We’re going to set out on a mind-blowing tour round community safety. Upon contemplating the nearness and danger posed by cyber threats on this epoch, it is very important stop the threats in order that they don’t trigger irreversible injury throughout the community. This three-part article sequence will take you thru the method of creating a community anomaly detection system utilizing the Spring Boot framework in a sturdy method. The sequence is organized as follows:
- Half 1: We’ll consider the muse and primary construction of our detection system, which must be created.
- Half 2: The second quantity offers with tips on how to help in controlling the diffusion of delicate community info because it targets superior methods for actively monitoring the community at the moment.
- Half 3: Within the final half, machine studying strategies will probably be utilized to the developed system, together with algorithms, which can enhance the system’s efficiency by way of accuracy and skill to detect anomalies.
By the top of this sequence, you should have acquired numerous data in creating a strong-based community anomaly detection system utilizing Spring Boot and making use of applied sciences to enhance your group’s safety degree.
Step 1: Challenge Setup
As an preliminary step within the improvement of our community anomaly detection system, let’s develop a Spring Boot mission during which we are able to make use of all of the wanted dependencies. On this case, Maven will probably be our construct instrument and we are going to add the next main dependencies:
- Spring Internet: For utilizing Spring MVC within the improvement of net functions
- Spring Information JPA: For simpler entry to the database and ORM system
- H2 Database: Light-weight in-memory database for improvement and testing
Let’s go forward and add these essential dependencies to our pom.xml file.
org.springframework.boot
spring-boot-starter-web
org.springframework.boot
spring-boot-starter-data-jpa
javax.persistence
javax.persistence-api
2.2
com.h2database
h2
runtime
Step 2: Mannequin the Community Information
Let’s proceed to outline our core knowledge mannequin. This important part will function the muse for capturing and structuring important info from our community visitors.
package deal com.cyber.sreejith.anomaly.community.mannequin;
import java.time.Immediate;
import jakarta.persistence.*;
@Entity
@Desk(title = "network_data")
public class NetworkData {
@Id
@GeneratedValue(technique = GenerationType.IDENTITY)
non-public Lengthy id;
@Column(title = "source_ip", nullable = true)
non-public String sourceIp;
@Column(title = "destination_ip", nullable = true)
non-public String destinationIp;
@Column(title = "protocol", nullable = true)
non-public String protocol;
@Column(title = "packet_size", nullable = false)
non-public int packetSize;
@Column(title = "timestamp", nullable = true)
non-public Immediate timestamp;
@Column(title = "packetLoss", nullable = false)
non-public double packetLoss;
@Column(title = "throughput", nullable = false)
non-public double throughput;
@Column(title = "latency", nullable = false)
non-public double latency;
@Column(title = "anomaly", nullable = false)
non-public boolean anomaly;
public NetworkData() {}
public NetworkData(String sourceIp, String destinationIp, String protocol, int packetSize, Immediate timestamp) {
this.sourceIp = sourceIp;
this.destinationIp = destinationIp;
this.protocol = protocol;
this.packetSize = packetSize;
this.timestamp = timestamp;
}
public NetworkData(String sourceIp, String destinationIp, int packetSize, Immediate timestamp) {
this.sourceIp = sourceIp;
this.destinationIp = destinationIp;
this.packetSize = packetSize;
this.timestamp = timestamp;
}
public NetworkData(String sourceIp, String destinationIp, int packetSize) {
this.sourceIp = sourceIp;
this.destinationIp = destinationIp;
this.packetSize = packetSize;
}
//Eliminated setter/getters/toString for brevity
}
Step 3: Core Detection Engine
Allow us to now direct our consideration to constructing the guts of this technique, which is the instrument that may deal with and analyze community visitors buildings. This essential unit will use particular algorithms to hold out the conventional operations of looking for patterns within the collected community packets and recognizing irregular ones that counsel doable threats. Saving this engine on this manner will allow it to carry out effectively even when coping with excessive knowledge visitors.
