Editor’s Notice: The next is an article written for and printed in DZone’s 2024 Pattern Report, Enterprise Safety: Reinforcing Enterprise Utility Protection.
Risk looking is a proactive cybersecurity technique that actively searches for hidden threats all through a company’s total digital surroundings. In contrast to conventional safety measures that primarily react to incidents, menace looking assumes a breach has already occurred and goals to determine malicious exercise earlier than it escalates. By analyzing huge quantities of knowledge from networks, endpoints, and cloud environments, organizations can uncover suspicious patterns, neutralize threats, and considerably scale back their danger of a profitable cyberattack.
This text units the general context and scope for implementing menace detection and looking in software program techniques. We are going to discover new-age practices, superior tooling, and the mixing of AI in menace detection, equipping organizations with the data and instruments to bolster their safety defenses.
Risk Looking
Typical cybersecurity measures — like intrusion detection system, intrusion prevention system, antivirus, and malware supervision — primarily function reactively, counting on predefined signatures and alerts to detect recognized threats comparable to widespread malware and viruses. In distinction, menace looking is a proactive guide or semi-automated course of that actively seeks out hidden threats, together with superior persistent threats (APTs), zero-day vulnerabilities, and insider threats.
Whereas conventional instruments present automated, broad protection, they usually miss subtle threats that evade detection. Risk looking includes deep, hypothesis-driven investigations to uncover unknown threats, specializing in behavioral anomalies and indicators of compromise (IOCs). This proactive strategy enhances a company’s safety posture by reducing the time that threats stay undetected and adapting to the evolving menace panorama.
Risk Modeling vs. Risk Looking
Risk modeling is a proactive course of that identifies potential vulnerabilities in a system earlier than it is constructed. It helps prioritize safety controls. Risk looking is each proactive and investigative, specializing in figuring out lively threats inside recognized compartments or scope. Whereas completely different, they complement one another. Risk modeling informs menace looking by highlighting potential targets, whereas menace looking can reveal vulnerabilities missed in modeling.
Desk 1. Risk modeling vs. menace looking
| Options | Risk Modeling | Risk Looking |
| Intent | Dry run — determine potential dangers and vulnerabilities in a system or software | Risk simulation — proactively detect anomalies and vulnerability threats inside an surroundings |
| Strategy | Preventive, theoretical strategy | Proactive, detective strategy |
| Section | Carried out throughout the design and early growth phases | Carried out towards the tip of implementation and through upkeep |
| Methodology | Risk identification, danger evaluation, mitigation planning | Speculation-driven, data-driven evaluation, anomaly detection |
| End result | Mitigation methods, safety controls | Risk identification, incident response, and safety measure enhancements |
| Modeling instruments | Risk modeling frameworks (STRIDE, PASTA, LINDDUN, VAST), diagramming mapping | Endpoint detection, community evaluation, safety info, occasion administration, and so on. |
| Experience | ISO guide, safety architects, builders, analysts | ISO guide, safety analysts, incident responders, menace intelligence analysts |
| Relationship | Risk modeling identifies potential vulnerabilities that may be focused by menace looking | Risk looking can uncover vulnerabilities that weren’t beforehand recognized via menace modeling |
AI: The Double-Edged Sword of Risk Looking
Risk looking is more and more changing into an enviornment for AI competitors. The cyber menace panorama is a steady arms race, with AI serving as a robust instrument for each attackers and defenders. Malicious actors leverage AI to automate assaults and develop subtle, adaptive malware. In response, organizations are turning to AI-powered menace looking options to proactively detect and reply to those evolving threats.
AI instruments excel at analyzing huge quantities of knowledge in actual time, uncovering hidden patterns and anomalies that may be difficult for people to detect. By integrating machine studying (ML) with menace modeling, AI constantly learns and adapts, enhancing menace detection and enabling the proactive identification and prediction of future assaults. Combining steady studying from ML fashions with human experience and conventional safety controls creates a sturdy protection that’s able to outsmarting even probably the most subtle adversaries.
