First, let’s discover the sensible functions and benefits of deploying IPSec over SD-WAN.
1. Department Workplace Connectivity
- Safe branch-to-branch communication: Securely connects department places of work to one another and to the headquarter utilizing IPSec tunnels over SD-WAN, IPSec gives encrypted and dependable communication.
- Excessive availability: A number of ISP hyperlinks (WAN) will guarantee excessive availability and failover capabilities for essential department workplace functions.
2. Distant Workforce
- Safe distant entry: Staff can have safe entry to their workplace community from house or distant places, the connections are encrypted to company assets.
- Efficiency optimization: SD-WAN optimizes the community by routing visitors throughout the simplest paths
3. Cloud Connectivity
- Safe cloud entry: Connectivity to the cloud is safe utilizing IPSec tunnels with knowledge encryption and safety being its key options
- Hybrid cloud surroundings: SD-WAN can handle visitors between on-premise knowledge facilities and a number of cloud environments, offering dependable and safe knowledge switch.
4. IoT and Edge Gadgets
- Safe IoT communications: Knowledge is transmitted securely from IoT units via IPSec tunnels, defending delicate knowledge.
- Edge computing: SD-WAN and IPSec facilitate knowledge switch to edge computing websites, making certain correct dealing with of knowledge with safe switch.
Steps To Implement FortiGate for IPSec Over SD-WAN
- Think about the next state of affairs
