Deploying microservices in a Kubernetes cluster is vital in 5G Telecom. Nonetheless, it additionally introduces important safety dangers. Whereas firewall guidelines and proxies present preliminary safety, the default communication mechanisms inside Kubernetes, corresponding to unencrypted community visitors and lack of entry management, are inherently insecure. This insecurity may compromise delicate knowledge. Due to this fact, implementing further safety measures inside every microservice pod is not only a advice however an important step to make sure safe communication inside the cluster. So, further configuration inside every software is required.
Istio offers a strong answer to those challenges by successfully managing communication between particular person 5G telecom microservice pods. With its management aircraft, Istio mechanically injects a sidecar proxy into particular person microservices pods, making certain safe and environment friendly communication.
Let’s dive deep.
What Is Istio?
Istio is an important open-source service mesh that seamlessly integrates with microservices-based purposes, simplifying monitoring, administration, and implementing efficiency and safety insurance policies. It prevents overload, restricts unauthorized entry, and secures knowledge in transit. Its assist system unifies and ensures easy operations for microservices, considerably streamlining their administration and making certain efficiency and safety necessities are met effortlessly.
What Is a Sidecar Proxy?
A sidecar proxy is a separate container that runs alongside a Kubernetes microservice pod. It’s chargeable for offloading capabilities required by all purposes inside Istio. The sidecar proxy, a strong element of Istio Structure, intercepts the applying’s incoming and outgoing community visitors. It allows telecom operators to use insurance policies and make the most of the talked about resiliency options, and it empowers operators to carry out superior capabilities on the interface level with the surface world, showcasing the capabilities of Istio Structure.
Structure
The spine of Istio’s structure is considerably formed by two essential elements, every enjoying a pivotal function in its performance:
- The info aircraft, a pivotal a part of Istio’s structure, contains a set of proxies (deployed utilizing Envoy, an open-source proxy for distributed purposes) that run alongside microservices as sidecar containers.
- The management aircraft, a decisive component in Istio’s structure, manages the proxies and dictates their actions. Let us take a look at every element in additional element. It contains the next elements:
- Pilot: Manages service discovery and visitors.
- Citadel: Manages safety and allows safe communication.
- Galley: Validates and distributes configuration assets.
- Mixer: Handles coverage enforcement and telemetry assortment.
- Sidecar Injector: Mechanically injects Envoy sidecar proxies into Kubernetes pods for simple integration.
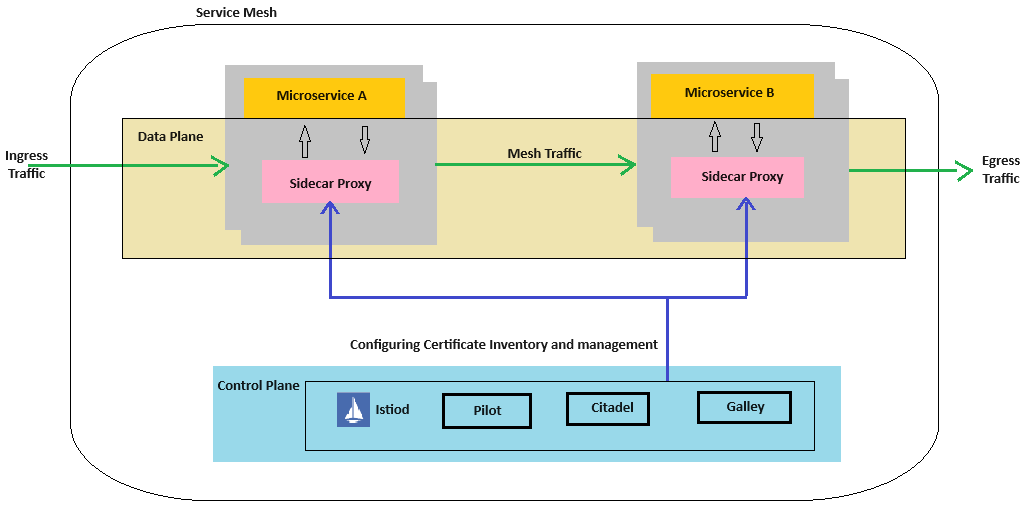
To clarify how Istio Structure works, we’ll use the instance based mostly on the above structure diagram, the sidecar proxy deployed with Microservice-A and Microservice-B ensures seamless and environment friendly communication. The sidecar proxy intercepts community visitors, empowering the applying to implement and implement insurance policies, make the most of resiliency options, and allow superior capabilities.