AI-Pushed Integration of Open-Supply Intelligence in Risk Modeling
The combination of AI and steady open-source intelligence in menace modeling has revolutionized the flexibility to detect and reply to rising threats. Nonetheless, it additionally introduces new challenges and potential threats. Under is a abstract of those facets:
Desk 2. Threats and challenges launched by AI-driven menace modeling
| Points | Examples | |
| New threats launched by AI | AI-powered assaults | Refined phishing, evasion methods, automated assaults |
| Automation of assaults | Velocity and scale, concentrating on and personalization | |
| Challenges to menace modeling | Dynamic menace panorama | Evolving threats, predicting AI behaviors and AL/ML opacity of intermediate state of fashions |
| Information overload | Quantity of knowledge, high quality, and relevance | |
| Bias and false positives | Coaching knowledge bias, false alarms | |
| Complexity and transparency | Algorithm complexity, lack of transparency | |
| Addressing challenges | Common speculation tuning | Steady AI mannequin updates with various knowledge |
| Human-AI collaboration | Human-AI integration for validated outcomes | |
| Superior filtering methods | Filtering and prioritization centered on context | |
| Adoptable, clear, and ruled | Improvement of clear, ruled AI fashions with audits |
By addressing these challenges and leveraging AI’s strengths, organizations can considerably improve their menace modeling processes and enhance their general safety posture. Whereas AI performs an important function in processing huge quantities of open-source intelligence, its integration additionally introduces new challenges comparable to AI-powered assaults and knowledge overload. To successfully counter these threats, a balanced strategy that mixes human experience with superior AI is crucial. Moreover, steady studying and adaptation are very important for sustaining the effectiveness of menace modeling within the face of evolving cyber threats.
Enabling Risk Detection in Software program
Efficient menace detection calls for a sensible, end-to-end strategy. Integrating safety measures throughout the software program lifecycle that minimize throughout the enterprise expertise stack is crucial. By implementing a layered protection technique and fostering a security-conscious tradition, organizations can proactively determine and mitigate threats.
Key Steps of Risk Looking
Under are devoted levels of and steps for approaching an efficient enterprise-wide menace detection technique, together with sensible examples, based mostly on menace modeling.