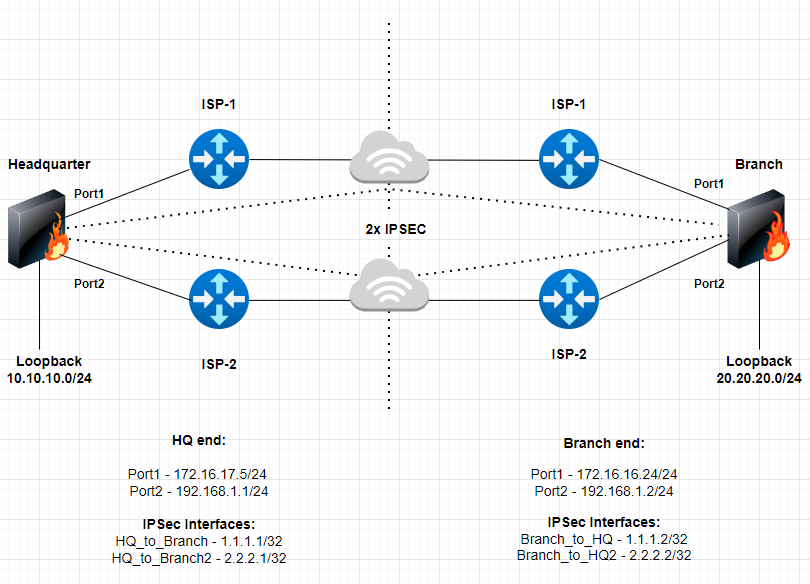
Overview of the Setup
- FortiOS model 7.2.x on Headquarter and Department FortiGate’s (could be applied on 6.4.x).
- Two FortiGate’s in a Headquarter and Department setup
- 2 x ISP connections on every website
- 2x IPSec tunnels on every website
- Loopback’s interface (subnets) used to alternate routes between the 2 websites
1. Steps to Configure VPN Interface on Headquarter and Department Fortigate’s
- Create the VPN interface utilizing SD-WAN VPN.
- Navigate to Community -> SD-WAN, and choose ‘Create New’-> SD-WAN Member
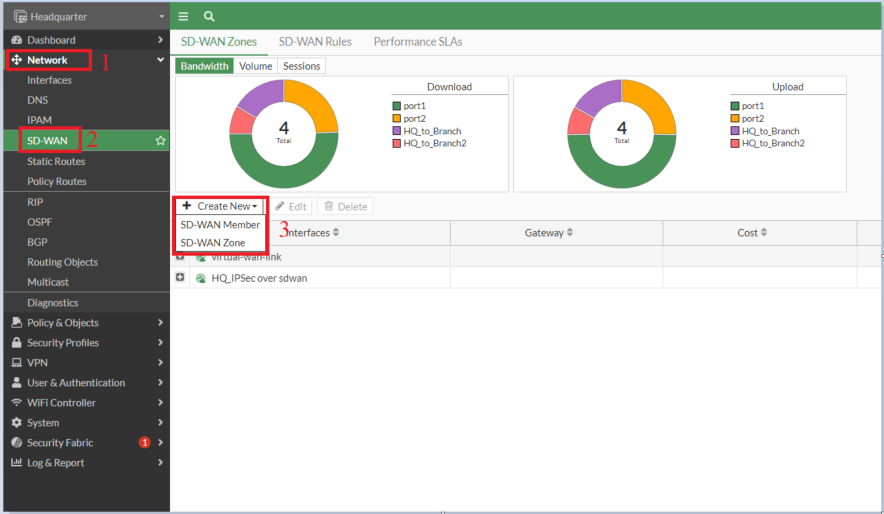
- Choose Interface -> +VPN button -> Create IPSec VPN for SD-WAN interface
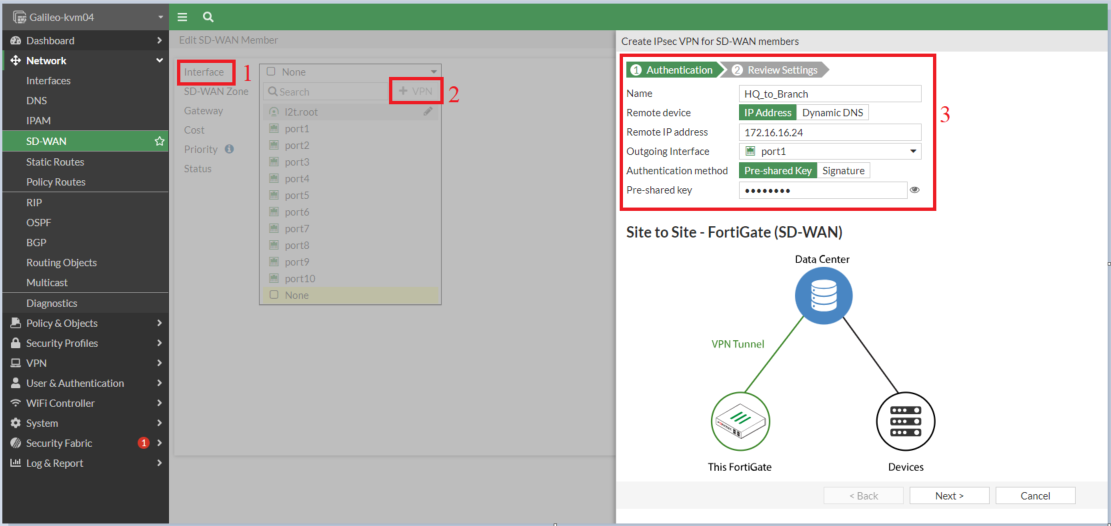
Observe: Within the above screenshot, outgoing interface port1 is the WAN interface
- Now bear in mind we’re creating two IPSec tunnels over Port1 and Port2, so create one other IPSec tunnel interface utilizing the identical steps
- Create a SD-WAN Zone
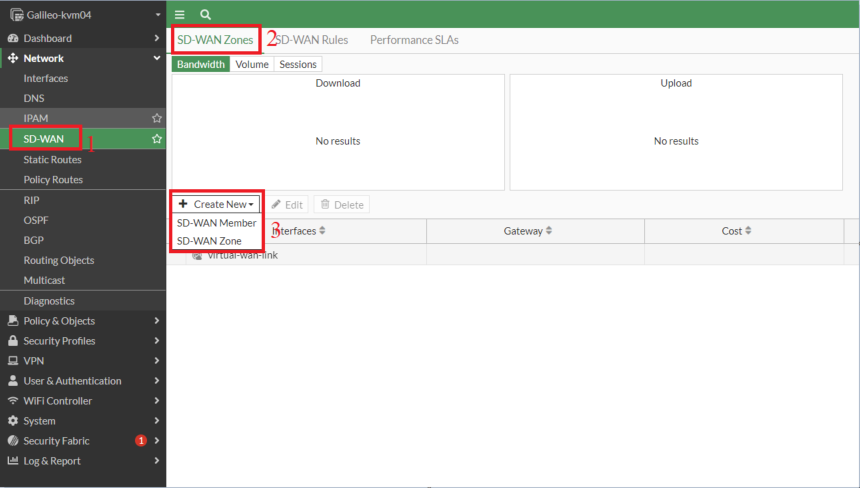
- Add the 2 IPSec tunnel interfaces
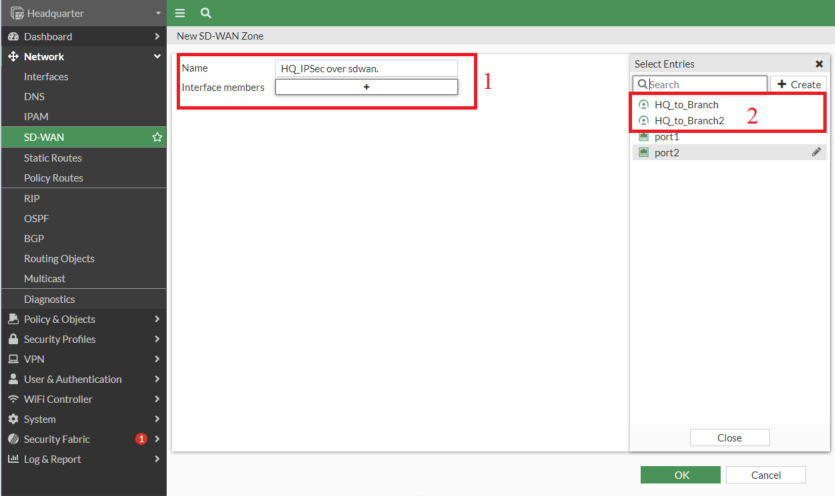
- All of the above steps should be repeated on the Department FortiGate as properly
IMP: We don’t make the most of the IPSec Wizard to create tunnel interfaces as a result of it can’t be invoked inside the SD-WAN member context. The IPSec Wizard generates routes, insurance policies, and addresses which can be appended to the configuration, necessitating their removing to combine the tunnel interface into the SD-WAN member.
