In an period the place digital transformation is quickly advancing, the significance of cybersecurity can’t be overstated. One of many important points of sustaining strong safety is penetration testing, generally referred to as pentesting. This information goals to supply novices with a complete understanding of penetration testing, providing a step-by-step strategy to getting began on this vital discipline.
Introduction to Penetration Testing
Penetration testing is a simulated cyber assault towards a pc system, community, or internet utility to determine safety vulnerabilities that an attacker may exploit. The first objective is to seek out and repair these vulnerabilities earlier than they are often leveraged by malicious actors. Penetration testing might be guide or automated and usually includes numerous strategies and instruments to guage the safety of a corporation’s IT infrastructure.
Why Penetration Testing Is Necessary
Penetration testing helps organizations:
- Establish safety vulnerabilities earlier than attackers do.
- Adjust to trade laws and requirements.
- Shield delicate information and keep buyer belief.
- Enhance general safety posture and incident response methods.
Getting Began With Penetration Testing
Step 1: Understanding the Fundamentals
Earlier than diving into penetration testing, it is essential to know some foundational ideas in cybersecurity:
- Threats and vulnerabilities: Perceive the distinction between threats (potential assaults) and vulnerabilities (weaknesses that may be exploited).
- Assault vectors: Familiarize your self with widespread assault vectors, corresponding to phishing, malware, and SQL injection.
- Safety testing sorts: Find out about several types of safety testing, together with vulnerability evaluation, safety auditing, and penetration testing.
Step 2: Establishing Your Setting
To start out penetration testing, you want a secure and managed surroundings. This typically includes organising a lab that mimics real-world circumstances however doesn’t have an effect on dwell techniques.
- Digital Machines (VMs): Use VMs to create remoted environments for testing. Instruments like VMware or VirtualBox can assist you arrange a number of VMs on a single machine.
- Kali Linux: Kali Linux is a Debian-based distribution particularly designed for penetration testing. It comes pre-installed with quite a few instruments used for safety testing.
- Community simulation instruments: Instruments like GNS3 or Cisco Packet Tracer can assist you simulate complicated community environments.
Step 3: Studying the Instruments
Penetration testers depend on numerous instruments to conduct checks. Among the hottest instruments embody:
- Nmap: A community scanning software used to find hosts and companies on a pc community.
- Metasploit: A framework for creating and executing exploit code towards a distant goal machine.
- Burp Suite: A complete set of instruments for internet utility safety testing.
- Wireshark: A community protocol analyzer used to seize and interactively browse the visitors operating on a pc community.
- John the Ripper: A password-cracking software used to check the energy of passwords.
Step 4: Understanding Authorized and Moral Issues
Penetration testing includes actions that, if achieved with out permission, might be unlawful and unethical. At all times guarantee you may have specific permission to check the goal techniques. Familiarize your self with related legal guidelines and laws, such because the Laptop Fraud and Abuse Act (CFAA) in america.
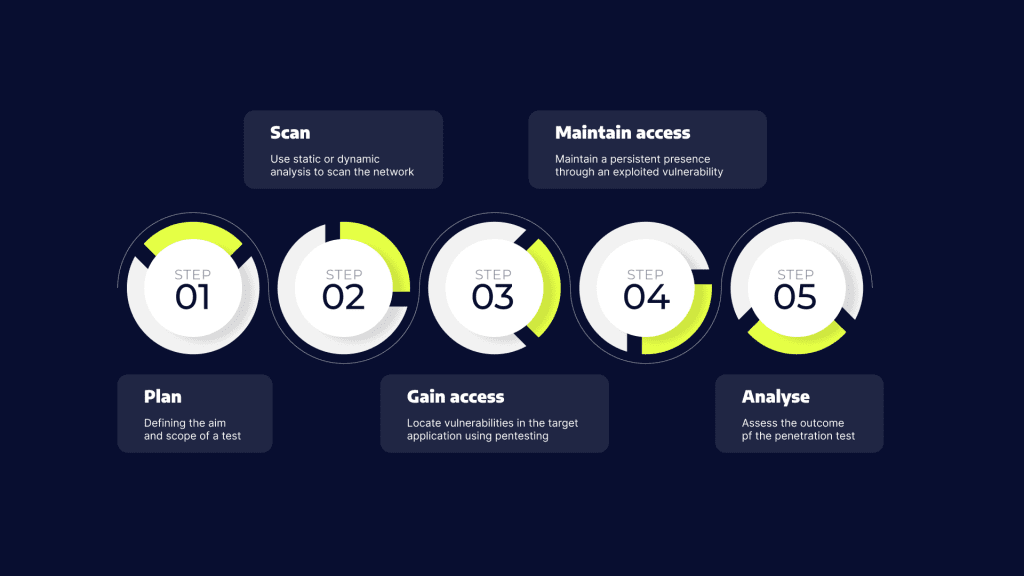
Step 5: Conducting a Penetration Check
A penetration check usually follows these phases:
1. Planning and Reconnaissance
- Outline scope and targets: Clearly define what can be examined and what the aims are. This consists of figuring out goal techniques, testing strategies, and success standards.
- Collect info: Use passive and energetic reconnaissance methods to gather as a lot info as potential in regards to the goal. Instruments like WHOIS lookup, Google hacking, and social engineering might be helpful.
2. Scanning
- Community scanning: Use instruments like Nmap to determine open ports, companies, and potential vulnerabilities on the goal techniques.
- Vulnerability scanning: Use automated instruments like Nessus or OpenVAS to determine recognized vulnerabilities.
