DevOps has turn into the groundwork for delivering top-notch functions shortly and effectively in immediately’s agile improvement. Its effectivity and velocity may also trigger notable safety threats if vulnerabilities are usually not managed correctly.
Sixty % of information breaches succeed as a result of organizations fail to use identified, obtainable patches earlier than the weaknesses are exploited.
This piece explores the important thing significance vulnerability administration performs in DevOps infrastructure, spotlighting strategies to include resilient defenses whereas retaining the swiftness and creativity offered by DevOps.
The Necessities of Vulnerability Administration
Vulnerability administration is an indispensable a part of the safety measures of a company. It’s a preventive methodology that spots, examines, handles, and critiques the safety weaknesses in programs and software program.
Unpatched vulnerabilities performed a task in 60% of information breaches. vulnerability administration goals to alleviate the probabilities menace actors could have for exploitation. It consists of key elements which embrace:
- Identification: This entails scanning software program and programs to search out weaknesses.
- Analysis: This has to do with reviewing the strengths and anticipated outcomes of the weaknesses discovered.
- Therapy: Taking steps to amend vulnerabilities
- Reporting: Noting and speaking the place and development of safety enhancement efforts
Frequent Kinds of Vulnerabilities in Software program and Infrastructure
Weaknesses inside infrastructure and software program can prevail in quite a few varieties, widespread varieties embrace:
- Code flaws: Issues in software program code may be taken benefit of.
- Configuration points: Errors in functions or safety could make safety susceptible.
- Outdated software program: Working outmoded editions with confirmed flaws
- Weak authentication: Insufficient safety measures that may be evaded very simply
- Third-party elements: Weaknesses in exterior dependencies included within the software program.
The Influence of Unmanaged Vulnerabilities on DevOps Workflows
Unmanaged weaknesses can have a big affect on DevOps workflow. This may result in important repercussions, together with leveraging weaknesses to breach programs inflicting extreme monetary and reputational harm.
Operational disruption can also be an influence of unmanaged vulnerabilities. When an assault targets a weak spot it might disrupt providers and result in a system downtime which can have an effect on the continuity of enterprise.
Incapacity to deal with vulnerabilities can lead to non-compliance with the regulatory framework, attracting authorized penalties. Lastly, the market place and reliability of a company are additionally at stake right here, unwavering safety issues can deplete clients’ and stakeholders’ belief.
Integration of Vulnerability Administration in DevOps
DevSecOps entails including safety measures to each software program improvement section. This methodology contains cooperation between operation, improvement, and safety groups, making safety a collective obligation.
Specializing in safety from the beginning allows figuring out and resolving points early to forestall them from turning into hurdles at a later time. This technique helps scale back the chance related to safety points afterward when the software program is accomplished.
CI/CD pipelines are pivotal, they automate integration and ship code adjustments. Together with safety scans in these pipelines can permit for constant weak spot assessments, ensuring that upon modification it’s put to check for safety points. Working these automated assessments alongside regular assessments offers fast responses to builders to resolve points that may turn into a roadblock to the event course of.
Automated Instruments
To handle safety vulnerabilities, it is very important use automated instruments. Various kinds of instruments apply to completely different phases.
- Static Software safety testing (SAST): These instruments verify the code for weaknesses earlier than it’s deployed.
- Dynamic Software Safety Testing (DAST): Dast instruments discover vulnerabilities in an utility or system that’s already executed.
- Software program Composition Evaluation (SCA): Software program composition evaluation instruments observe exterior dependencies used within the mission for recognized safety issues.
As well as, GitLab CI, Jenkins, and CircleCI are instruments that may simply mix safety checks into the creation course of. It permits for fixed commentary and fast patches to any safety dangers.
Complete Vulnerability Administration Technique
In accordance with analysis by Optimistic Applied sciences, 84 % of corporations have high-risk vulnerabilities on their exterior networks. The analysis additionally hinted that greater than half of those weaknesses may be erased just by putting in updates.
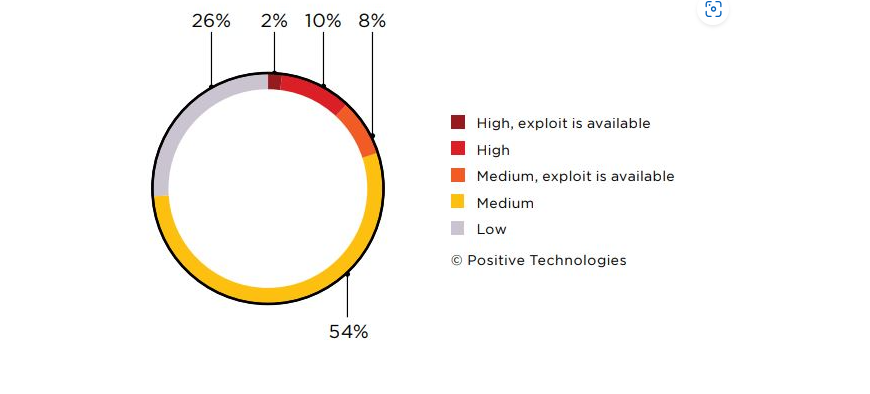
Picture Supply
Step one in complete vulnerability administration is finishing up rigorous assessments that contain discovering susceptibilities that exist inside software program and programs. As soon as these weaknesses have been recognized, rank them so as of precedence; that’s, concentrate on probably the most important publicity first, as high-risk vulnerabilities may cause better harm. Decrease dangers needs to be resolved later.
Establishing well-defined vulnerability administration guidelines is indispensable. This guideline ought to draft how weaknesses might be recognized, reported, and reviewed. The duty of staff members also needs to be clarified to verify everybody is aware of the function they play in safety repairs.
A classy framework contains:
The worth of an enlightened staff can’t be overstated. To maintain your DevOps staff up to date on new safety dangers and their mannequin procedures, common coaching and consciousness applications are wanted.
These applications ought to handle how you can uncover susceptibilities in code and software program, how safety instruments can be utilized effectively, and the advantages of compliance with vulnerability administration coverage. When your staff is enhanced with the best expertise and data, vulnerabilities might be preemptively recognized and alleviated earlier than they’re capitalized on.
Safety is a steady operation, not a activity to be carried out as soon as. To regulate to new dangers and weaknesses, safety baselines needs to be commonly up to date and maintained. This entails:
- Monitoring programs and software program commonly
- Making use of updates and patches immediately
- Revising safety insurance policies as essential
- Conducting audits and assessments to make sure compliance with safety requirements and uncover the areas that want enchancment
Embracing a Proactive Safety Tradition in DevOps
To keep up the integrity and safety of cutting-edge programming, efficient vulnerability administration in a DevOps surroundings is essential. Integrating safety practices into each section of DevOps improvement can assist organizations preemptively uncover and mitigate weaknesses making certain a strong and resilient infrastructure.
DevOps continues to evolve and so do cyber threats. To keep up reliability and be secure from unfolding dangers within the digital terrain prioritize safety, and embrace a tradition of steady progress.