Orchestrate the Detection
The anomaly detection system has been designed with a working module that comes with a complete operate to oversee the entire strategy of detection. Via this multipronged technique, a lot of parallelized algorithms are built-in, permitting evaluation of the system’s real-time safety effectiveness towards a a lot wider perspective of even doable assaults.
public boolean detectAnomaly(NetworkData knowledge)
isHighPacketRate(knowledge) Replace Packet Statistics
This operate first updates our mannequin with respect to the latest community knowledge adopted by empirical evaluation of this knowledge based mostly on a number of anomaly standards utilizing boolean logic.
non-public void updateStats(NetworkData knowledge) {
String sourceIp = knowledge.getSourceIp();
ipStats.putIfAbsent(sourceIp, new PacketStats());
PacketStats stats = ipStats.get(sourceIp);
stats.addPacket(knowledge.getTimestamp());
}Packet Dimension Anomaly
The operate returns true if such packet measurement departs from these limits (i.e., is both too massive or too small), signifying a risk of an anomaly. This easy boolean examine eliminates thousands and thousands of packets that fall exterior regular bounds, which may indicate all kinds of improper actions or issues on the community, together with DoS or DDoS, knowledge leakage, fragmentation, and configuration errors. In filling this operate into our broader anomaly detection scheme, we enhance the possibilities of our system promptly elevating an alarm over suspicious community visitors dealing with, which can be investigated or answered in an automatic method.
non-public static last int MAX_PACKET_SIZE = 10000;
non-public static last int MIN_PACKET_SIZE = 20;
non-public boolean isPacketSizeAnomaly(NetworkData knowledge) {
return knowledge.getPacketSize() > MAX_PACKET_SIZE || knowledge.getPacketSize() Protocol Anomaly
This code establishes a purposeful framework for the community visitors protocol. It additionally has a process to boost alerts the place any community communication employs the usage of protocols apart from these which have been flagged. The applying offers a way of filtering administration of unlawful actions and even makes an attempt to conduct unlawful community operations.
non-public static last Set KNOWN_PROTOCOLS = new HashSet(
Arrays.asList("HTTPS", "SMTP"));
non-public boolean isUnknownProtocol(NetworkData knowledge) {
return !KNOWN_PROTOCOLS.comprises(knowledge.getProtocol().toUpperCase());
} Excessive Packet Charge
The recognized risk operate is kind of essential in stopping community flooding or any Denial of Service (DoS) assault, if any. This operate assesses the frequency of packets from a specific IP deal with by accessing historic recordsdata of that supply IP and checking the dispersion of packets to the given most degree of packets outlined as the utmost doable. When the speed exceeds this threshold, the speed operate returns true as a sign that such visitors is anomalous.
non-public boolean isHighPacketRate(NetworkData knowledge) {
PacketStats stats = ipStats.get(knowledge.getSourceIp());
return stats.getPacketRate() > MAX_PACKETS_PER_SECOND;
} non-public class PacketStats {
non-public Immediate firstPacketTime;
non-public int packetCount;
void addPacket(Immediate timestamp) {
if (firstPacketTime == null || Period.between(firstPacketTime, timestamp).compareTo(TIME_WINDOW) > 0) {
firstPacketTime = timestamp;
packetCount = 1;
} else {
packetCount++;
}
}
double getPacketRate() {
if (firstPacketTime == null) {
return 0.0;
}
Period period = Period.between(firstPacketTime, Immediate.now());
lengthy seconds = period.getSeconds();
if (seconds Suspicious Port
It includes a extra granular operate for evaluating community connections based mostly on the usage of malicious ports. It captures the vacation spot port quantity from the given NetworkData object and matches it with any of the suspicious ports which can be current inside a predefined threshold (31337, 12345, 65535). These ports have additionally been linked to malware, backdoors, and hacking software program. Due to this fact this operate helps stop connecting to such ports which could result in safety breaches, invasion, and malware an infection.
non-public boolean isSuspiciousPort(NetworkData knowledge) port == 12345 non-public int extractPort(String ip) {
String[] elements = ip.break up(":");
return elements.size > 1 ? Integer.parseInt(elements[1]) : -1;
}
Uncommon Timestamp
It carries out this by taking the most certainly present time of the working system and relating it with the time the given NetworkData object was timestamped. If a packet with a NetworkData object is stamped for a future temporal occasion, then the operate returns true as an indicator of a possible anomalous occasion.
non-public boolean isUnusualTimestamp(NetworkData knowledge) {
return knowledge.getTimestamp().isAfter(Immediate.now());
}Step 4: Information Persistence Layer
Let’s proceed with implementing our knowledge entry layer by making a repository interface. This interface will leverage the highly effective capabilities of Spring Information JPA to streamline our database operations. It may well carry out primary CRUD operations by extending JpaRepository. We have additionally added a customized question to retrieve the latest community knowledge entries. The interface features a customized question technique, which makes use of the @Question annotation to specify a JPQL question. This technique retrieves a specified variety of NetworkData entries, ordered by their timestamps in descending order (most up-to-date first).
