With Spring Boot 3.2 and Spring Framework 6.1, we get assist for Coordinated Restore at Checkpoint (CRaC), a mechanism that allows Java functions to start out up sooner. With Spring Boot, we will use CRaC in a simplified manner, often known as Automated Checkpoint/Restore at startup. Although not as highly effective as the usual manner of utilizing CRaC, this weblog submit will present an instance the place the Spring Boot functions startup time is decreased by 90%. The pattern functions are from chapter 6 in my e-book on constructing microservices with Spring Boot.
Overview
The weblog submit is split into the next sections:
- Introducing CRaC, advantages, and challenges
- Creating CRaC-based Docker pictures with a Dockerfile
- Attempting out CRaC with computerized checkpoint/restore
- Abstract
- Subsequent weblog submit
Let’s begin studying about CRaC and its advantages and challenges.
1. Introducing CRaC, Advantages, and Challenges
Coordinated Restore at Checkpoint (CRaC) is a function in OpenJDK, initially developed by Azul, to reinforce the startup efficiency of Java functions by permitting them to revive to a beforehand saved state rapidly. CRaC permits Java functions to avoid wasting their state at a selected time limit (checkpoint) after which restore from that state at a later time. That is significantly helpful for situations the place quick startup occasions are essential, resembling serverless environments, microservices, and, typically, functions that should be capable to scale up their cases rapidly and in addition assist scale-to-zero when not getting used.
This introduction will first clarify a bit about how CRaC works, then focus on a number of the challenges and issues related to it, and eventually, describe how Spring Boot 3.2 integrates with it. The introduction is split into the next subsections:
- 1.1. How CRaC Works
- 1.2. Challenges and Issues
- 1.3. Spring Boot 3.2 integration with CRaC
1.1. How CRaC Works
Checkpoint Creation
At a selected level throughout the utility’s execution, a checkpoint is created. This entails capturing all the state of the Java utility, together with the heap, stack, and all energetic threads. The state is then serialized and saved to the file system. Throughout the checkpoint course of, the appliance is often paused to make sure a constant state is captured. This pause is coordinated to attenuate disruption and make sure the utility can resume accurately.
Earlier than taking the checkpoint, some requests are normally despatched to the appliance to make sure that it’s warmed up, i.e., all related lessons are loaded, and the JVM HotSpot engine has had an opportunity to optimize the bytecode in line with how it’s being utilized in runtime.
Instructions to carry out a checkpoint:
java -XX:CRaCCheckpointTo= -jar my_app.jar
# Make calls to the app to heat up the JVM...
jcmd my_app.jar JDK.checkpoint
State Restoration
When the appliance is began from the checkpoint, the beforehand saved state is deserialized from the file system and loaded again into reminiscence. The applying then continues execution from the precise level the place the checkpoint was taken, bypassing the standard startup sequence.
Command to revive from a checkpoint:
java -XX:CRaCRestoreFrom=
Restoring from a checkpoint permits functions to skip the preliminary startup course of, together with class loading, warmup initialization, and different startup routines, considerably lowering startup occasions.
For extra data, see Azul’s documentation: What’s CRaC?
1.2. Challenges and Issues
As with all new expertise, CRaC comes with a brand new set of challenges and issues:
State Administration
Open recordsdata and connections to exterior assets, resembling databases, should be closed earlier than the checkpoint is taken. After the restore, they should be reopened.
CRaC exposes a Java lifecycle interface that functions can use to deal with this, org.crac.Useful resource, with the callback strategies beforeCheckpoint and afterRestore.
Delicate Data
Credentials and secrets and techniques saved within the JVM’s reminiscence can be serialized into the recordsdata created by the checkpoint. Due to this fact, these recordsdata have to be protected. An alternate is to run the checkpoint command in opposition to a brief surroundings that makes use of different credentials and exchange the credentials on restore.
Linux Dependency
The checkpoint method is predicated on a Linux function known as CRIU, “Checkpoint/Restore In Userspace”. This function solely works on Linux, so the simplest solution to check CRaC on a Mac or a Home windows PC is to bundle the appliance right into a Linux Docker picture.