When Microservice-A sends a request to Microservice-B, the sidecar proxy identifies the vacation spot, forwards the request, and checks the service-to-service communication coverage to find out if the decision ought to undergo based mostly on safety, efficiency, and reliability. This strategy of intercepting, forwarding, and checking ensures that the request is dealt with appropriately. If the request goes by, Microservice-B processes the request, prepares the response, and sends it again over the community, which is intercepted and forwarded by the sidecar proxy to the shopper after which to the vacation spot software, Microservice A.
Understanding the Significance of Istio Service Mesh for Kubernetes Microservices
The Istio service mesh is crucial in Kubernetes. Whereas Kubernetes manages microservices, it does not deal with visitors stream administration, entry insurance policies, or telemetry knowledge assortment. Istio offers these capabilities with out requiring adjustments to software code, making it a horny answer for managing microservices in Kubernetes utilizing sidecar containers. It might probably run in any distributed atmosphere, offering a safe answer for cloud or on-premises purposes.
Istio helps Kubernetes distributions, together with managed companies like EKS and self-managed clusters. It additionally works with totally different software orchestration platforms and all microservices purposes, together with serverless architectures.
Benefits of Istio
Istio affords a number of vital advantages for Kubernetes and Istio-compatible platforms:
- Safety: Enforces sturdy authentication and authorization necessities between microservices.
- Utility efficiency: Effectively routes visitors between microservices and handles retries and failovers.
- Observability: Collects telemetry knowledge from particular person microservices for detailed visibility into well being and efficiency.
- Troubleshooting: Displays every microservice individually to establish and handle efficiency and safety points.
General, Istio simplifies administration for admins of recent, microservices-based purposes.
Configuration YAMLs (But One other Markup Language)
The Service Mesh Management Aircraft manages proxies to route visitors, offers coverage and configuration for knowledge planes, and empowers directors to outline and configure numerous companies. As soon as configured, the SMCP distributes obligatory info to the service mesh’s knowledge aircraft, permitting proxies to dynamically adapt their habits.
Telecom Operators can set up and run SMCP (Service Mesh Management Aircraft) utilizing the configuration beneath:
SMCP YAML
apiVersion: maistra.io/v2
sort: ServiceMeshControlPlane
metadata:
identify: full-install
namespace: istio-system
spec:
model: v2.1
techPreview:
meshConfig:
defaultConfig:
concurrency: 8 # Regulate based on the necessity
proxy:
runtime:
container:
assets:
requests:
cpu: 500m
reminiscence: 256Mi
