The swift progress in cloud expertise has made information and utility safety an essential requirement slightly than only a desire. As extra buyer companies are transferring their operations to the cloud, safeguarding their cloud workloads — referring to all deployed purposes and providers — has develop into more and more important. Cloud Workload Safety (CWP) is essential on this space as a result of it ensures that these workloads stay safe and resilient in opposition to a rising vary of threats.
Why CWP Is Important
CWP is a necessity that should not be ignored. Because the adoption of cloud expertise grows, the size and complexity of threats additionally escalate. Listed below are the explanation why CWP is crucial:
- Elevated risk surroundings: Cyber threats have gotten extra advanced and frequent. CWP instruments are crafted to detect and counter these altering threats in actual time, delivering enhanced safety for cloud workloads uncovered throughout varied networks and environments.
- Safety in opposition to information breaches and compliance: Knowledge breaches can result in extreme monetary and reputational hurt. CWP instruments help organizations in complying with strict rules like GDPR, HIPAA, and PCI-DSS by implementing robust safety protocols and compliance checks.
- Upkeep of operational integrity: It’s important for companies to take care of the uninterrupted operation of their cloud workloads with out being affected by safety incidents. CWP instruments provide intensive risk detection and automatic responses, minimizing disruptions and upholding operational integrity.
- Price implications: Safety breaches can incur substantial prices. Investing in CWP instruments helps avert these dangers by early identification of vulnerabilities and threats, lastly defending organizations from potential monetary losses resulting from breaches and repair interruptions.
The beneath image depicts the parts, functionalities, and platforms supported by CWP.
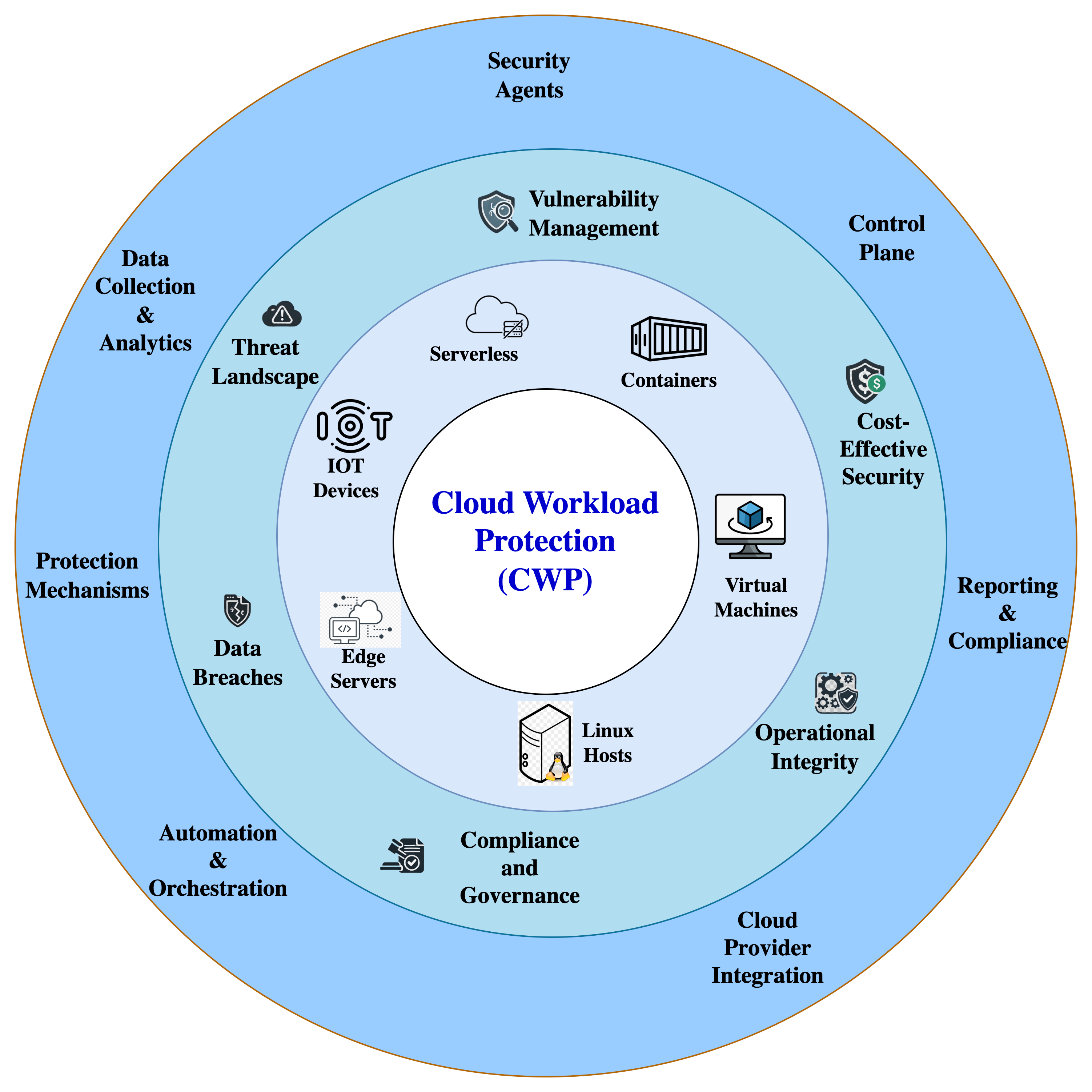 The Benefits of CWP
The Benefits of CWP
Investing in Cloud Workload Safety offers a number of essential advantages:
- Superior risk detection: CWP options use superior expertise to acknowledge and reply to potential threats in real-time, and supply a proactive protection technique that adapts to rising threats.