Linux Privileges Required
CRIU requires particular Linux privileges, leading to Docker instructions to construct Docker pictures and creating Docker containers additionally requiring Linux privileges to have the ability to run.
Storage Overhead
Storing and managing checkpoint knowledge requires extra storage assets, and the checkpoint dimension can affect the restoration time. The unique jar file can be required to have the ability to restart a Java utility from a checkpoint.
I’ll describe deal with these challenges within the part on creating Docker pictures.
1.3. Spring Boot 3.2 Integration With CRaC
Spring Boot 3.2 (and the underlying Spring Framework) helps with the processing of closing and reopening connections to exterior assets. Earlier than the creation of the checkpoint, Spring stops all working beans, giving them an opportunity to shut assets if wanted. After a restore, the identical beans are restarted, permitting beans to reopen connections to the assets.
The one factor that must be added to a Spring Boot 3.2-based utility is a dependency to the crac-library. Utilizing Gradle, it appears like the next within the gradle.construct file:
dependencies {
implementation 'org.crac:crac'
Observe: The conventional Spring Boot BOM mechanism takes care of versioning the
cracdependency.
The automated closing and reopening of connections dealt with by Spring Boot normally works. Sadly, when this weblog submit was written, some Spring modules lacked this assist. To trace the state of CRaC assist within the Spring ecosystem, a devoted check challenge, Spring Lifecycle Smoke Assessments, has been created. The present state could be discovered on the challenge’s standing web page.
If required, an utility can register callback strategies to be known as earlier than a checkpoint and after a restore by implementing the above-mentioned Useful resource interface. The microservices used on this weblog submit have been prolonged to register callback strategies to display how they can be utilized. The code appears like this:
import org.crac.*;
public class MyApplication implements Useful resource {
public MyApplication() {
Core.getGlobalContext().register(this);
}
@Override
public void beforeCheckpoint(Context extends Useful resource> context) {
LOG.data("CRaC's beforeCheckpoint callback method called...");
}
@Override
public void afterRestore(Context extends Useful resource> context) {
LOG.data("CRaC's afterRestore callback method called...");
}
}
Spring Boot 3.2 offers a simplified different to take a checkpoint in comparison with the default on-demand different described above. It’s known as computerized checkpoint/restore at startup. It’s triggered by including the JVM system property -Dspring.context.checkpoint=onRefresh to the java -jar command. When set, a checkpoint is created mechanically when the appliance is began. The checkpoint is created after Spring beans have been created however not began, i.e., after many of the initialization work however earlier than that utility begins. For particulars, see Spring Boot docs and Spring Framework docs.
With an computerized checkpoint, we don’t get a completely warmed-up utility, and the runtime configuration should be specified at construct time. Because of this the ensuing Docker pictures can be runtime-specific and comprise delicate data from the configuration, like credentials and secrets and techniques. Due to this fact, the Docker pictures should be saved in a personal and guarded container registry.
Observe: If this doesn’t meet your necessities, you possibly can go for the on-demand checkpoint, which I’ll describe within the subsequent weblog submit.
With CRaC and Spring Boot 3.2’s assist for CRaC coated, let’s see how we will create Docker pictures for Spring Boot functions that use CRaC.
2. Creating CRaC-Based mostly Docker Photos With a Dockerfile
Whereas studying use CRaC, I studied a number of weblog posts on utilizing CRaC with Spring Boot 3.2 functions. All of them use fairly advanced bash scripts (relying in your bash expertise) utilizing Docker instructions like docker run, docker exec, and docker commit. Although they work, it looks like an unnecessarily advanced resolution in comparison with producing a Docker picture utilizing a Dockerfile.