limits: # Regulate based on the necessity
cpu: "1"
reminiscence: 1Gi
tracing:
sampling: 10000 # 0.01% increments. 10000 samples 100% of traces
kind: Jaeger
gateways:
ingress: # istio-ingressgateway
service:
kind: ClusterIP
ports:
- identify: status-port
port: 15020
- identify: http2
port: 80
targetPort: 8080
- identify: https
port: 443
targetPort: 8443
meshExpansionPorts: []
egress: # istio-egressgateway
service:
kind: ClusterIP
ports:
- identify: status-port
port: 15020
- identify: http2
port: 80
targetPort: 8080
- identify: https
port: 443
targetPort: 8443
additionalIngress:
some-other-ingress-gateway: {}
additionalEgress:
some-other-egress-gateway: {}
coverage:
kind: Istiod
telemetry:
kind: Istiod
addons:
grafana:
enabled: true
kiali:
identify: kiali
enabled: true
set up: # set up kiali CR if not out there
dashboard:
viewOnly: false
enableGrafana: true
enableTracing: true
enablePrometheus: true
jaeger:
identify: jaeger-production
set up:
storage:
kind: Elasticsearch
elasticsearch:
nodeCount: 3
redundancyPolicy: SingleRedundancy
indexCleaner:
enabled: true
numberOfDays: 7
schedule: 55 23 * * *
ingress:
enabled: true
runtime:
elements:
tracing.jaeger.elasticsearch: # solely helps assets and picture identify
container:
assets:
limits:
cpu: 1
reminiscence: 1Gi
requests:
cpu: 500m
reminiscence: 1Gi
pilot:
deployment:
autoScaling:
enabled: true
minReplicas: 2
maxReplicas: 2
targetCPUUtilizationPercentage: 85
pod:
tolerations:
- key: node.kubernetes.io/unreachable
operator: Exists
impact: NoExecute
tolerationSeconds: 60
affinity:
podAntiAffinity:
requiredDuringScheduling:
- key: istio
topologyKey: kubernetes.io/hostname
operator: In
values:
- pilot
container:
assets:
limits: # Regulate based on the necessity
cpu: "1"
reminiscence: 1GiThe Service Mesh Member Roll unequivocally identifies the initiatives related to the Service Mesh management aircraft. Solely, initiatives enlisted on the roll are impacted by the management aircraft. Including a mission to the member roll hyperlinks it to a selected management aircraft deployment.
Telecom Operators can set up and run SMMR (Service Mesh Member Roll) utilizing the configuration beneath:
SMMR YAML
apiVersion: maistra.io/v1
sort: ServiceMeshMemberRoll
metadata:
identify: default
namespace: istio-system
spec:
members:
- # namespace that wants be istio injected. Set up
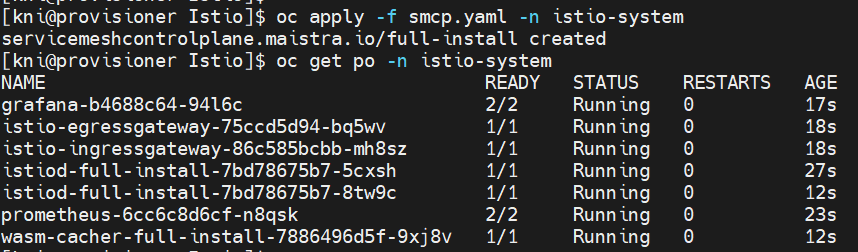
1. Set up the SMCP (Service Mesh Management Aircraft) as beneath.
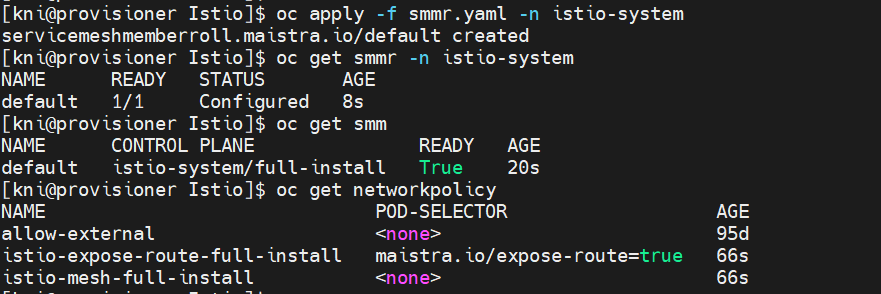
2. Set up the SMMR (Service Mesh Member Roll) as beneath.
Conclusion
Istio simplifies communication between 5G telecom microservices pods in a Kubernetes atmosphere and allows seamless connectivity, management, monitoring, and safety of microservice architectures throughout totally different platforms. It helps workloads in containers and digital machines.
With Istio, the way forward for Telecom IoT microservice pod structure seems promising, with improved effectivity, safety, and scalability.