2. Configure Section 2 Selectors for Headquarter and Department FortiGate’s
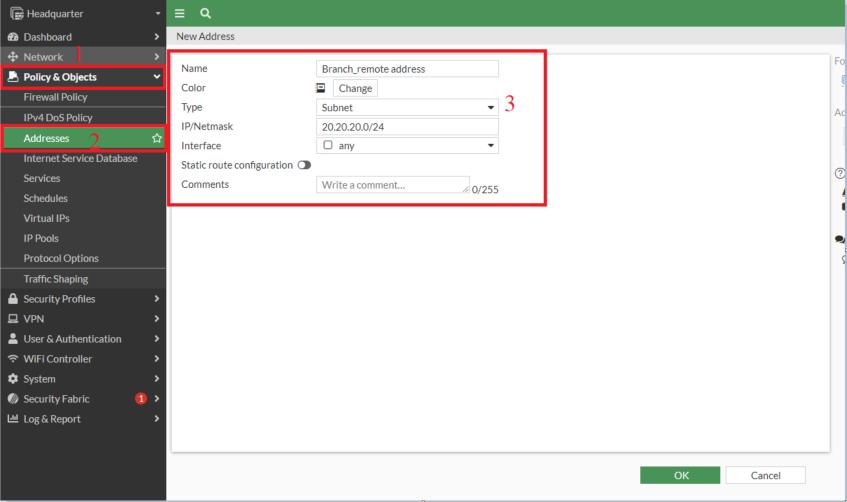
- Creating tackle on Headquarter for “Branch_remote address”: 20.20.20.0/24
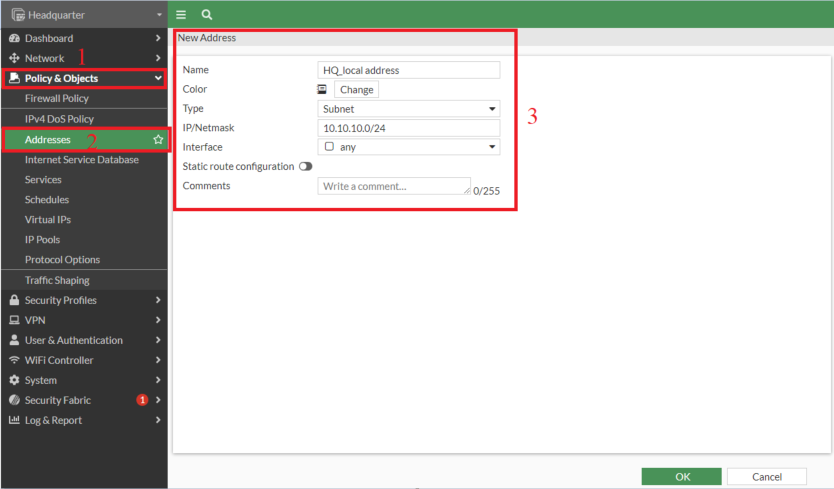
- Creating tackle on Headquarter for “HQ_local address” : 10.10.10.0/24
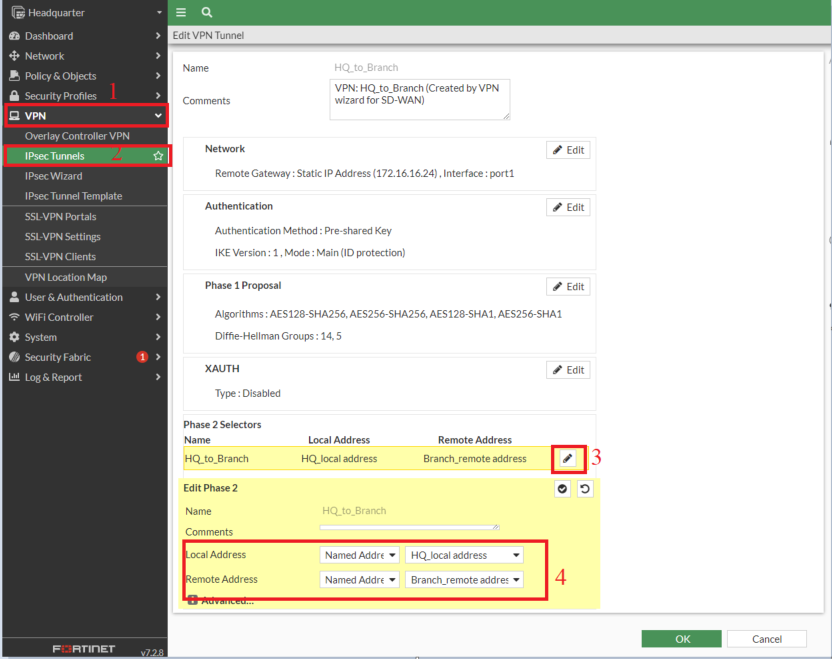
- Including the addresses in Phase2 Selectors
- The identical steps should be applied on the Department FortiGate however make sure the under
- Branch_remote tackle: 10.10.10.0/24
- HQ_local tackle: 20.20.20.0/24
3. Assign IP Addresses to the IPSec Interfaces for Each Tunnels on Headquarter and Department
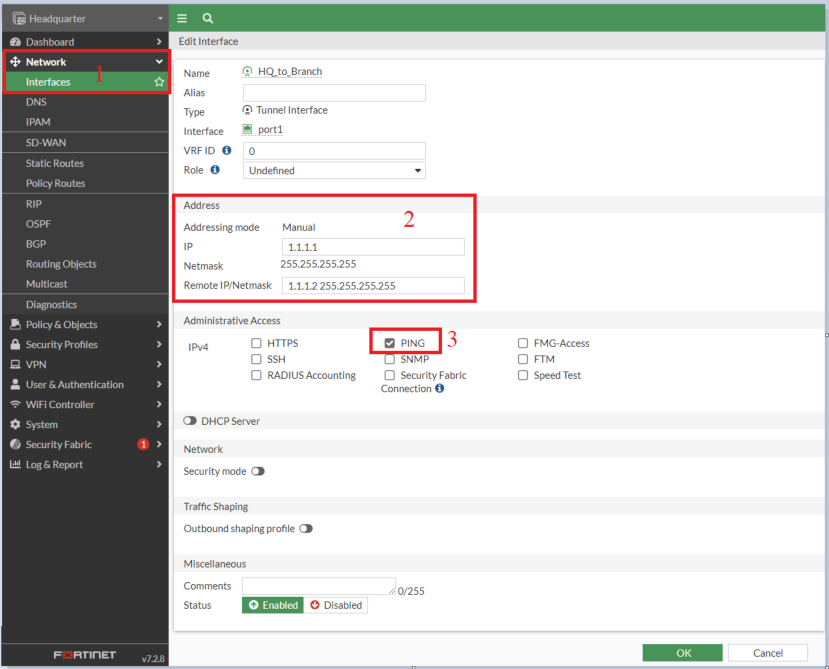