So, I made a decision to develop a Dockerfile that runs the checkpoint command as a RUN command within the Dockerfile. It turned out to have its personal challenges, as described beneath. I’ll start by describing my preliminary try after which clarify the issues I stumbled into and the way I solved them, one after the other till I attain a completely working resolution. The walkthrough is split into the next subsections:
- 2.1. First try
- 2.2. Drawback #1, privileged builds with
docker construct - 2.3. Drawback #2, CRaC returns exit standing 137, as a substitute of 0
- 2.4. Drawback #3, Runtime configuration
- 2.5. Drawback #4, Spring Knowledge JPA
- 2.6. The ensuing
Dockerfile
Let’s begin with a primary try and see the place it leads us.
2.1. First Try
My preliminary assumption was to create a Dockerfile primarily based on a multi-stage construct, the place the primary stage creates the checkpoint utilizing a JDK-based base picture, and the second step makes use of a JRE-based base picture for runtime. Nonetheless, whereas penning this weblog submit, I did not discover a base picture for a Java 21 JRE supporting CRaC. So I modified my thoughts to make use of an everyday Dockerfile as a substitute, utilizing a base picture from Azul: azul/zulu-openjdk:21-jdk-crac
Observe: BellSoft additionally offers base pictures for CraC; see Liberica JDK with CRaC Help as an alternative choice to Azul.
The primary model of the Dockerfile appears like this:
FROM azul/zulu-openjdk:21-jdk-crac
ADD construct/libs/*.jar app.jar
RUN java -Dspring.context.checkpoint=onRefresh -XX:CRaCCheckpointTo=checkpoint -jar app.jar
EXPOSE 8080
ENTRYPOINT ["java", "-XX:CRaCRestoreFrom=checkpoint"]
This Dockerfile is sadly not attainable to make use of since CRaC requires a construct to run privileged instructions.
2.2. Drawback #1, Privileged Builds With Docker Construct
As talked about in part 1.2. Challenges and Issues, CRIU, which CRaC is predicated on, requires particular Linux privileges to carry out a checkpoint. The usual docker construct command doesn’t enable privileged builds, so it might’t be used to construct Docker pictures utilizing the above Dockerfile.
Observe: The
--privileged– flag that can be utilized indocker runinstructions shouldn’t be supported bydocker construct.
Happily, Docker offers an improved builder backend known as BuildKit. Utilizing BuildKit, we will create a customized builder that’s insecure, that means it permits a Dockerfile to run privileged instructions. To speak with BuildKit, we will use Docker’s CLI device buildx.
The next command can be utilized to create an insecure builder named insecure-builder:
docker buildx create --name insecure-builder --buildkitd-flags '--allow-insecure-entitlement safety.insecure'
Observe: The builder runs in isolation inside a Docker container created by the
docker buildx createcommand. You’ll be able to run adocker pscommand to disclose the container. When the builder is now not required, it may be eliminated with the command:docker buildx rm insecure-builder.
The insecure builder can be utilized to construct a Docker picture with a command like:
docker buildx --builder insecure-builder construct --allow safety.insecure --load .
Observe: The
--loadflag hundreds the constructed picture into the common native Docker picture cache. Because the builder runs in an remoted container, its end result won’t find yourself within the common native Docker picture cache by default.
RUN instructions in a Dockerfile that requires privileges should be suffixed with --security=insecure. The --security-flag is barely in preview and should subsequently be enabled within the Dockerfile by including the next line as the primary line within the Dockerfile:
# syntax=docker/dockerfile:1.3-labs
For extra particulars on BuildKit and docker buildx, see Docker Construct structure.
We are able to now carry out the construct; nonetheless, the best way the CRaC is applied stops the construct, as we are going to study within the subsequent part.
2.3. Drawback #2, CRaC Returns Exit Standing 137 As a substitute of 0
On a profitable checkpoint, the java -Dspring.context.checkpoint=onRefresh -XX:CRaCCheckpointTo... command is terminated forcefully (like utilizing kill -9) and returns the exit standing 137 as a substitute of 0, inflicting the Docker construct command to fail.
To stop the construct from stopping, the java command is prolonged with a check that verifies that 137 is returned and, if that’s the case, returns 0 as a substitute. The next is added to the java command: || if [ $? -eq 137 ]; then return 0; else return 1; fi.
