Spoofing is a sort of cyber-attack utilized by hackers to realize unauthorized entry to a pc or a community, IP spoofing is the commonest sort of spoofing out of the opposite spoofing methodology. With IP Spoofing the attacker can conceal the true supply of the IP packets to make it troublesome to know the origin of the assault. As soon as entry to a community or a tool/host is achieved, cybercriminals often mine them for delicate information, with computer systems they’ll flip into zombies and can be utilized to launch Denial-of-Service (DoS) assaults.
What Is IP Spoofing?
IP addresses are used for communication between gadgets on the web. Cybercriminals use a false supply IP handle to cover and impersonate one other system. Basically making it tougher for the vacation spot system to detect. Such assaults include the intent to steal delicate information, infect your laptop with malware or viruses, and even crash your server.
How IP Spoofing Works
So, let’s get deeper into how IP spoofing works. An IP handle is a sequence of numbers that identifies your system on the web and each system that connects to the web has an IP handle with its use they’re able to trade information., beneath is what an IP header packet appears like
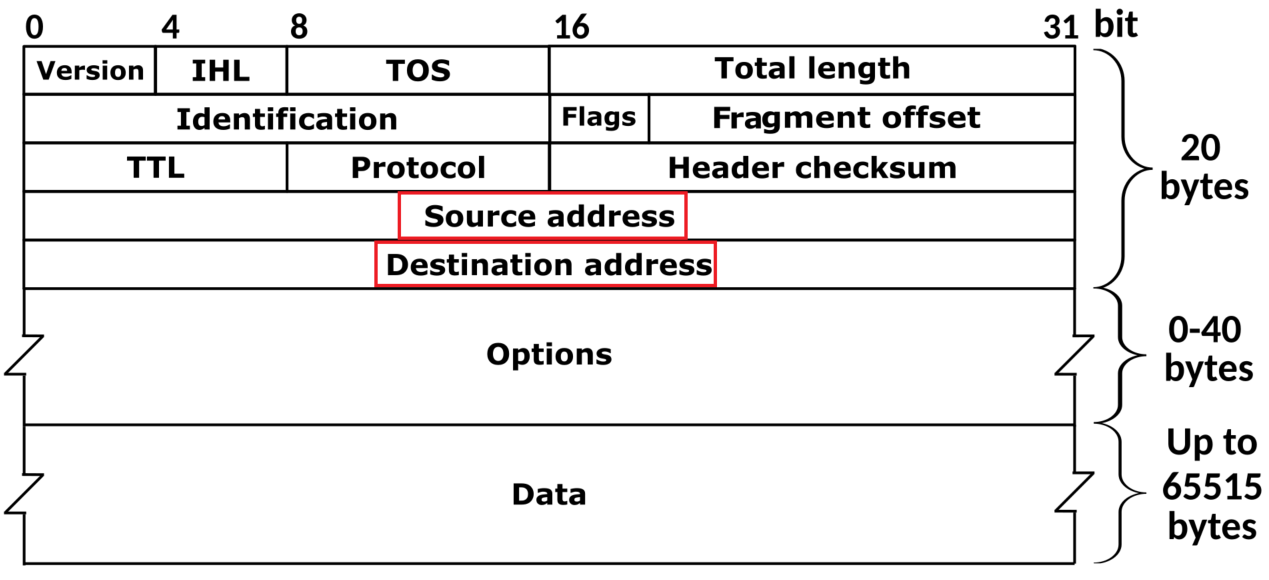
IP Spoofing takes benefit of the supply by faking the supply contained in the packet equally it is like placing a faux return handle on an envelope in a mailbox. More often than not when an IP packet travels to succeed in its vacation spot it goes over a number of intermediate gadgets or routers which don’t examine the supply handle in any respect.