3. Gaining Entry
- Exploitation: Use the data gathered to use vulnerabilities and achieve entry to the goal system. Metasploit is a robust software for this part.
- Privilege escalation: As soon as preliminary entry is obtained, try to escalate privileges to realize full management of the system.
4. Sustaining Entry
- Persistence: Implement backdoors or different strategies to keep up entry to the goal system over an extended interval.
- Overlaying tracks: Erase proof of your presence to keep away from detection and make sure the goal system’s regular operations should not disrupted.
5. Evaluation and Reporting
- Knowledge evaluation: Analyze the outcomes of the penetration check, together with the vulnerabilities exploited, information accessed, and the general impression.
- Report writing: Create an in depth report that features findings, proof, and suggestions for remediation. An excellent report ought to be clear and concise, making it straightforward for the group to know the dangers and take motion.
Step 6: Submit-Testing Actions
After finishing a penetration check, it’s vital to make sure that the group addresses the recognized vulnerabilities. This includes:
- Remediation: Work with the group’s IT and safety groups to repair the recognized vulnerabilities.
- Re-testing: Conduct follow-up checks to make sure that the vulnerabilities have been correctly addressed.
- Steady enchancment: Penetration testing ought to be a part of an ongoing safety technique. Frequently replace your abilities, instruments, and methods to remain forward of evolving threats.
Important Expertise for Penetration Testers
To achieve success in penetration testing, you want a mixture of technical and non-technical abilities:
Technical Expertise
- Networking: Perceive community protocols, architectures, and units.
- Working techniques: Proficiency in Home windows, Linux, and different working techniques.
- Programming: Information of scripting languages like Python, Bash, or PowerShell.
- Net applied sciences: Understanding of internet utility frameworks, databases, and APIs.
Non-Technical Expertise
- Analytical pondering: Capacity to assume like an attacker and determine potential weaknesses.
- Drawback-solving: Expertise to beat obstacles and discover artistic options.
- Communication: Capacity to jot down clear stories and clarify technical ideas to non-technical stakeholders.
- Moral mindset: Dedication to moral hacking practices and adherence to authorized requirements.
We are able to considerably improve the effectiveness of penetration testing by offering automated cloud safety options tailor-made to trendy environments. This is how we will complement and bolster the steps and processes outlined within the weblog:
Integrating With Penetration Testing
1. Planning and Reconnaissance
Cloud Stock and Discovery
We are able to mechanically uncover and stock all cloud property throughout a number of cloud platforms (AWS, Azure, GCP). This supplies penetration testers with a complete checklist of property to focus on, making certain no useful resource is neglected.
Automated Reconnaissance
We are able to collect detailed details about your cloud infrastructure, corresponding to safety teams, VPCs, and IAM roles, streamlining the reconnaissance part and offering invaluable insights into potential assault vectors.
2. Scanning
Vulnerability Evaluation
We conduct steady vulnerability assessments of cloud sources, figuring out misconfigurations, outdated software program, and different safety gaps. This enhances conventional community scanning instruments like Nmap, offering a extra detailed view of cloud-specific vulnerabilities.
Compliance Checks
The platform consists of built-in compliance checks for requirements corresponding to CIS, NIST, and GDPR. This helps determine non-compliant sources, which are sometimes high-priority targets for penetration testing.
3. Gaining Entry
Figuring out Exploitable Weaknesses
By leveraging our automated scanning outcomes, penetration testers can rapidly pinpoint and prioritize vulnerabilities which can be more than likely to be exploited. This enhances the effectivity of the exploitation part, permitting testers to give attention to high-impact points.
Position-Primarily based Entry Insights
We offer an in depth evaluation of IAM roles and permissions, serving to testers perceive the potential for privilege escalation and lateral motion throughout the cloud surroundings.
4. Sustaining Entry
Safety Monitoring
We provide steady monitoring of cloud environments, detecting and alerting on uncommon exercise. This can be utilized to guage the effectiveness of persistence methods and to make sure that entry might be maintained with out detection.
Automated Remediation
The platform can mechanically remediate sure points, corresponding to reverting malicious modifications to configurations. This helps in understanding the resilience of the surroundings towards persistent threats.
5. Evaluation and Reporting
Complete Reporting
We generate detailed stories of all findings, together with vulnerabilities, misconfigurations, and compliance violations. These stories might be built-in into the ultimate penetration testing report, offering a radical overview of cloud-specific points.
Actionable Insights
The platform not solely identifies points but in addition supplies actionable suggestions for remediation. This helps organizations rapidly handle vulnerabilities recognized throughout penetration testing.
Enhancing Penetration Tester Expertise and Effectivity
Studying Assets
We provide documentation and help that may assist penetration testers perceive cloud-specific safety challenges and options. This enhances conventional studying sources and certifications talked about within the weblog.
Palms-On Follow
Through the use of our service in a managed lab surroundings, testers can achieve hands-on expertise with real-world cloud configurations and safety points, enhancing their sensible abilities.
Neighborhood Engagement
Taking part in boards and discussions associated to us, we will present penetration testers with insights and greatest practices shared by different safety professionals.
Conclusion
We are able to enormously improve the penetration testing course of by automating the invention, evaluation, and remediation of cloud-specific safety points. By integrating our companies into your penetration testing workflow, you may guarantee a extra thorough and environment friendly analysis of your cloud surroundings’s safety posture. This not solely helps in figuring out and fixing vulnerabilities but in addition in sustaining steady compliance and safety in dynamic cloud infrastructures.
Incorporating our companies into the steps outlined within the weblog can present a extra strong and complete strategy to penetration testing, significantly for organizations closely reliant on cloud companies.