Observe:
||signifies that the command following can be executed if the primary command fails.
With CRaC working in a Dockerfile, let’s transfer on and study concerning the challenges with runtime configuration and deal with them.
2.4. Drawback #3, Runtime Configuration
Utilizing Spring Boot’s computerized checkpoint/restore at startup, there isn’t any solution to specify runtime configuration on restore; at the least, I haven’t discovered a solution to do it. Because of this the runtime configuration needs to be specified at construct time. Delicate data from the runtime configuration, resembling credentials used for connecting to a database, will written to the checkpoint recordsdata. Because the Docker pictures will comprise these checkpoint recordsdata additionally they have to be dealt with in a safe manner.
The Spring Framework documentation incorporates a warning about this, copied from the part Automated checkpoint/restore at startup:
As talked about above, and particularly in use instances the place the CRaC recordsdata are shipped as a part of a deployable artifact (a container picture, for instance), function with the idea that any delicate knowledge “seen” by the JVM results in the CRaC recordsdata, and assess fastidiously the associated safety implications.
So, let’s assume that we will defend the Docker pictures, for instance, in a personal registry with correct authorization in place and that we will specify the runtime configuration at construct time.
In Chapter 6 of the e-book, the supply code specifies the runtime configuration within the configuration recordsdata, utility.yml, in a Spring profile named docker.
The RUN command, which performs the checkpoint, has been prolonged to incorporate an surroundings variable that declares what Spring profile to make use of: SPRING_PROFILES_ACTIVE=docker.
Observe: When you’ve got the runtime configuration in a separate file, you possibly can add the file to the Docker picture and level it out utilizing an surroundings variable like
SPRING_CONFIG_LOCATION=file:runtime-configuration.yml.
With the challenges of correct runtime configuration coated, now we have just one downside left to deal with: Spring Knowledge JPA’s lack of assist for CRaC with out some additional work.
2.5. Drawback #4, Spring Knowledge JPA
Spring Knowledge JPA doesn’t work out-of-the-box with CRaC, as documented within the Smoke Assessments challenge; see the part about Forestall early database interplay. Because of this auto-creation of database tables when beginning up the appliance, shouldn’t be attainable when utilizing CRaC. As a substitute, the creation needs to be carried out outdoors of the appliance startup course of.
Observe: This restriction doesn’t apply to embedded SQL databases. For instance, the Spring PetClinic utility works with CRaC with none modifications because it makes use of an embedded SQL database by default.
To handle these deficiencies, the next modifications have been made within the supply code of Chapter 6:
-
Handbook creation of a SQL DDL script,
create-tables.sqlSince we will now not depend on the appliance to create the required database tables, a SQL DDL script has been created. To allow the appliance to create the script file, a Spring profile
create-ddl-scripthas been added within the assessment microservice’s configuration file,microservices/review-service/src/predominant/assets/utility.yml. It appears like:spring.config.activate.on-profile: create-ddl-script spring.jpa.properties.jakarta.persistence.schema-generation: create-source: metadata scripts: motion: create create-target: crac/sql-scripts/create-tables.sqlThe SQL DDL file has been created by beginning the MySQL database and, subsequent, the appliance with the brand new Spring profile. As soon as linked to the database, the appliance and database are shut down. Pattern instructions:
docker compose up -d mysql SPRING_PROFILES_ACTIVE=create-ddl-script java -jar microservices/review-service/construct/libs/review-service-1.0.0-SNAPSHOT.jar # CTRL/C as soon as "Connected to MySQL: jdbc:mysql://localhost/review-db" is written to the log output docker compose downThe ensuing SQL DDL script,
crac/sql-scripts/create-tables.sql, has been added to Chapter 6’s supply code. -
The Docker Compose file configures MySQL to execute the SQL DDL script at startup.
