In Kubernetes, a Secret is an object that shops delicate info like a password, token, key, and so forth. One of many a number of good practices for Kubernetes secret administration is making use of a third-party secrets and techniques retailer supplier resolution to handle secrets and techniques exterior of the clusters and configuring pods to entry these secrets and techniques. There are many such third-party options out there out there, akin to:
- HashiCorp Vault
- Google Cloud Secret Supervisor
- AWS Secrets and techniques Supervisor
- Azure Key Vault
These third-party options, a.okay.a Exterior Secrets and techniques Managers (ESM), implement safe storage, secret versioning, fine-grain entry management, audit and logging.
The Exterior Secrets and techniques Operator (ESO) is an open-source resolution used for safe retrieval and synchronization of secrets and techniques from the ESM. The secrets and techniques retrieved from the ESM are injected into the Kubernetes setting as native secret objects. Thus, ESO allows utility builders to make use of Kubernetes Secret Object with Enterprise grade Exterior Secret Managers.
ESO implementation in a Kubernetes cluster primarily requires two assets:
ClusterSecretStorethat specifies easy methods to entry the Exterior Secrets and techniques SupervisorExternalSecretthat specifies what knowledge is to be fetched and saved as a Kubernetes secret object
Secret retrieval is a one-time exercise, however synchronization of secrets and techniques generates site visitors at common intervals. So it is necessary to comply with greatest practices (listed under) that may optimize ESO site visitors to the exterior secrets and techniques administration methods.
Defining Refresh Interval for the ExternalSecret Object
Lengthy-lived static secrets and techniques pose a safety threat that may be addressed by adopting a secret rotation coverage. Every time a secret will get rotated within the ESM, it needs to be mirrored within the corresponding Kubernetes Secret object. ESO helps computerized secret synchronization for such conditions. Secrets and techniques get synchronized after a specified timeframe, referred to as “refresh interval,” which is part of the ExternalSecret useful resource definition.
It’s advisable to go for an optimum refresh interval worth; e.g., a secret that is not prone to get modified typically can have a refresh interval of at some point as a substitute of 1 hour or a couple of minutes. Bear in mind, the extra aggressive the refresh interval, the extra site visitors it’ll generate.
Defining Refresh Interval for the ClusterSecretStore Object
The refresh interval outlined within the ClusterSecretStore (CSS) is the frequency with which the CSS validates itself with the ESM. If the refresh interval is just not specified whereas defining a CSS object, the default refresh interval (which is restricted to the ESM API implementation) is taken into account. The default CSS refresh interval has been discovered to be a really aggressive worth; i.e., the interplay with the ESM occurs very ceaselessly on this case.
For instance, the image under is an excerpt of the outline of a pattern CSS (HashiCorp Vault is the ESM on this case) that has no refresh interval worth in its definition. The refresh interval seen within the CSS description under is 5 minutes, implying the useful resource is approaching the ESM each 5 minutes, producing avoidable site visitors.
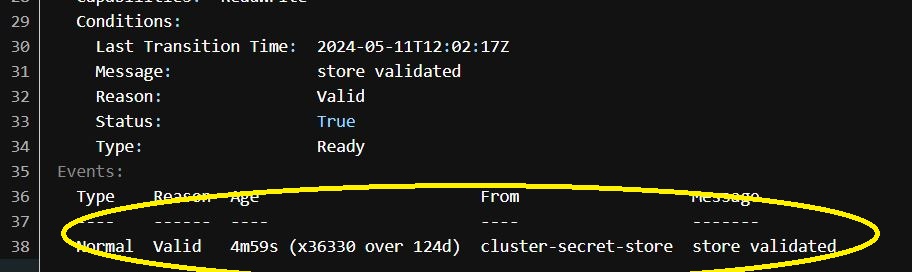
The refresh interval attribute will get missed in most CSS definitions as a result of:
- There’s a discrepancy between the default worth of the refresh interval for an
ExternalSecretobject and that for aClusterSecretStoreobject. This could inadvertently result in an un-optimized implementation forClusterSecretStore.- The default worth of the refresh interval for the
ExternalSecretobject isZERO. It signifies that refresh is disabled; i.e., the key by no means will get synchronized mechanically. - The default worth of the refresh interval for the
ClusterSecretStoreobject is ESM-specific; e.g., it’s 5 minutes within the HashiCorp Vault state of affairs cited above.
- The default worth of the refresh interval for the
- The refresh interval attribute is just not current within the distinguished samples/examples on the web (e.g., test ClusterSecretStore documentation). One can acquire perception into this attribute by way of the command
kubectl clarify clustersecretstore.spec.
The importance of defining a refresh interval for CSS may be realized by monitoring the site visitors generated by way of a CSS object with no refresh interval in a take a look at cluster that doesn’t have any ESO object.
Utilizing Cluster-Scoped Exterior Secrets and techniques Over Namespace-Scoped Exterior Secrets and techniques
The primary ESO launch was accomplished in Might 2021. Again then, the one possibility was to make use of the namespace-scoped ExternalSecret useful resource. So, even when the key saved was international, an ExternalSecret object needed to be outlined for every namespace. ExternalSecret objects throughout all namespaces would get synchronized on the outlined refresh interval, thereby producing site visitors. The bigger the variety of namespaces, the extra site visitors they’d generate.
There was a dire want for a world ExternalSecret object accessible throughout completely different namespaces. To fill this hole, the cluster-level exterior secret useful resource, ClusterExternalSecret (CES) was launched in April 2022 (v0.5.0). Choosing ClusterExternalSecret over ExternalSecret (the place relevant) can keep away from redundant site visitors technology.
A pattern YAML particular to HashiCorp Vault and Kubernetes picture pull secret may be referred to under:
apiVersion: external-secrets.io/v1beta1
type: ClusterExternalSecret
metadata:
identify: "sre-cluster-ext-secret"
spec:
# The identify for use on the ExternalSecrets
externalSecretName: sre-cluster-es
# This can be a primary label selector to pick the namespaces to deploy ExternalSecrets to.
# you may learn extra about them right here https://kubernetes.io/docs/ideas/overview/working-with-objects/labels/#resources-that-support-set-based-requirements
namespaceSelector: #necessary -- not including it will expose the exterior secret
matchLabels:
label: try_ces
# How typically the ClusterExternalSecret ought to reconcile itself
# It will resolve how typically to test and guarantee that the ExternalSecrets exist within the matching namespaces
refreshTime: "10h"
# That is the spec of the ExternalSecrets to be created
externalSecretSpec:
secretStoreRef:
identify: vault-backend
type: ClusterSecretStore
goal:
identify: sre-k8secret-cluster-es
template:
kind: kubernetes.io/dockerconfigjson
knowledge:
.dockerconfigjson: "{ toString}"
refreshInterval: "24h"
knowledge:
- secretKey: dockersecret
remoteRef:
key: imagesecret
property: dockersecretConclusion
By following the very best practices listed above, the Exterior Secrets and techniques Operator site visitors to the Exterior Secrets and techniques Supervisor may be diminished considerably.