Interface: HQ_to_Branch
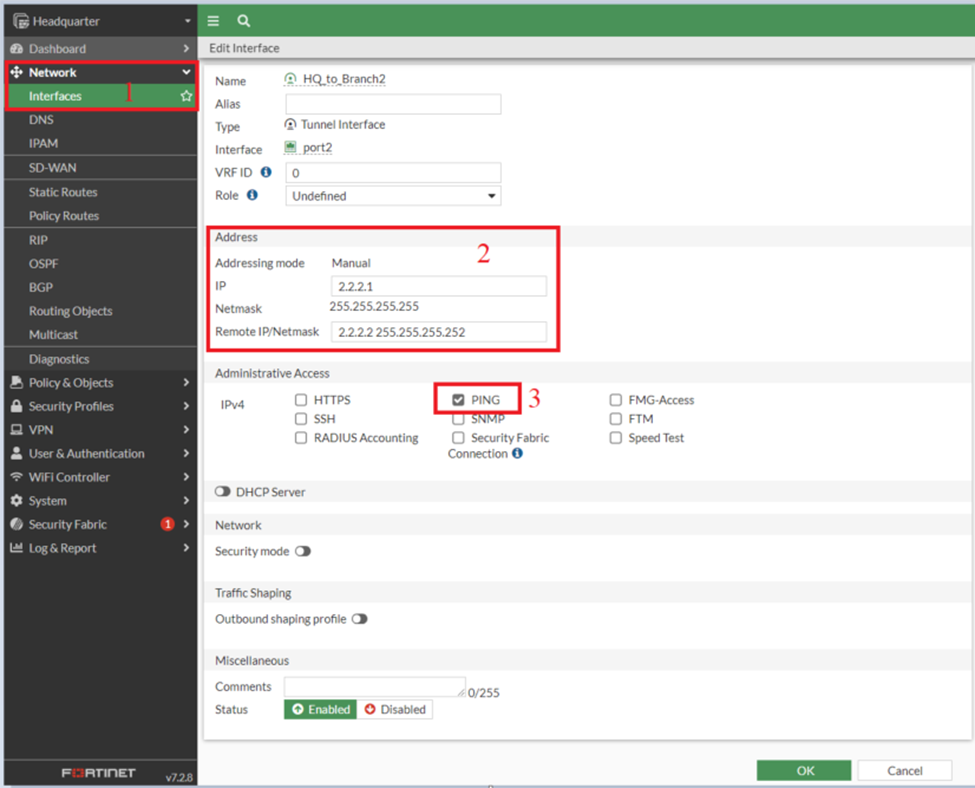
Interface: HQ_to_Branch2
On Department Fortigate
Interface Branch_to_HQ
- IP: 1.1.1.2/32
- Distant IP: 1.1.1.1/32
Interface Branch_to_HQ2
- IP: 2.2.2.2/32
- Distant IP: 2.2.2.1/32
4. Create Static Routes
- Static Routes should be created for the VPN visitors utilizing VPN SD-WAN zone for FortiOS operating v7.0 and above
Observe: In FortiOS v6.4.x, you’ll be able to configure static routes for particular VPN interfaces or for your complete SD-WAN interface, however not for particular person VPN SD-WAN zones. Assist for creating static routes particularly for particular person VPN SD-WAN zones is out there ranging from FortiOS v7.0.