A CraC-specific model of the Docker Compose file has been created,
crac/docker-compose-crac.yml. To create the tables when the database is beginning up, the SQL DDL script is used as an init script. The SQL DDL script is mapped into the init-folder/docker-entrypoint-initdb.dwith the next volume-mapping within the Docker Compose file:volumes: - "./sql-scripts/create-tables.sql:/docker-entrypoint-initdb.d/create-tables.sql" -
Added a runtime-specific Spring profile within the assessment microservice’s configuration file.
The rules within the Smoke Assessments challenge’s JPA part have been adopted by including an additional Spring profile named
crac. It appears like the next within the assessment microservice’s configuration file:spring.config.activate.on-profile: crac spring.jpa.database-platform: org.hibernate.dialect.MySQLDialect spring.jpa.properties.hibernate.temp.use_jdbc_metadata_defaults: false spring.jpa.hibernate.ddl-auto: none spring.sql.init.mode: by no means spring.datasource.hikari.allow-pool-suspension: true -
Lastly, the Spring profile
cracis added to theRUNcommand within the Dockerfile to activate the configuration when the checkpoint is carried out.
2.6. The Ensuing Dockerfile
Lastly, we’re achieved with dealing with the issues ensuing from utilizing a Dockerfile to construct a Spring Boot utility that may restore rapidly utilizing CRaC in a Docker picture.
The ensuing Dockerfile, crac/Dockerfile-crac-automatic, appears like:
# syntax=docker/dockerfile:1.3-labs
FROM azul/zulu-openjdk:21-jdk-crac
ADD construct/libs/*.jar app.jar
RUN --security=insecure
SPRING_PROFILES_ACTIVE=docker,crac
java -Dspring.context.checkpoint=onRefresh
-XX:CRaCCheckpointTo=checkpoint -jar app.jar
|| if [ $? -eq 137 ]; then return 0; else return 1; fi
EXPOSE 8080
ENTRYPOINT ["java", "-XX:CRaCRestoreFrom=checkpoint"]
Observe: One and the identical Dockerfile is utilized by all microservices to create CRaC variations of their Docker pictures.
We at the moment are able to attempt it out!
3. Attempting Out CRaC With Automated Checkpoint/Restore
To check out CRaC, we are going to use the microservice system panorama utilized in Chapter 6 of my e-book. In case you are not acquainted with the system panorama, it appears like the next:
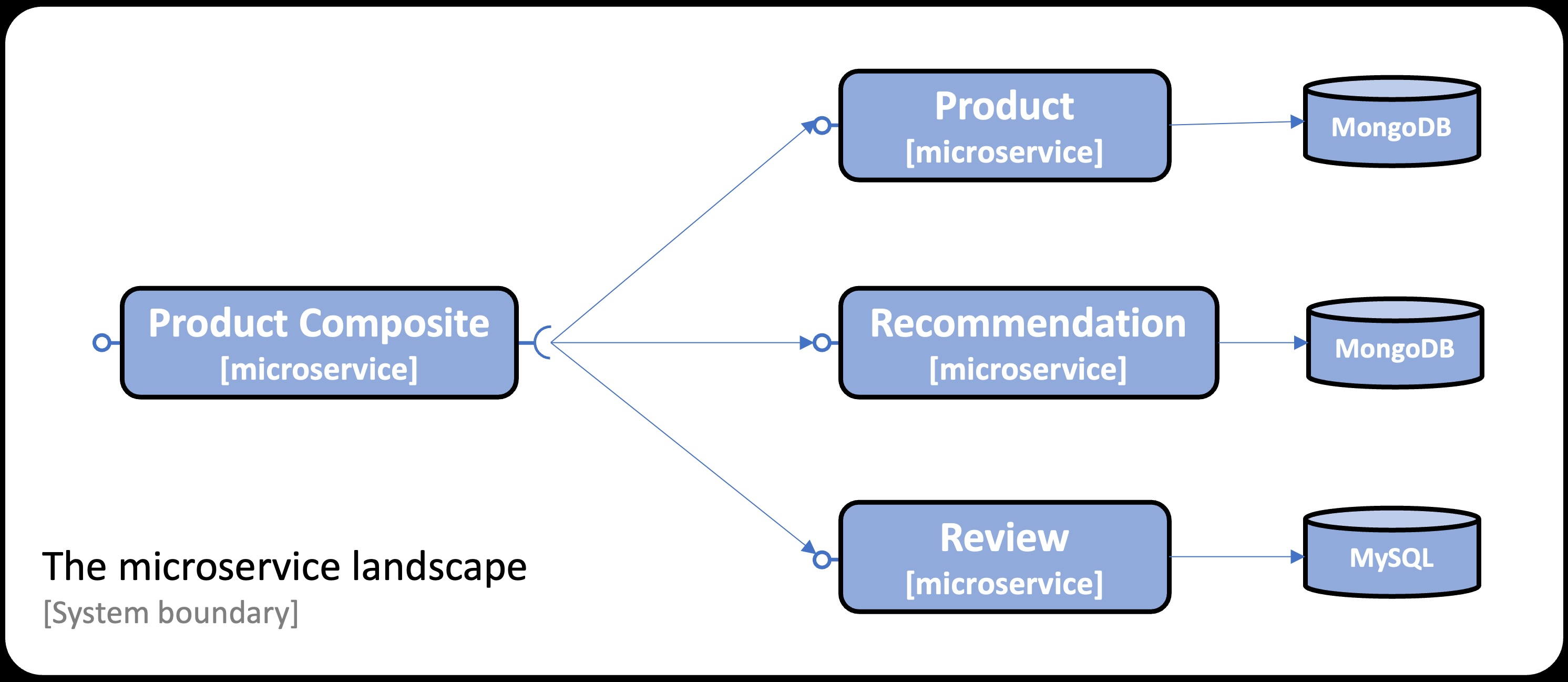
Chapter 6 makes use of Docker Compose to handle (construct, begin, and cease) the system panorama.
Observe: For those who don’t have all of the instruments used on this weblog submit put in in your surroundings, you possibly can look into Chapters 21 and 22 for set up directions.
To check out CRaC, we have to get the supply code from GitHub, compile it, and create the Docker pictures for every microservice utilizing a customized insecure Docker builder. Subsequent, we will use Docker Compose to start out up the system panorama and run the end-to-end validation script that comes with the e-book to make sure that all the pieces works as anticipated. We are going to wrap up the try-out part by evaluating the startup occasions of the microservices after they begin with and with out utilizing CRaC.