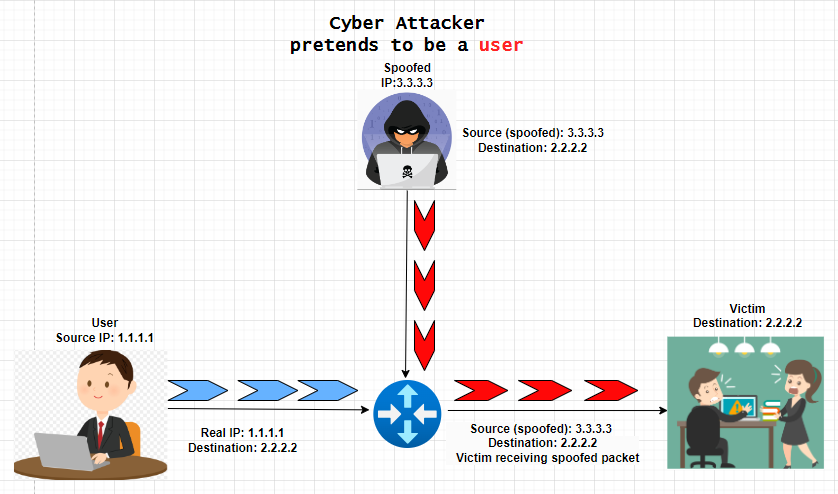
Within the beneath instance, you may see that the cyber attacker has efficiently modified the supply IP of the packet from 1.1.1.1 to three.3.3.3 (modified IP).
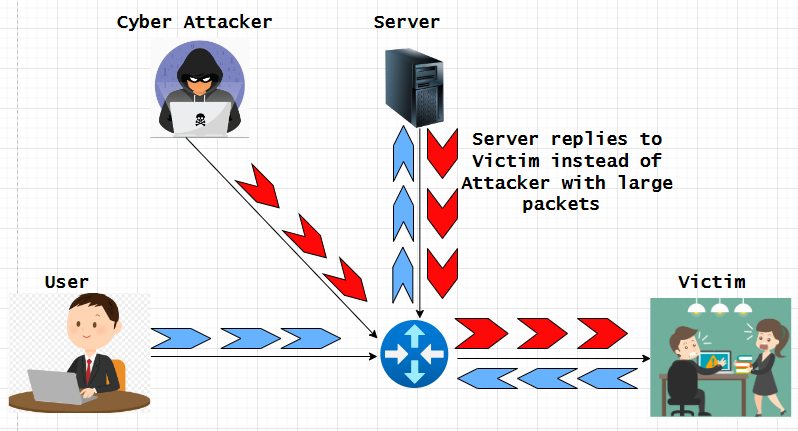
Now, for example that somebody desires to disrupt and utterly disconnect their web service, they’ll ship packets with a faux supply handle to that sufferer with so many packets that the sufferer has no sources to course of professional packets. An attacker can use many alternative faux supply addresses throughout many packets and sometimes it is not possible to hint again the attacker to its origin to dam the assault on the sufferer it will get even worse when an attacker can commandeer intermediate nodes to amplify an assault by triggering that node to ship the sufferer very massive packets which takes extra sources to course of as seen within the picture beneath.
Forms of IP Spoofing
The beneath three are the commonest forms of IP Spoofing
1. Distributed Denial of Service (DDoS) Assaults
A Distributed Denial of Service (DDoS) assault is the commonest cyber assault which makes use of a spoofing methodology, primarily the focused host, service, or community is flooded with Web site visitors.
Key Traits of DDoS Assaults
- Quantity-based assaults: The thought is to saturate the bandwidth of the goal host. Among the methods are to carry out ICMP floods, UDP floods, and different spoofed packet floods. The assault is measured in bits per second (bps).
- Protocol assaults: These assaults work on exploiting weaknesses in community protocols. For instance, in TCP it could use SYN floods. Fragment packet assaults are one other instance the place packets are fragmented and reassembled to evade safety controls and launch assaults. Ping of loss of life and Smurf DDoS are a number of the others. These assaults are measured in packets per second (pps).
- Utility layer assaults: These goal particular functions or providers, making the assault appear to be professional site visitors. Examples embody HTTP floods, GET/POST floods, and Slowloris. These assaults are measured in requests per second (rps).
2. Masking Botnet Gadgets
IP Spoofing can be utilized to entry computer systems by masking botnets. A botnet as soon as it good points entry to a PC is utilized by the perpetrator to regulate from a single supply. The PCs which can be affected by the botnet perform malicious assaults on attackers’ behalf.