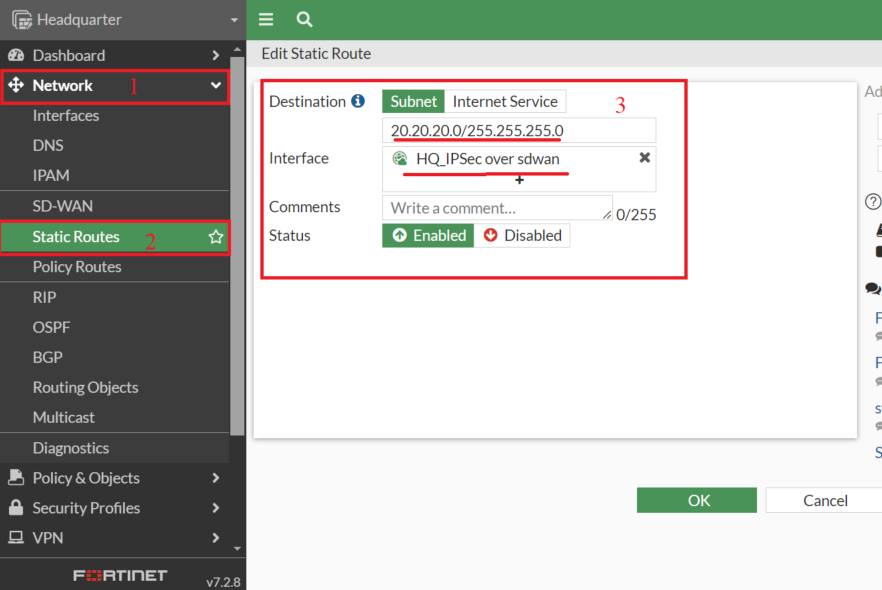
- Equally on the Department finish
Vacation spot: 10.10.10.0/24
Interface: Branch_IPSec over sdwan (SD-WAN Zone)
5. Create Firewall Insurance policies
- Create a firewall coverage for the VPN visitors utilizing the VPN SD-WAN Zone
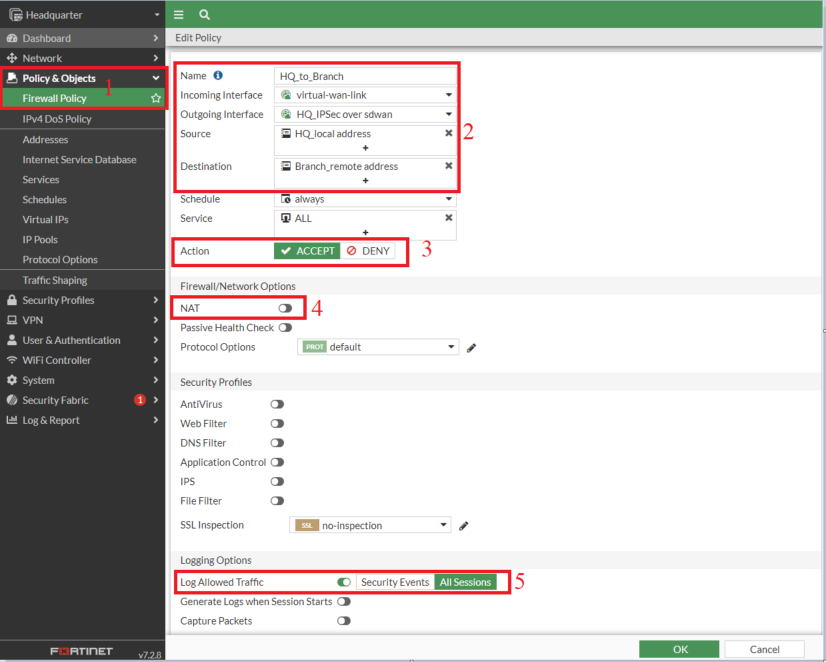
Observe: Be sure that NAT is turned off within the coverage settings; in any other case, visitors will probably be routed via the tunnel interface IP.
- Now create a second coverage for visitors route from Department to Headquarter. You may duplicate it utilizing the clone characteristic, rename the copy, after which allow it.