We are going to undergo every step within the following subsections:
- 3.1. Getting the supply code
- 3.2. Constructing the CRaC-based Docker pictures
- 3.3. Operating end-to-end assessments
- 3.4. Evaluating startup occasions with out CRaC
3.1. Getting the Supply Code
Run the next instructions to get the supply code from GitHub, leap into the Chapter06 folder, take a look at the department SB3.2-crac-automatic, and be sure that a Java 21 JDK is used (Eclipse Temurin is used right here):
git clone https://github.com/PacktPublishing/Microservices-with-Spring-Boot-and-Spring-Cloud-Third-Version.git
cd Microservices-with-Spring-Boot-and-Spring-Cloud-Third-Version/Chapter06
git checkout SB3.2-crac-automatic
sdk use java 21.0.3-tem
3.2. Constructing the CRaC-Based mostly Docker Photos
Begin with compiling the microservices supply code:
If not already created, create the insecure builder with the command:
docker buildx create --name insecure-builder --buildkitd-flags '--allow-insecure-entitlement safety.insecure'
Now we will construct a Docker picture, the place the construct performs a CRaC checkpoint for every of the microservices with the instructions:
docker buildx --builder insecure-builder construct --allow safety.insecure -f crac/Dockerfile-crac-automatic -t product-composite-crac --load microservices/product-composite-service
docker buildx --builder insecure-builder construct --allow safety.insecure -f crac/Dockerfile-crac-automatic -t product-crac --load microservices/product-service
docker buildx --builder insecure-builder construct --allow safety.insecure -f crac/Dockerfile-crac-automatic -t recommendation-crac --load microservices/recommendation-service
docker buildx --builder insecure-builder construct --allow safety.insecure -f crac/Dockerfile-crac-automatic -t review-crac --load microservices/review-service
3.3. Operating Finish-To-Finish Assessments
To begin up the system panorama, we are going to use Docker Compose. Since CRaC requires particular Linux privileges, a CRaC-specific docker-compose file comes with the supply code, crac/docker-compose-crac.yml. Every microservice is given the required privilege, CHECKPOINT_RESTORE, by specifying:
cap_add:
- CHECKPOINT_RESTORE
Observe: A number of weblog posts on CRaC recommend utilizing privileged containers, i.e., beginning them with
run --privlegedor includingprivileged: truewithin the Docker Compose file. This can be a actually unhealthy thought since an attacker who will get management over such a container can simply take management of the host that runs Docker. For extra data, see Docker’s documentation on Runtime privilege and Linux capabilities.