3. Man-In-The-Center Assaults
Man-in-the-middle assault is used to change packets and transmit them with out the unique sender or receiver figuring out. If attackers spoof an IP handle and acquire entry to non-public accounts, they’ll observe any facet of the communication. As soon as entry is achieved, private data could be simply stolen, perpetrators can direct customers to faux web sites, and extra. Over time hackers gather a wealth of confidential data they’ll use or promote — which implies a man-in-the-middle assault could be extra beneficial and profitable than the others.
How To Detect IP Spoofing
Community monitoring instruments can be utilized to research site visitors at endpoints. Though it is troublesome for finish customers to detect IP spoofing assaults, the change of supply IP is completed within the Community layer i.e. Layer 3 of the Open System Interconnection communications mannequin. For the reason that modification is completed at a packet stage it would not go away an indication of alterations. Often, spoofed connection requests can seem real from the surface. Let’s focus on the methods you may mitigate such assaults:
- Packet filtering: It’s used to research packets to examine for any inconsistencies between the packet’s IP handle and the IP handle detailed on the entry management listing (ACLs), it’s used to detect tampered packets.
- Ingress filtering: Verify incoming packets to evaluate whether or not the supply IP header matches a permitted supply handle. If it fails the examine, the packet is dropped.
- Egress filtering: Outbound packets are verified for his or her supply addresses which do not match with those of the group’s community. This prevents inner customers from initiating IP spoofing assaults
How To Defend Towards IP Spoofing
With the best way IP Spoofing works, it conceals the attacker’s id as it’s exhausting to hint again to its unique supply. Nevertheless, we are able to take some anti-spoofing steps to decrease the dangers of such assaults.
- Always scanning networks for irregular actions
- Packet filtering mechanisms to detect supply IPs divergent from the group’s registered community
- Authenticating all IP addresses and deploying a community attack-prevention instrument
- Enabling Reserve Path Forwarding on Routers/Firewalls to confirm that site visitors is to be blocked on an interface whether it is sourced from solid IP addresses.
Instance of a Spoofing Assault
GitHub Spoofing Assault (2019)
In July 2019, a classy phishing marketing campaign focused GitHub customers, the target was to steal their login credentials and two-factor authentication (2FA) codes. The intrusion concerned spoofing strategies the place the attackers pretended as GitHub and different well-known entities to realize the belief of customers to surrender delicate data.
Assault Particulars
- Phishing emails: Emails had been despatched by the attackers that introduced themselves to be from GitHub. The message within the electronic mail was to inform the person about suspicious login makes an attempt, account safety issues, or required updates making a scenario of excessive significance for the safety of their account urging customers to click on on a hyperlink to safe their accounts.
- Spoofed web sites: The URL hyperlinks took the customers to web sites that mirrored GitHub’s login web page. Now when the customers entered their credentials, the attackers captured this data.
- Credential harvesting: As soon as the person entered their credentials and the 2FA codes on the spoofed web sites, attackers had been in a position to collect this data. This enabled the attackers to realize unauthorized entry to the person’s GitHub accounts.
- Exploitation: Entry to GitHub accounts, will doubtlessly lead as much as loads of exploitation.
- Alter or delete code repositories
- Entry non-public repositories containing delicate data.
- Use the compromised accounts to launch additional assaults inside the community or group
Conclusion
IP Spoofing stays a prevalent and harmful sort of cyberattack that permits perpetrators to realize unauthorized entry to networks and methods by concealing their true id. Altering the supply IP handle and tracing it again to the origin of the assault is considerably troublesome. As mentioned within the GitHub spoofing assault, numerous techniques had been used and so they had been efficient in deceiving customers to present you their delicate information, resulting in credential theft, unauthorized entry, and additional exploitation.
To mitigate such assaults we have to make use of a complete community monitoring system, instruments similar to packet filtering, and ingress and egress filtering. Additionally, superior strategies like enabling Reverse Path Forwarding on routers and firewalls will assist confirm the supply of the IP packet.
A proactive strategy is a should to guard networks and customers from IP spoofing assaults which would scale back the danger and influence of such assaults and assist to safeguard delicate information.