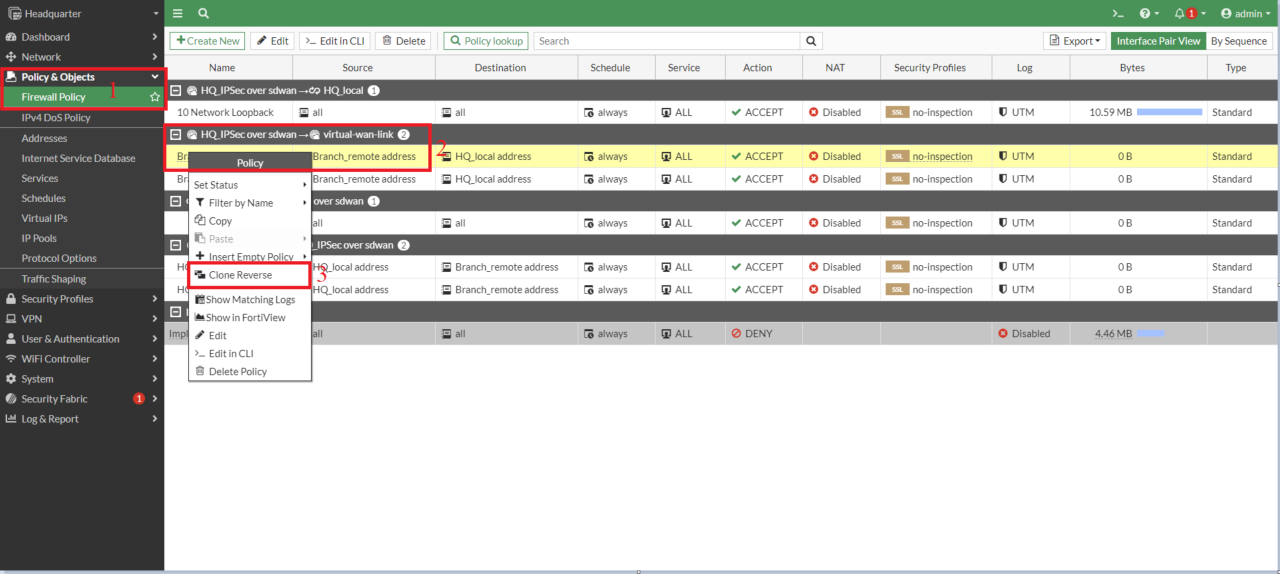 Now similar manner create firewall insurance policies for tunnel HQ_to_Branch2 on Headquarter finish and for Department IPSec tunnels
Now similar manner create firewall insurance policies for tunnel HQ_to_Branch2 on Headquarter finish and for Department IPSec tunnels
6. Organising Efficiency SLA on Headquarter and Department for VPN Interfaces in SD-WAN
- The peer IP used is the loopback interface of the department 20.20.20.1
- We’ve chosen ICMP (ping)
- We’ve enabled the “Update Static Route” choice. It’s used to disable static routes for inactive interfaces, and restores upon restoration.
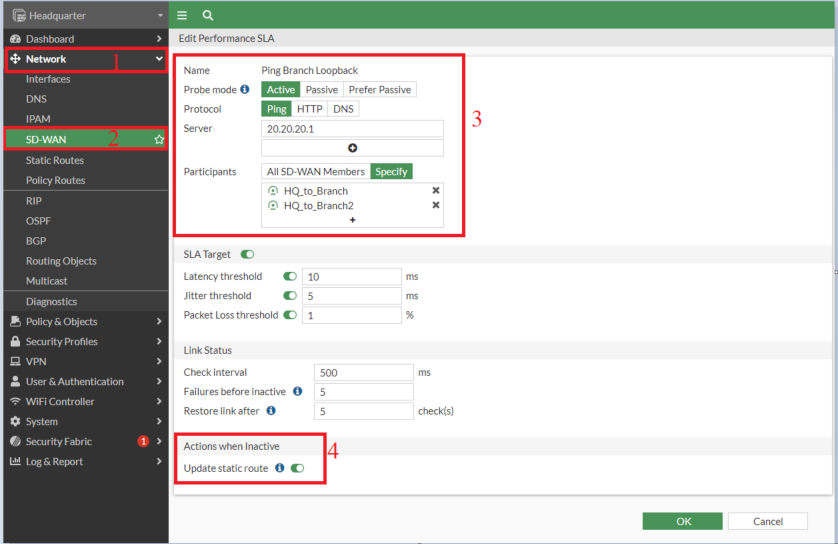
- Now add the supply IP in SD-WAN VPN member from the CLI to make it work. (given under)
- The peer finish configuration must be accomplished for the SLA to be up and dealing, the SLA depends on the tunnel configuration to succeed in the peer finish.
- The supply IP must be an interface IP and it’ll work solely when it’s added to the Section 2 selectors. In our configuration, Headquarter Loopback — 10.10.10.1/24 and Department Loopback — 20.20.20.1/24
Headquarter Fortigate
config system sdwan
config members
edit 3
set interface "HQ_to_branch"
set zone "HQ_IPSec_over_sdwan"
set supply 10.10.10.1 - Equally, on the department add supply ip 20.20.20.1
7. Create SD-WAN rule
- The SD-WAN rule would come with the efficiency SLA
- We’re going to use lowest lowest-cost SLA, however you need to use every other based mostly in your community necessities.
Observe: Latency, Finest High quality, and Lowest Value SLAs make the most of one interface at a time, whereas Most Bandwidth SLA load-balances visitors throughout interfaces.