@Repository
public interface NetworkDataRepository extends JpaRepository {
@Question(worth = "SELECT n FROM NetworkData n ORDER BY n.timestamp DESC LIMIT :limit")
Checklist findTopNByOrderByTimestampDesc(@Param("limit") int restrict);
} This saveNetworkData technique is an information persistence operation inside our community anomaly detection system. It takes a NetworkData object as enter and makes use of the networkDataRepository to avoid wasting this knowledge to the database.
public NetworkData saveNetworkData(NetworkData knowledge) {
return networkDataRepository.save(knowledge);
}The getRecentNetworkData technique is a key part in our community anomaly detection system, designed to retrieve the latest community visitors knowledge. It takes an integer parameter restrict to specify the variety of entries to fetch.
public Checklist getRecentNetworkData(int restrict) {
return networkDataRepository.findTopNByOrderByTimestampDesc(restrict);
} The getAllNetworkData technique offers a complete retrieval mechanism for our community visitors knowledge. It makes use of the findAll() technique, which is robotically offered by Spring Information JPA. This technique fetches all NetworkData entries saved within the database, returning them as a Checklist.
public Checklist getAllNetworkData() {
return networkDataRepository.findAll();
} The deleteAllNetworkData technique invokes the deleteAll() operation offered by the networkDataRepository, which is a part of Spring Information JPA’s commonplace CRUD operations. This technique effectively removes all NetworkData entries from the database, successfully clearing all the assortment of saved community visitors knowledge.
public void deleteAllNetworkData() {
networkDataRepository.deleteAll();
}Step 5: Actual-Time Community Monitoring
Now, let’s create the monitoring class. This can maintain a relentless eye on our community, amassing knowledge and elevating alarms when wanted.
Community Monitoring
The under technique, scheduled to run each 60 seconds, collects community knowledge, checks for anomalies, logs the outcomes, and saves the information.
@Scheduled(fixedRate = 60000) // Run each 60 seconds
public void monitorNetwork() {
NetworkData knowledge = collectNetworkData();
boolean isAnomaly = anomalyService.detectAnomaly(knowledge);
if (isAnomaly) {
knowledge.setAnomaly(true);
logger.warn("Anomaly detected: {}", knowledge);
} else {
knowledge.setAnomaly(false);
logger.information("Normal network activity: {}", knowledge);
}
anomalyService.saveNetworkData(knowledge);
}Community Information Assortment
The under technique simulates the gathering of community visitors knowledge in a managed surroundings. It creates and populates object with mock values for varied community attributes equivalent to supply and vacation spot IP addresses, packet measurement, protocol, packet loss, latency, throughput, and timestamp.
non-public NetworkData collectNetworkData() {
// Simulate community knowledge assortment
NetworkData knowledge = new NetworkData();
knowledge.setSourceIp("10.0.0.1");
knowledge.setDestinationIp("10.1.0.100");
knowledge.setPacketSize(100);
knowledge.setProtocol("http");
knowledge.setPacketLoss(Math.random() * 10); // 0-10% packet loss
knowledge.setLatency(Math.random() * 200); // 0-200ms latency
knowledge.setThroughput(Math.random() * 1000); // 0-1000 Mbps throughput
knowledge.setTimestamp(Immediate.now());
return knowledge;
}Step 6: Simulate Anomaly by way of REST API
The system features a REST API, permitting us to simulate anomalies simply. This API offers a user-friendly interface for testing and experimentation. Nevertheless, in real-world functions, such an API is often pointless. Anomaly detection in real-world situations focuses on steady, real-time community monitoring. Fairly than counting on exterior inputs to set off anomalies, the system robotically detects uncommon patterns as they happen. This strategy ensures well timed detection and response to potential threats. The REST API, whereas helpful for testing, wouldn’t play a central position in manufacturing environments. In observe, the system would operate autonomously to keep up community safety.
