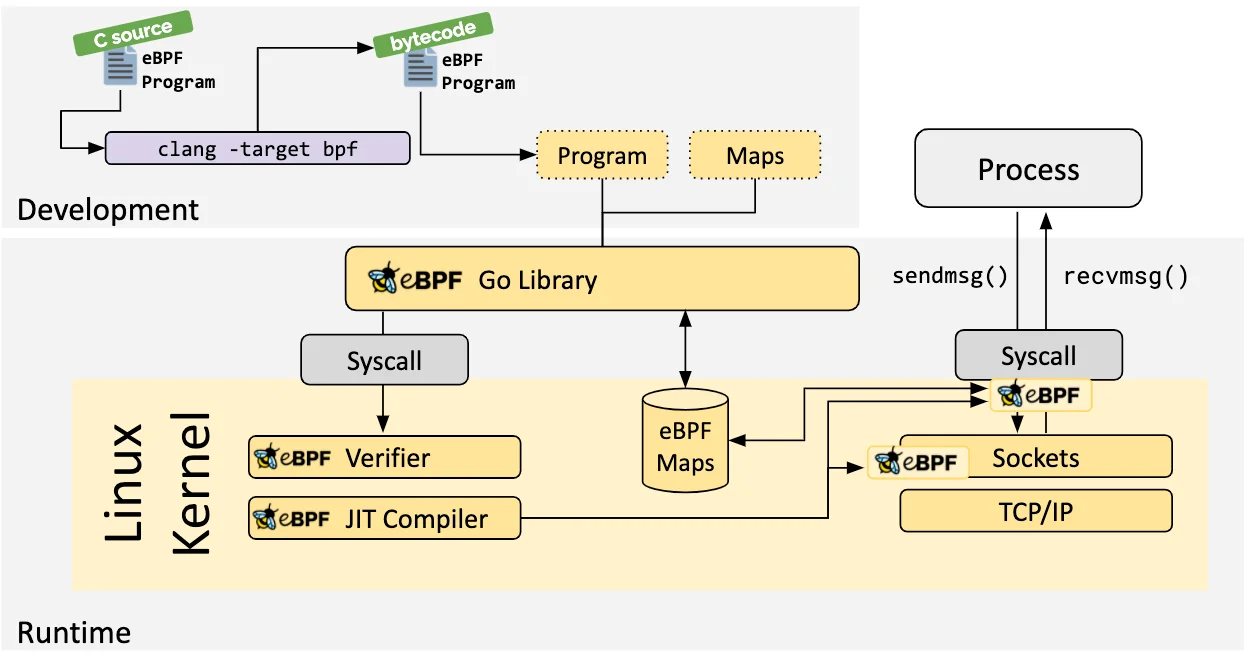
The Simply-in-Time (JIT) compilation step interprets the generic bytecode of this system into the machine particular instruction set to optimize execution velocity of this system. This makes eBPF packages run as effectively as natively compiled kernel code or as code loaded as a kernel module.
eBPF maps are like information constructions that may be accessed each from inside eBPF packages and from user-space purposes utilizing a system name. This permits eBPF packages to share data and retailer state.
Why Use eBPF for O11y?
- Efficiency: Since eBPF runs within the kernel and doesn’t want to modify between person house and kernel house incessantly, it’s extremely environment friendly and has very low overhead.
- Flexibility: eBPF can be utilized for numerous use circumstances like community monitoring, safety enforcement, debugging, and efficiency tuning.
- Non-intrusive: eBPF can collect detailed system information with out modifying software code or rebooting the system.
Instance: Tracing File Opens With eBPF
Think about you wish to monitor and hint each time a course of opens a file in your system. eBPF can obtain this by hooking into the openat() syscall (a system name used to open information in Linux) and offering real-time insights with out affecting system efficiency.
Here is a easy step-by-step instance utilizing bcc (BPF Compiler Assortment), a well-liked front-end for writing eBPF packages:
Step 1: Set up bcc
First, it is advisable to set up bcc instruments in your system. For instance, on Ubuntu:
sudo apt-get set up bpfcc-tools linux-headers-$(uname -r)Step 2: Write a Easy eBPF Program
This eBPF program traces the openat() syscall, logs the method ID (PID), course of identify, and file path every time a file is opened.
#!/usr/bin/python
from bcc import BPF
# eBPF program that hooks into the openat syscall
bpf_code = """
#embody
#embody
struct data_t {
u32 pid;
char comm[TASK_COMM_LEN];
char fname[256];
};
BPF_PERF_OUTPUT(occasions);
int trace_openat(struct pt_regs *ctx, int dfd, const char __user *filename, int flags) {
struct data_t information = {};
// Seize course of ID and identify
information.pid = bpf_get_current_pid_tgid() >> 32;
bpf_get_current_comm(&information.comm, sizeof(information.comm));
// Seize file identify
bpf_probe_read_user(&information.fname, sizeof(information.fname), filename);
// Ship the information to user-space
occasions.perf_submit(ctx, &information, sizeof(information));
return 0;
}
"""
# Load the eBPF program
b = BPF(textual content=bpf_code)
# Connect eBPF program to the openat syscall
b.attach_kprobe(occasion="sys_openat", fn_name="trace_openat")
# Operate to print the output
def print_event(cpu, information, dimension):
occasion = b["events"].occasion(information)
print(f"PID: {event.pid}, Process: {event.comm.decode('utf-8')}, File: {event.fname.decode('utf-8', 'replace')}")
# Open a perf buffer to obtain occasions from kernel house
b["events"].open_perf_buffer(print_event)
# Repeatedly hear for occasions and print them
whereas True:
b.perf_buffer_poll() Step 3: Rationalization of the Code
- Hooking the syscall: The eBPF program hooks into the
openat()system name utilizingkprobes(kernel probes). This permits this system to execute each time any course of callsopenat()to open a file. - Information assortment: The eBPF program captures the method ID, course of identify (
comm), and the identify of the file being opened. It makes use of helper features likebpf_get_current_comm()to get the method identify andbpf_probe_read_user()to learn the filename from person house. - Sending information to user-space: The eBPF program makes use of a perf buffer (
occasions.perf_submit()) to ship this information from the kernel house again to the user-space, the place we print the data. - Person-space script: The Python script attaches the eBPF program to the
openat()syscall and prints out the information collected from kernel house, resembling the method identify and file being opened.