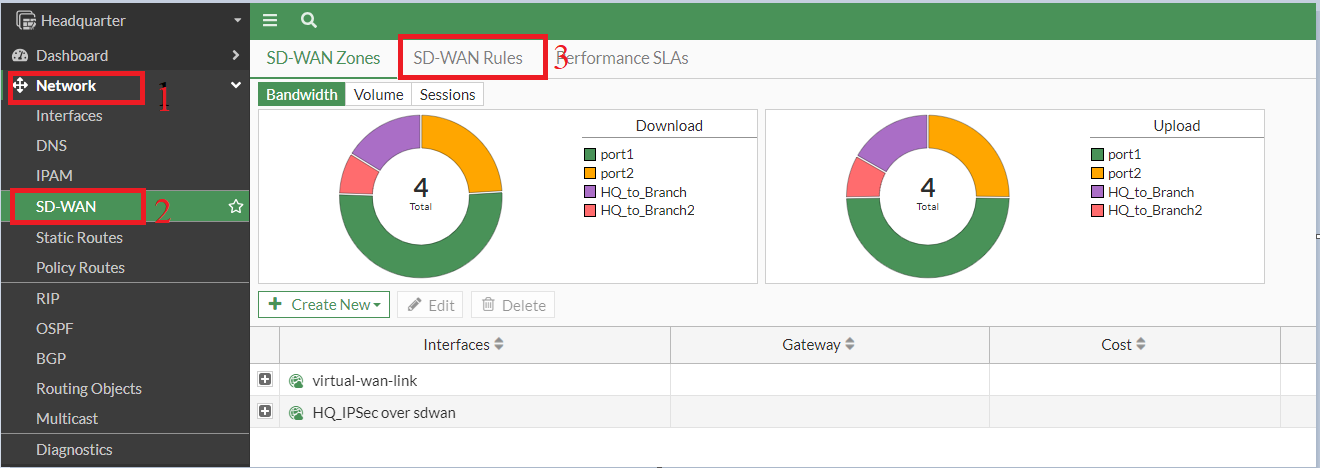
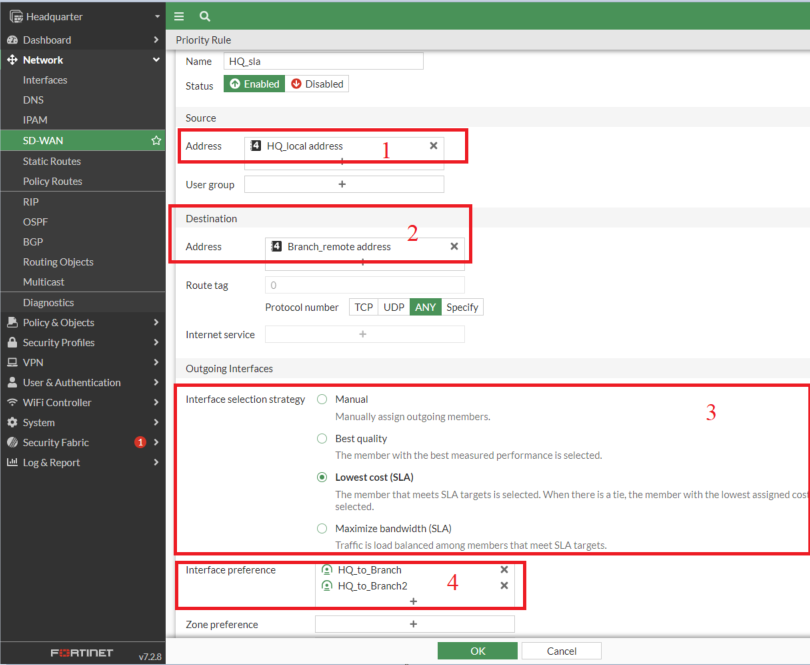
- Make sure the VPN rule is positioned above the all-to-all rule, as guidelines are processed from prime to backside.
8. Create a Blackhole Route
- To forestall visitors from being routed to the ISP hyperlink when each tunnels are down, we have to create a blackhole route for the vacation spot subnets. In any other case, even when the tunnels recuperate, current classes will proceed to make use of the ISP hyperlink till their timeout or handbook clearing, ignoring the tunnels.
Config Router Static
edit 3
set dst 20.20.20.0 255.255.255.0
set distance 15
set blackhole allow
set vrf 0
subsequent
finishObserve: Make sure that the executive distance (AD) worth set for the blackhole route is increased than that of any configured static routes.
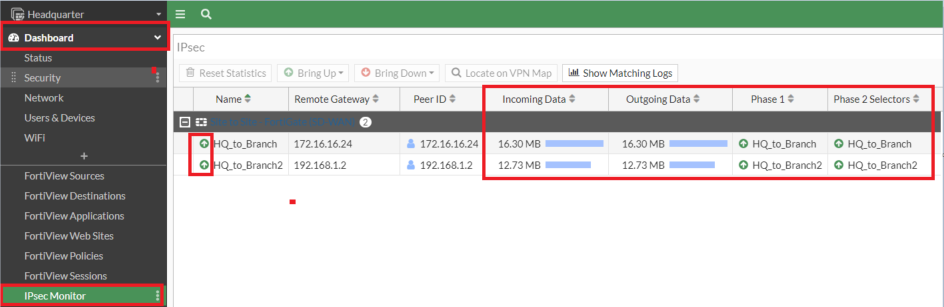