The ultimate addition to the CRaC-specific Docker Compose file is the amount mapping for MySQL so as to add the init file described above in part 2.5. Drawback #4, Spring Knowledge JPA:
volumes:
- "./sql-scripts/create-tables.sql:/docker-entrypoint-initdb.d/create-tables.sql"
Utilizing this Docker Compose file, we will begin up the system panorama and run the end-to-end verification script with the next instructions:
export COMPOSE_FILE=crac/docker-compose-crac.yml
docker compose up -d
Let’s begin with verifying that the CRaC afterRestore callback strategies had been known as:
docker compose logs | grep "CRaC's afterRestore callback method called..."
Count on one thing like:
...ReviewServiceApplication : CRaC's afterRestore callback technique known as...
...RecommendationServiceApplication : CRaC's afterRestore callback technique known as...
...ProductServiceApplication : CRaC's afterRestore callback technique known as...
...ProductCompositeServiceApplication : CRaC's afterRestore callback technique known as...
Now, run the end-to-end verification script:
If the script ends with a log output much like:
Finish, all assessments OK: Fri Jun 28 17:40:43 CEST 2024
…it means all assessments run okay, and the microservices behave as anticipated.
Convey the system panorama down with the instructions:
docker compose down
unset COMPOSE_FILE
After verifying that the microservices behave accurately when began from a CRaC checkpoint, we will evaluate their startup occasions with microservices began with out utilizing CRaC.
3.4. Evaluating Startup Instances With out CRaC
Now over to probably the most fascinating half: How a lot sooner does the microservice startup when performing a restore from a checkpoint in comparison with an everyday chilly begin?
The assessments have been run on a MacBook Professional M1 with 64 GB reminiscence.
Let’s begin with measuring startup occasions with out utilizing CRaC.
3.4.1. Startup Instances With out CRaC
To begin the microservices with out CRaC, we are going to use the default Docker Compose file. So, we should be sure that the COMPOSE_FILE surroundings variable is unset earlier than we construct the Docker pictures for the microservices. After that, we will begin the database companies, MongoDB and MySQL:
unset COMPOSE_FILE
docker compose construct
docker compose up -d mongodb mysql
Confirm that the databases are reporting wholesome with the command: docker compose ps. Repeat the command till each report they’re wholesome. Count on a response like this:
NAME ... STATUS ...
chapter06-mongodb-1 ... Up 13 seconds (wholesome) ...
chapter06-mysql-1 ... Up 13 seconds (wholesome) ...
Subsequent, begin the microservices and look within the logs for the startup time (trying to find the phrase Began). Repeat the logs command till logs are proven for all 4 microservices:
docker compose up -d
docker compose logs | grep Began
Search for a response like:
...Began ProductCompositeServiceApplication in 1.659 seconds
...Began ProductServiceApplication in 2.219 seconds
...Began RecommendationServiceApplication in 2.203 seconds
...Began ReviewServiceApplication in 3.476 seconds
Lastly, deliver down the system panorama:
3.4.2. Startup Instances With CRaC
First, declare that we’ll use the CRaC-specific Docker Compose file and begin the database companies, MongoDB and MySQL:
export COMPOSE_FILE=crac/docker-compose-crac.yml
docker compose up -d mongodb mysql
Confirm that the databases are reporting wholesome with the command: docker compose ps. Repeat the command till each report they’re wholesome. Count on a response like this:
NAME ... STATUS ...
crac-mongodb-1 ... Up 10 seconds (wholesome) ...
crac-mysql-1 ... Up 10 seconds (wholesome) ...