Simulate Anomaly
This operate simulates a community anomaly examine. It takes community knowledge as enter and analyzes it to detect any anomalies. After processing, it logs the consequence, saves the information, and returns a response. The response contains the standing of the anomaly, the information itself, and a message that describes the end result.
@PostMapping("/simulate/anomaly")
public ResponseEntityGet Latest Information
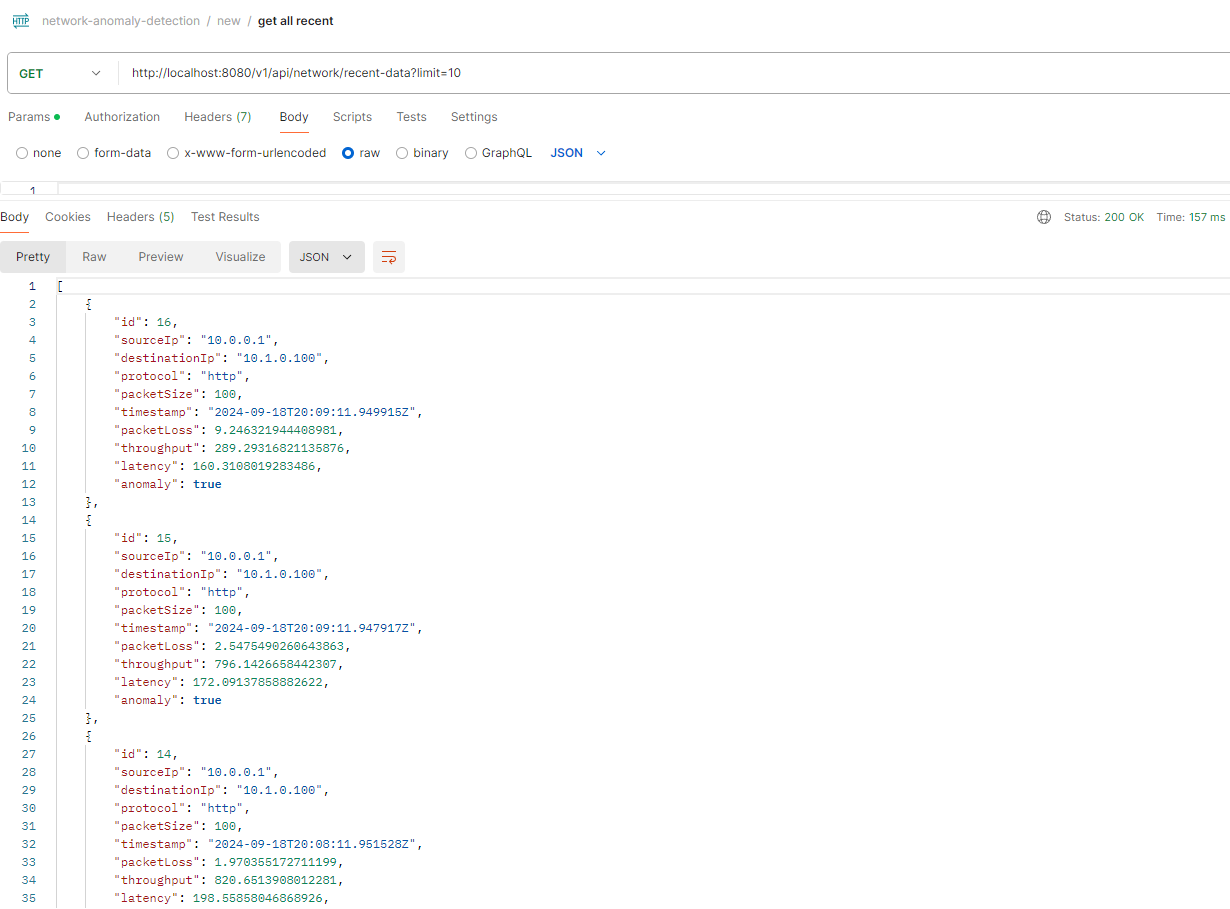
This operate retrieves current community knowledge. It accepts an non-compulsory restrict parameter (defaulting to 10) to specify the variety of current entries to fetch.