- Automated safety updates: CWP instruments repeatedly replace themselves to sort out latest vulnerabilities, decreasing the handbook workload on IT groups and making certain uninterrupted safety.
- Centralized administration: A unified overview of safety throughout all cloud workloads optimizes administration and enhances oversight by way of clever insights and alerts.
- Flexibility and scalability: As cloud environments develop, CWP options can adapt accordingly, offering robust safety with out compromising efficiency.
Compliance and CWP
Regulatory compliance is a key motivation for implementing CWP. Rules equivalent to GDPR, HIPAA, and PCI-DSS implement stringent safety standards to guard delicate info. CWP instruments assist in fulfilling these necessities with:
- Knowledge encryption: Guaranteeing that delicate information is encrypted each at relaxation and when transmitted.
- Steady monitoring: Sustaining fixed surveillance of workloads, rapidly figuring out and addressing potential safety considerations.
- Thorough auditing: Delivering complete information and logs of knowledge entry and modifications for compliance reporting.
Distinguishing CWP from Utility Safety
Whereas CWP and Utility Safety are each important, they deal with completely different parts.
- CWP encompasses the whole thing of the cloud surroundings, together with infrastructure, digital machines, and information. CWP goals to safe all elements of the cloud workload, outlining a complete safety technique.
- Utility Safety concentrates on securing particular person purposes in opposition to vulnerabilities and assaults. This side is extra involved with defending the code and capabilities of the purposes themselves.
Primarily, CWP is like securing your entire construction, whereas Utility Safety pertains to locking and safeguarding every particular person room inside that construction.
Instruments and Applied sciences for CWP
Quite a lot of instruments and applied sciences can ship efficient CWP. Listed below are some notable examples from main cloud platforms:
IBM Cloud
- IBM Safety QRadar: Provides superior safety analytics and risk intelligence
- IBM Cloud Hyper Defend: Supplies refined information encryption and safe key administration
- IBM Safety and Compliance Middle (SCC): Provides complete instruments to handle safety and compliance throughout cloud environments, integrating risk intelligence, threat administration, and compliance monitoring to reinforce the general safety posture
Google Cloud
- Google Cloud Safety Command Middle: Supplies insights into the cloud surroundings and identifies potential threats
- Chronicle Safety: Analyzes massive volumes of safety information to swiftly detect and reply to threats
Microsoft Azure
- Azure Safety Middle: Provides unified safety administration and superior risk safety
- Microsoft Sentinel: A cloud-native SIEM resolution for clever safety analytics and risk detection
Amazon Internet Providers (AWS)
- AWS Protect: Supplies safety in opposition to DDoS assaults and enhances total safety
- AWS GuardDuty: Screens for malicious actions and unauthorized actions
Function of CSPM and CWP in Fashionable Cloud Environments
Cloud Safety Posture Administration (CSPM) and CWP are complementary in nature however deal with completely different areas. CSPM goals to enhance the general safety posture of the cloud surroundings by figuring out configuration errors and compliance points. CWP focuses particularly on the safety of the workloads themselves, encompassing purposes, information, and infrastructure.
Conclusion
It is turning into more and more essential to deal with defending their workloads. This implies holding delicate information protected, sustaining regulatory compliance, and ensuring crucial purposes run easily. By embracing CWP and mixing it with different important instruments and practices, corporations can construct a robust and safe cloud surroundings that stands as much as at this time’s cyber threats.