Subsequent, begin the microservices and look within the logs for the startup time (this time trying to find the phrase Restored). Repeat the logs command till logs are proven for all 4 microservices:
docker compose up -d
docker compose logs | grep Restored
Search for a response like:
...Restored ProductCompositeServiceApplication in 0.131 seconds
...Restored ProductServiceApplication in 0.225 seconds
...Restored RecommendationServiceApplication in 0.236 seconds
...Restored ReviewServiceApplication in 0.154 seconds
Lastly, deliver down the system panorama:
docker compose down
unset COMPOSE_FILE
Now, we will evaluate the startup occasions!
3.4.3. Evaluating Startup Instances Between JVM and CRaC
Here’s a abstract of the startup occasions, together with calculations of what number of occasions sooner the CRaC-enabled microservice begins and the discount of startup occasions in share:
| MICROSERVICE | WITHOUT CRAC | WITH CRAC | CRAC TIMES FASTER | CRAC REDUCED STARTUP TIME |
|---|---|---|---|---|
| product-composite | 1.659 | 0.131 | 12.7 | 92% |
| product | 2.219 | 0.225 | 9.9 | 90% |
| advice | 2.203 | 0.236 | 9.3 | 89% |
| assessment | 3.476 | 0.154 | 22.6 | 96% |
Typically, we will see a 10-fold efficiency enchancment in startup occasions or 90% shorter startup time; that’s rather a lot!
Observe: The development within the Overview microservice is even higher because it now not handles the creation of database tables. Nonetheless, this enchancment is irrelevant when evaluating enhancements utilizing CRaC, so let’s discard the figures for the Overview microservice.
4. Abstract
Coordinated Restore at Checkpoint (CRaC) is a robust function in OpenJDK that improves the startup efficiency of Java functions by permitting them to renew from a beforehand saved state, a.okay.a., a checkpoint. With Spring Boot 3.2, we additionally get a simplified manner of making a checkpoint utilizing CRaC, often known as computerized checkpoint/restore at startup.
The assessments on this weblog submit point out a 10-fold enchancment in startup efficiency, i.e., a 90% discount in startup time when utilizing computerized checkpoint/restore at startup.
The weblog submit additionally defined how Docker pictures utilizing CRaC could be constructed utilizing a Dockerfile as a substitute of the advanced bash scripts recommended by most weblog posts on the topic. This, nonetheless, comes with some challenges of its personal, like utilizing customized Docker builders for privileged builds, as defined within the weblog submit.
Utilizing Docker pictures created utilizing computerized checkpoint/restore at startup comes with a worth. The Docker pictures will comprise runtime-specific and delicate data, resembling credentials to connect with a database at runtime. Due to this fact, they should be shielded from unauthorized use.
The Spring Boot assist for CRaC doesn’t absolutely cowl all modules in Spring’s eco-system, forcing some workaround to be utilized, e.g., when utilizing Spring Knowledge JPA.
Additionally, when utilizing computerized checkpoint/Restore at startup, the JVM HotSpot engine can’t be warmed up earlier than the checkpoint. If optimum execution time for the primary requests being processed is vital, computerized checkpoint/restore at startup might be not the best way to go.
5. Subsequent Weblog Publish
Within the subsequent weblog submit, I’ll present you use common on-demand checkpoints to unravel a number of the issues with computerized checkpoint/restore at startup.
Particularly, the issues with specifying the runtime configuration at construct time, storing delicate runtime configuration within the Docker pictures, and the way the Java VM could be warmed up earlier than performing the checkpoint.