Stage One: Preparation and Planning
☑ Outline scope: concentrate on particular areas comparable to community, endpoints, and cloud — e.g., shield transaction techniques in a monetary establishment
☑ Determine crucial belongings: decide high-value targets — e.g., affected person information in healthcare and fee card info
☑ Develop hypotheses: formulate educated guesses about potential threats — e.g., brute power assault indicated by failed login makes an attempt
☑ Set up success standards: set metrics for effectiveness — e.g., detect threats inside 24 hours
☑ Assemble workforce: determine required expertise and assign roles — e.g., embrace a community analyst, forensic investigator, and menace intelligence skilled
Stage Two: Information Assortment and Evaluation
☑ Determine knowledge sources: use SIEM, EDR, community logs, and so on. — e.g., accumulate logs from firewalls and servers
☑ Acquire and normalize knowledge: standardize knowledge for evaluation — e.g., guarantee constant timestamping
☑ Enrich knowledge with context: add menace intelligence — e.g., correlate IP addresses with recognized threats
☑ Analyze for anomalies: determine uncommon patterns — e.g., use ML for conduct deviations
☑ Correlate knowledge factors: join associated knowledge to uncover threats — e.g., hyperlink uncommon login instances with community site visitors
Stage Three: Investigation and Response
☑ Validate findings: affirm recognized threats — e.g., analyze recordsdata in a sandbox
☑ Prioritize threats: assess affect and chance — e.g., prioritize ransomware over phishing
☑ Develop response plan: define containment, eradication, and restoration steps — e.g., isolate techniques and restore from backups
☑ Implement countermeasures: mitigate threats — e.g., block malicious IP addresses
☑ Doc findings: file particulars and classes discovered — e.g., doc incident timeline and gaps
Stage 4: Steady Suggestions and Enchancment
☑ Measure effectiveness: consider looking success — e.g., improved detection and response instances
☑ Regulate hypotheses: replace based mostly on new insights — e.g., embrace new assault vectors
☑ Replace playbooks: refine looking procedures — e.g., add new detection methods
☑ Share data: disseminate findings to the workforce — e.g., conduct coaching periods
☑ Keep knowledgeable: monitor rising threats — e.g., subscribe to menace intelligence feeds
Determine 1. Risk looking course of
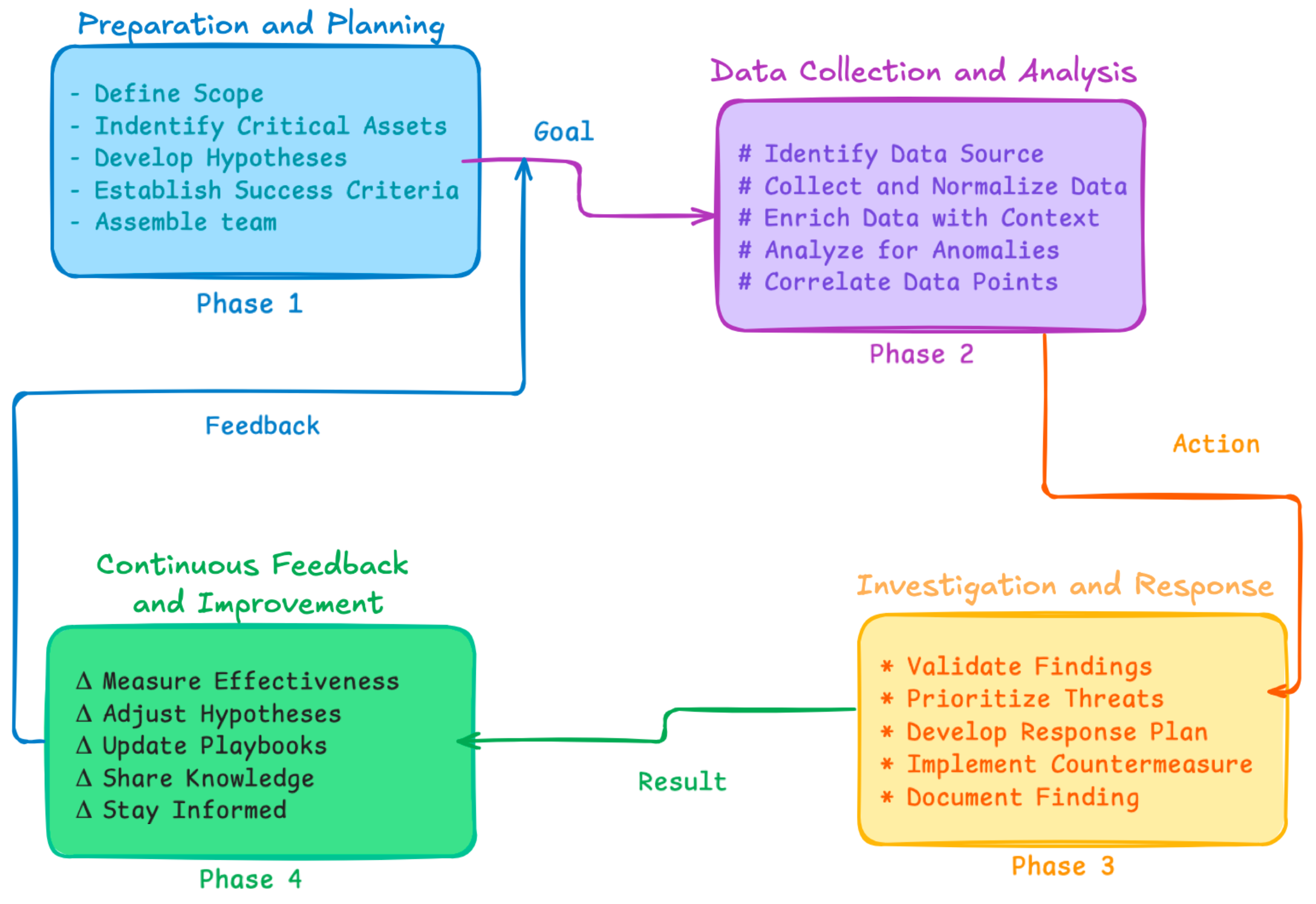
By following these steps, organizations can improve their menace looking capabilities and enhance their general safety posture.