Step 4: Working the eBPF Program
When you run the script with root privileges, you will note output like this:
PID: 12345, Course of: bash, File: /and so forth/passwd
PID: 12346, Course of: vim, File: /residence/person/file.txt
PID: 12347, Course of: python, File: /tmp/log.txtWhich means that each time any course of opens a file, the script captures and shows:
- PID: Course of ID that opened the file
- Course of identify: The identify of the method (e.g.,
bash,vim) - File path: The trail of the file being opened
This instance exhibits how eBPF can be utilized for real-time monitoring of system occasions (on this case, file opens) with minimal efficiency influence.
Greatest Practices for Non-Invasive Observability With eBPF
1. Begin Small and Regularly Improve Scope
Start by observing high-level metrics (e.g., syscall counts or community site visitors) reasonably than capturing detailed data resembling particular person operate calls. When you’re assured about efficiency impacts, regularly broaden to extra detailed probes.
2. Use Present Instruments Earlier than Writing Customized eBPF Packages
Instruments like bcc (BPF Compiler Assortment) or bcc-tools, bpftrace, and libbpf supply pre-built options for observability and cut back the chance of writing unsafe or inefficient eBPF packages. Examples:
execsnoopfor tracing course of executionopensnoopfor tracing file open occasionstcptracerfor observing TCP connections
3. Decrease Overhead by Choosing Environment friendly Probes
Keep away from attaching eBPF packages to high-frequency occasions (like scheduler-related occasions or community packet processing) except needed. As a substitute, deal with rare occasions resembling particular syscalls or features. Use kprobes and tracepoints selectively to keep away from overhead. Favor tracepoints when obtainable, as they’re designed for observability and impose much less overhead.
4. Leverage BPF Maps Successfully
eBPF packages use BPF maps to retailer and share information between the kernel and person house. Select acceptable map sorts (e.g., hash maps, arrays) and guarantee they’re correctly sized to keep away from reminiscence overhead. Implement methods to batch information assortment and cut back the frequency of user-space reads.
5. Charge-Limiting and Filtering
Implement rate-limiting in eBPF packages to stop extreme information assortment throughout high-frequency occasions.Use filtering to focus on solely particular occasions or processes, thus lowering the quantity of knowledge being collected and processed.
6. Decrease Probe Execution Time
eBPF packages ought to be designed to run in a brief and bounded time to keep away from affecting system efficiency. Kernel enforces closing dates on eBPF packages, however even approaching these limits can degrade efficiency. Keep away from advanced logic and loops in your eBPF code to make sure that it runs shortly.
7. Monitor Overhead Fastidiously
All the time monitor the overhead launched by eBPF packages. The Linux kernel gives instruments like bpftool to examine and measure the efficiency influence of eBPF packages. Measure the next:
- Latency of the noticed software
- CPU utilization improve resulting from eBPF packages
- Reminiscence utilization of BPF maps
8. Use BPF Sort Format (BTF) for Compatibility
Make the most of BTF (BPF Sort Format) to make sure that your eBPF packages are moveable and work throughout completely different kernel variations. BTF permits eBPF packages to entry kernel internals with out requiring version-specific modifications.
9. Guarantee Security With Verifier Compliance
The kernel’s eBPF verifier ensures the security of eBPF packages by analyzing them earlier than they’re loaded. Hold packages easy and keep away from unsafe operations, resembling accessing uninitialized information or performing out-of-bounds reminiscence accesses, which may trigger verifier failures.
10. Keep Up to date With Kernel Variations
The eBPF ecosystem evolves shortly, and newer kernel variations usually convey optimizations and new options that enhance the efficiency and security of eBPF packages. Contemplate working a more moderen kernel (e.g., 5.x or later) to learn from these enhancements.
11. Use Off-Crucial-Path Information Assortment
The place potential, transfer information assortment and heavy processing off the essential path. For instance, acquire minimal information within the eBPF probe itself and offload extra detailed processing to user-space purposes.
12. Safety Issues
Be sure eBPF packages are utilized in a safe method. Since eBPF operates on the kernel degree, improperly written or malicious packages can expose the system to vulnerabilities. Leverage cgroup BPF or LSM BPF to manage and prohibit eBPF packages.
By adhering to those greatest practices, you may successfully leverage eBPF for observability with out introducing important overhead or danger to the system. All the time deal with simplicity, effectivity, and security when designing and deploying eBPF packages.