9. Confirm IPSec Tunnel Standing
#get vpn ipsec tunnel abstract
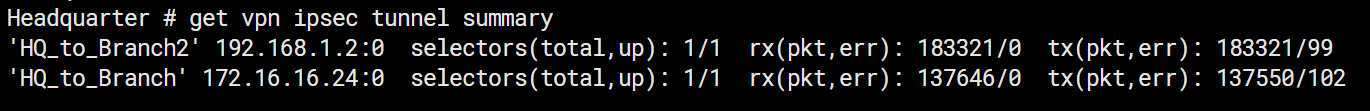
GUI
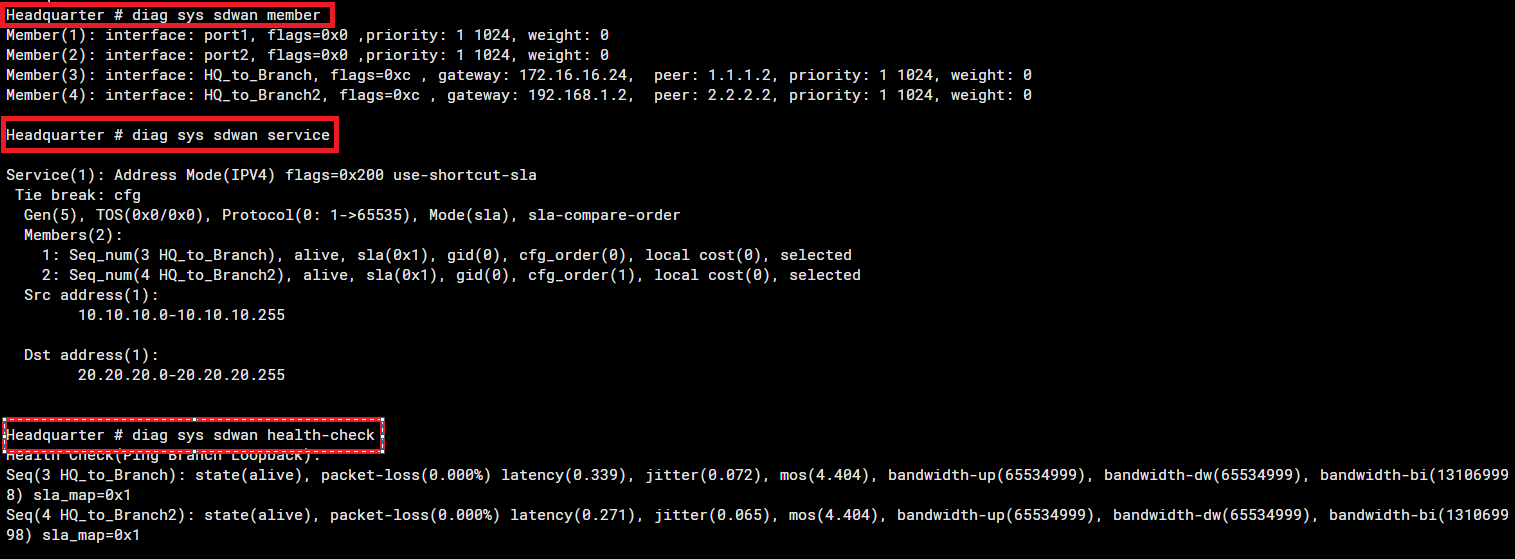
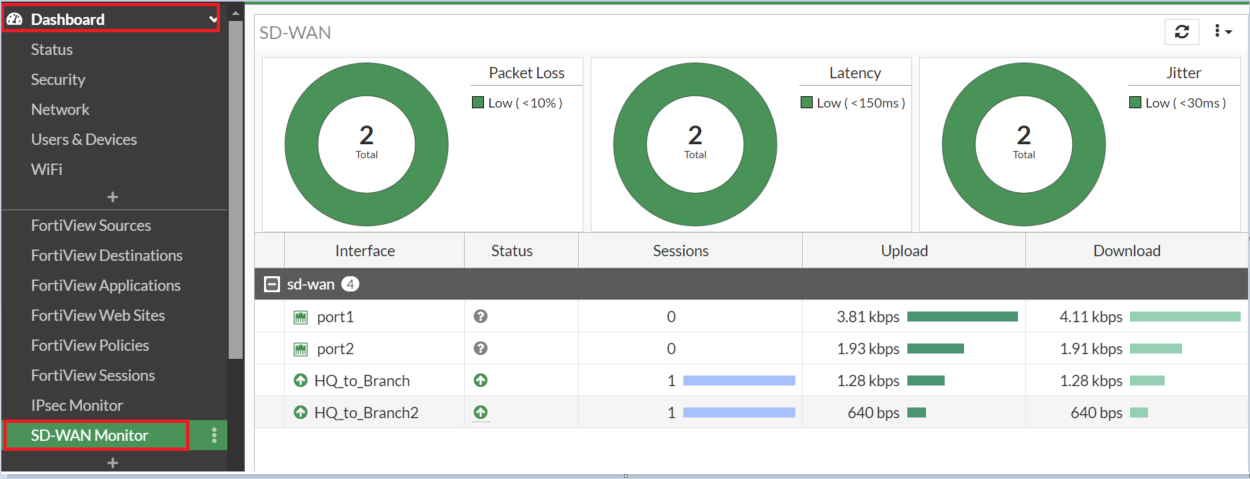
10. Confirm SD-WAN Standing
#diag sys sdwan member
#diag sys sdwan service
#diag sys sdwan health-check
GUI
Conclusion
As cyber threats proceed to evolve, adopting such superior configurations ensures that your community stays resilient, environment friendly, and safe. Investing the effort and time to configure IPsec over SD-WAN on FortiGate not solely fortifies your community but additionally this answer is scalable, requires much less effort and time to arrange, and is straightforward to diagnose for any issues, this additionally future-proofs your community infrastructure. Be at liberty to ask any questions within the feedback.