@GetMapping("/recent-data")
public ResponseEntity> getRecentData(@RequestParam(defaultValue = "10") int restrict) {
Checklist recentData = anomalyService.getRecentNetworkData(restrict);
return ResponseEntity.okay(recentData);
}
Clear Information
This operate clears all saved community knowledge. It calls the deleteAllNetworkData technique to take away all entries from the database. It returns a affirmation message upon profitable deletion.
@DeleteMapping("/clear-data")
public ResponseEntity clearAllData() {
anomalyService.deleteAllNetworkData();
return ResponseEntity.okay("All network data cleared.");
} Step 7: Scheduler Configuration
Now allow us to proceed in configuring our scheduling part, whose position will probably be to make sure any monitoring work is finished in a well timed method. This configuration part makes use of Spring scheduling infrastructure to carry out time-critical process administration and execution.
Allow Scheduler
This class is a Spring configuration part that serves the aim of enabling scheduling. It’s annotated with @Configuration and @EnableScheduling thus laying down the essential construction of the applying for the applying’s scheduled duties
@Configuration
@EnableScheduling
public class SchedulerConfig {
…..
}Monitor the Community for Every Minute
@Scheduled(fixedRate = 60000) // Run each minute
public void scheduleNetworkMonitoring() {
logger.information("Starting scheduled network monitoring task");
strive {
networkMonitoringService.monitorNetwork();
} catch (Exception e) {
logger.error("Error occurred during scheduled network monitoring: ", e);
}
}
}
Step 8: Testing
To carefully check our API’s capabilities, we’ll make use of Postman to emulate varied community situations:
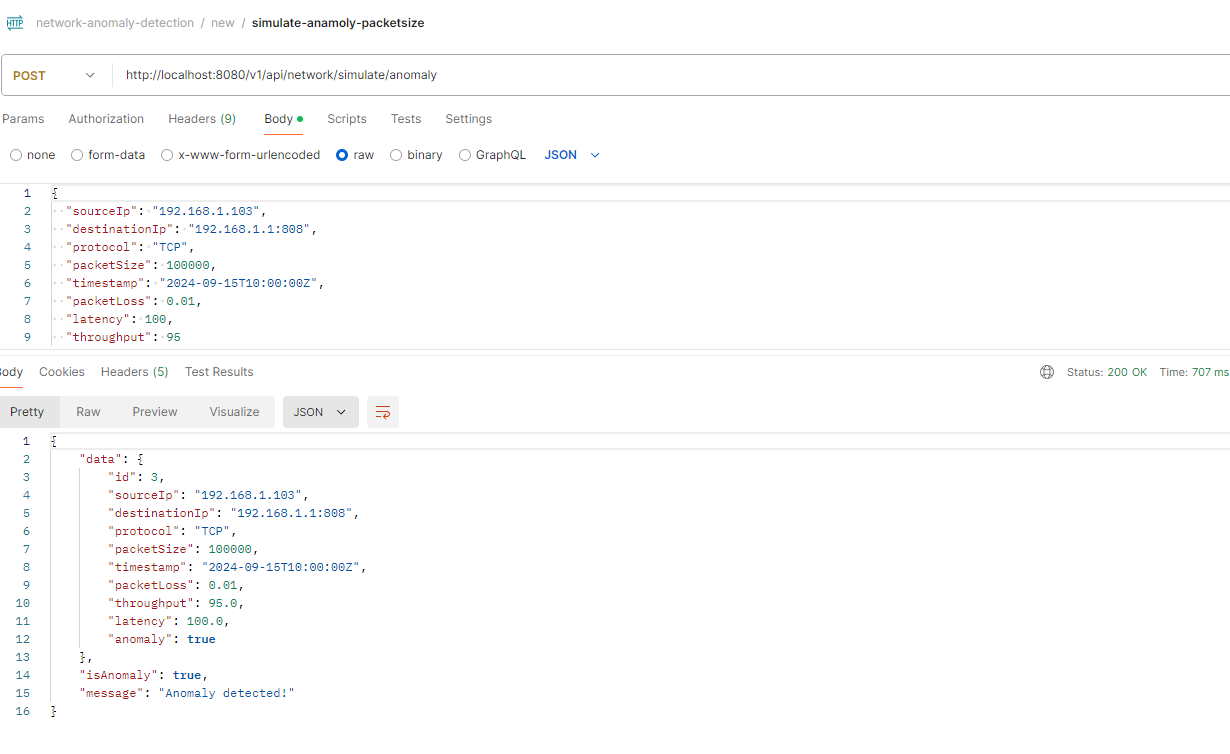
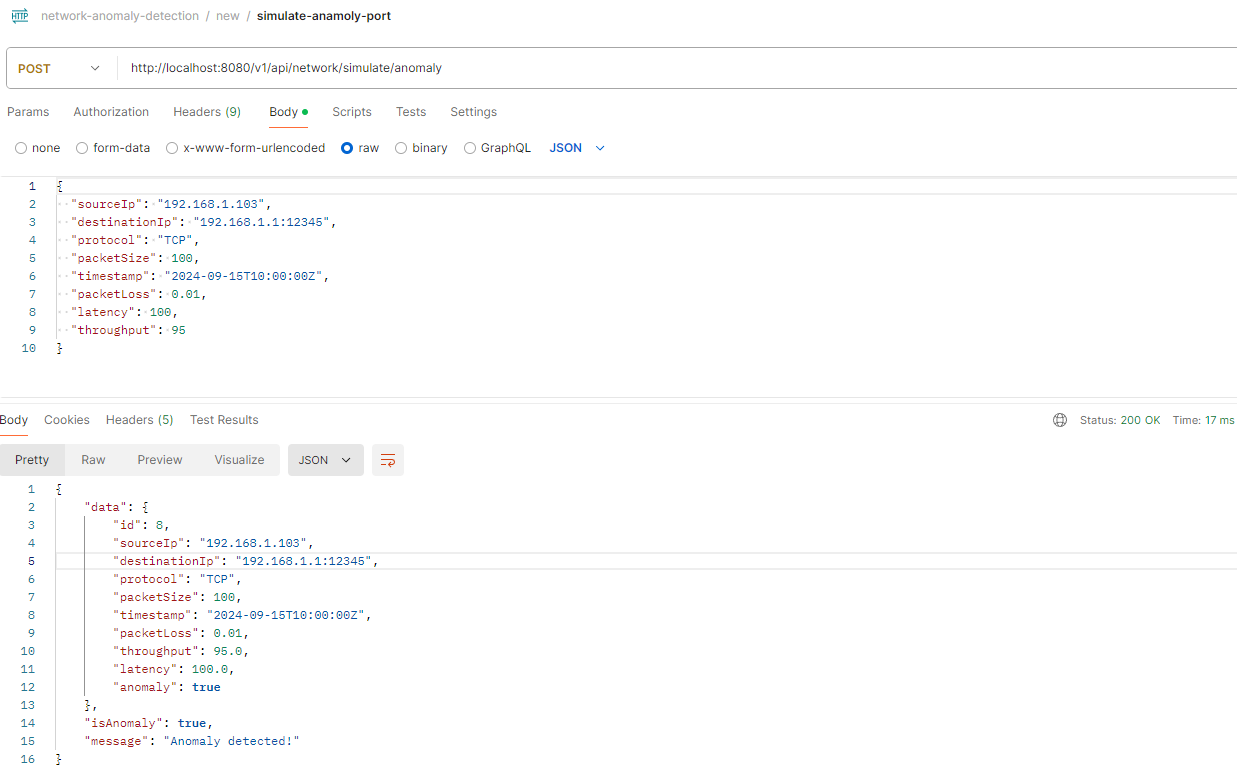
- Elevated packet measurement
- Invalid port in request
Simulate Packet Dimension Anomaly
Simulate an Invalid Port Anomaly
To retrieve the latest community exercise logs, we are able to make the most of the next API endpoint, which fetches knowledge from our in-memory database.
Conclusion
Utilizing the potent options of Spring Boot and the advisable approaches in community safety, a base structure may be created with the purpose of securing the community towards its risks. In filling this vital void, we are going to enhance the system in order to:
- Constantly observe exercise on the community.
- Automate the responses to precise or anticipated threats.
- Make use of clever computational mechanisms to enhance detection effectivity.
- Safe the API via the OAuth 2.0 authorization protocol.
- Develop an interactive front-end interface that may enable the person to make sense of the state of the community.
These enhancements will probably be introduced in later elements of the information.