Bridging the Hole: How Detection Engineering Enhances Risk Looking
Detection engineering focuses on constructing a sturdy basis of safety controls to guard in opposition to recognized threats. By growing and refining detection guidelines, leveraging SIEM techniques, and automating alerts, organizations can successfully determine and reply to malicious exercise. Steady testing and validation, together with the mixing of menace intelligence, be sure that these defenses stay updated and efficient.
Whereas detection engineering is important for sustaining sturdy defenses, it isn’t foolproof. Even probably the most subtle detection techniques could be bypassed by APTs and different stealthy adversaries. That is the place menace looking steps in: By proactively trying to find hidden threats which have evaded present defenses, menace looking uncovers IOCs and behavioral anomalies that automated techniques may miss. Whereas detection engineering supplies the required instruments and infrastructure to acknowledge recognized threats, menace looking extends this functionality by exploring the unknown, investigating refined indicators of compromise, and validating the effectiveness of present controls.
When detection engineering and menace looking are mixed, they create a robust synergy that considerably enhances a company’s cybersecurity posture. Detection engineering supplies a sturdy framework for figuring out and responding to recognized threats effectively, making certain that safety techniques are effectively ready to deal with acquainted dangers. Then again, menace looking takes a proactive stance, constantly difficult and bettering these techniques by uncovering beforehand unknown threats and refining detection methods.
This twin strategy not solely strengthens defenses in opposition to a large spectrum of cyberattacks but additionally promotes a tradition of steady enchancment, permitting organizations to deal with each recognized and rising threats with agility and precision. By integrating these two disciplines, organizations can construct a complete and adaptive protection technique, significantly enhancing their general resilience in opposition to evolving cyber threats.
Key Concerns Round Efficient Risk Looking
In a fancy cybersecurity panorama, efficient menace looking requires extra than simply the best instruments; it calls for a strategic strategy that considers varied essential facets. This part delves into the important thing components that contribute to profitable menace looking operations, together with the roles and tasks of various workforce members, the significance of various knowledge sources, and the steadiness between automation and human experience. By understanding these parts and integrating them into your menace looking technique, organizations can proactively determine threats, scale back dwell time, and enhance their general incident response capabilities.
Desk 2. Efficient menace dealing with facets
| Points | Particulars |
| Anticipated outcomes | Proactive menace identification, diminished dwell time, improved incident response |
| Roles and tasks | Risk hunters (who lead threats simulation), analysts (knowledge evaluation for speculation), responders (mitigate actors for threats) |
| Sources | Open-source knowledge, industrial menace intelligence feeds, intelligence-sharing communities |
| Incorporation | Enriching menace looking hypotheses, validating findings, updating looking playbooks |
| Stability | Mix human experience with automation for optimum outcomes |
| Instruments | SIEM, EDR, SOAR, AI-powered analytics platforms |
| Steady studying | Attend trade conferences, webinars, and coaching |
| Group engagement | Take part in safety boards and communities |
Conclusion
In at present’s more and more advanced cyber menace panorama, it’s important to anticipate and tackle threats earlier than they materialize. By implementing the outcomes of menace modeling hypotheses, organizations can drive steady enchancment and determine key areas for enhancement. Collaboration is equally essential — partnering with like-minded organizations for joint hackathons and drills fosters shared studying, greatest practices, and heightened preparedness. Common chaos-themed drills additional construct resilience and readiness for real-world incidents.
Investing in AI-driven instruments and integrating AI into menace simulation and anomaly detection are not non-obligatory however obligatory. AI and ML fashions, with their potential to retain and study from previous patterns and traits, present steady suggestions and enchancment. This enhances menace detection by figuring out refined patterns and anomalies inside huge datasets, maintaining organizations one step forward of rising threats. Finally, steady proactive menace looking ensures a sturdy protection in opposition to the ever-evolving menace panorama.
Adopting these proactive menace looking ideas and practices is crucial for staying forward of threats and malicious stealth actors. By actively looking for out and figuring out hidden threats earlier than they’ll trigger injury, organizations can preserve a sturdy protection. This proactive strategy ensures that safety groups can detect and neutralize superior assaults that may evade automated techniques, maintaining organizations secure and resilient in opposition to evolving cyber threats.
That is an excerpt from DZone’s 2024 Pattern Report,
Enterprise Safety: Reinforcing Enterprise Utility Protection.Learn the Free Report

